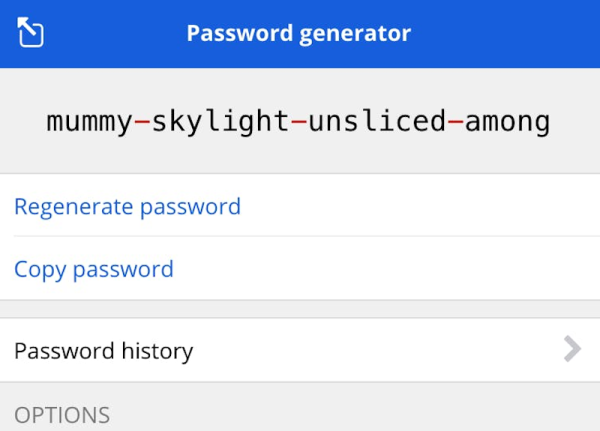
The ubiquity of ransomware continues, this time with The Guardian announcing they were partially shut down from an attack. Staff are working from home as the incident is being investigated and data is recovered. Publishing seems to be continuing, and the print paper ran as expected.
There have been a couple reports published recently on how ransomware and other malware is distributed, the first being a public service announcement from the FBI, detailing what might be a blindly obvious attack vector — search engine advertising. A bad actor picks a company or common search term, pays for placement on a search engine, and then builds a fake web site that looks legitimate. For bonus points, this uses a typosquatted domain, like adobe[dot]cm or a punycode domain that looks even closer to the real thing.
The FBI has a trio of recommendations, one of which I whole-heartedly agree with. Their first suggestion is to inspect links before clicking them, which is great, except for the punycode attack. In fact, there are enough lookalike glyphs to make this essentially useless. Second is to type in URLs directly rather than using a search engine to find a company’s site. This is great so long as you know the URL and don’t make a typo. But honestly, haven’t we all accidentally ended up at website[dot]co by doing this? Their last recommendation is the good one, and that is to run a high-quality ad-blocker for security. Just remember to selectively disable blocking for websites you want to support. (Like Hackaday!) Continue reading “This Week In Security: Adblock For Security, ProxyNotShell Lives, And CVSS 10 To Not Worry About”