Despite the popularity of social media, for communication that actually matters, e-mail reigns supreme. Crucial to the smooth operation of businesses worldwide, it’s prized for its reliability. Google is one of the world’s largest e-mail providers, both with its consumer-targeted Gmail product as well as G Suite for business customers [Jeffrey Paul] is a user of the latter, and was surprised to find that URLs in incoming emails were being modified by the service when fetched via the Internet Message Access Protocol (IMAP) used by external email readers.
This change appears to make it impossible for IMAP users to see the original email without logging into the web interface, it breaks verification of the cryptographic signatures, and it came as a surprise.
Security Matters
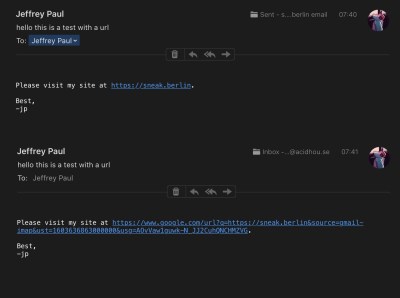
For a subset of users, it appears Google is modifying URLs in the body of emails to instead go through their own link-checking and redirect service. This involves actually editing the body of the email before it reaches the user. This means that even those using external clients to fetch email over IMAP are affected, with no way to access the original raw email they were sent.
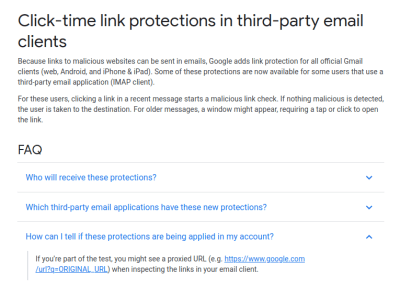
The security implications are serious enough that many doubted the initial story, suspecting that the editing was only happening within the Gmail app or through the web client. However, a source claiming to work for Google confirmed that the new feature is being rolled out to G Suite customers, and can be switched off if so desired. Reaching out to Google for comment, we were directed to their help page on the topic.
 The stated aim is to prevent phishing, with Google’s redirect service including a link checker to warn users who are traveling to potentially dangerous sites. For many though, this explanation doesn’t pass muster. Forcing users to head to a Google server to view the original URL they were sent is to many an egregious breach of privacy, and a security concern to boot. It allows the search giant to further extend its tendrils of click tracking into even private email conversations. For some, the implications are worse. Cryptographically signed messages, such as those using PGP or GPG, are broken by the tool; as the content of the email body is modified in the process, the message no longer checks out with respect to the original signature. Of course, this is the value of signing your messages — it becomes much easier to detect such alterations between what was sent and what was received.
The stated aim is to prevent phishing, with Google’s redirect service including a link checker to warn users who are traveling to potentially dangerous sites. For many though, this explanation doesn’t pass muster. Forcing users to head to a Google server to view the original URL they were sent is to many an egregious breach of privacy, and a security concern to boot. It allows the search giant to further extend its tendrils of click tracking into even private email conversations. For some, the implications are worse. Cryptographically signed messages, such as those using PGP or GPG, are broken by the tool; as the content of the email body is modified in the process, the message no longer checks out with respect to the original signature. Of course, this is the value of signing your messages — it becomes much easier to detect such alterations between what was sent and what was received.
Inadequate Disclosure
Understandably, many were up in arms that the company would implement such a measure with no consultation or warning ahead of time. The content of an email is sacrosanct, in many respects, and tampering with it in any form will always be condemned by the security conscious. If the feature is a choice for the user, and can be turned off at will, then it’s a useful tool for those that want it. But this discovery was a surprise to many, making it hard to believe it was adequately disclosed before roll-out. The question unfolded in the FAQ screenshot above hints at this being part of Google’s A/B test and not applied to all accounts. Features being tested on your email account should be disclosed yet they are not.
Protecting innocent users against phishing attacks is a laudable aim, and we can imagine many business owners enabling such a feature to avoid phishing attacks. It’s another case where privacy is willingly traded for the idea of security. While the uproar is limited due to the specific nature of the implementation thus far, we would expect further desertion of Google’s email services by the tech savvy if such practices were to spread to the mainstream Gmail product. Regardless of what happens next, it’s important to remember that the email you read may not be the one you were sent, and act accordingly.
Update 30/10/2020: It has since come to light that for G Suite users with Advanced Protection enabled, it may not be possible to disable this feature at all.
















Given emails have legal tender, I wonder how this will affect legal cases. The email was tampered with, and if they start modifying the links, there’s no guarantee other words won’t be modified (e.g. to comply with censorship laws), leaving reasonable doubt about the integrity of the message in a legal context. Can a real lawyer pitch in here?
Messages with broken electronic signatures are null and void in most countries.
Yeah, but what about messages that have no signature at all, or none that the user is aware of? I’ve made plans over Facebook messenger about what I’m supposed to do and how much I’m getting paid for it, and I never PGPed those messages.
I’m sure plenty of non-lawers like me think any verbal agreement you can maybe prove later, in any medium, is probably good enough for a $100 commission.
What makes you think they have legal tender?
Court cases often have to go to a great deal of effort to prove the integrity of the email message. “I didn’t send that, I musta been hacked, OMG” is a common defence.
People get important documents notarized and witnessed for the same reason, that doesn’t mean a paper signature doesn’t carry legal weight, just that lots of things can be faked.
(INAL)
That’d be quite a popular email system that makes communication through it inadmissible in court.
“Protecting innocent users against phishing attacks is a laudable aim, and we can imagine many business owners enabling such a feature to avoid phishing attacks. It’s another case where privacy is willingly traded for the idea of security. ”
Sounds like a feature that should be on the customers end. And the “willing” part is rather denied by the article itself.
I recently wrote a spamassassin rule that matched ‘ a href=other.domain>some.domain’ to catch phishing and such.
The effort was for nothing, because Ihad to find out, that many senders rewrote urls and redirect to their… … …anti-phishing resolution.
m(
You can’t fix stupid. You can’t persuade people not to click on phishing bate.
Google making it an opt-out feature instead of opt-in is again an example of their abusive behavior. The reason is that the feature is primarily intended for click tracking instead of user security.
Incidentally Alphabet is being sued now in the US for the abuse of their dominant market position.
https://www.bbc.com/news/business-54619148
But… But, it is so easy to make the opt-out functionality difficult for the end user to implement!
Much easier than trying to get them to opt-in!
B^)
Facebook does this is various different ways depending on the link destination.
Most of the time Facebook adds a [ sometimes very long ] tracking identifier. Sometimes they add a redirect prefix. They often remove the actual link text from the post by default depending on whether it’s before it after your post and unless it’s edited after their script reads it. You can always copy the link as text or manually replace the %20’s ect.
^in
Facebook sucks!
I think the privacy argument is a bit overzealous. I agree it’s an invasion of privacy but uh, that’s nothing new with gmail. If I wanted my gmail to not be read by google I would either
A. Not use gmail.
B. Encrypt all my emails before sending them.
I think it’s fairly well known that Google (and it’s tech brothers) give 0 f’s about your privacy and if they could would install a camera with GPS literally stapled to your forhead with video streaming enabled 24/7.
-Sent from my gmail account.
They already did. Cellphone.
Yeah, it’s a bad move. I would guess that some big company somewhere came to Google and said, we’d love to move to gSuite, but we’re gonna have to continue using Outlook on our desktops. Can you do phishing protection for Outlook users?
It’s mentioned in passing in the article, but so far this is only for paid G Suite users, not normal users with an @gmail.com address.
Great G Suite user screwing.
Charge them for:
* “just” forwarding email
* blocking email (deciding what is “spam”)
* modify email for better click tracking
Actually it says that all users of official gmail clients (web, Android, iPhone & iPad) already receive this “click-time link protection”. The news is that they’re extending that function (feature?) to some people using certain IMAP clients (“Apple Mail, Outlook, and some prevalent Android email clients”). In fact, I read nothing about paid vs unpaid or commercial vs consumer usage, except as inferred from the use of email clients.
Can’t actually tell for sure
“some big company somewhere came to Google and said, we’d love to move to gSuite, but we’re gonna have to continue using Outlook on our desktops”
You should probably be aware that Google is terminating G-suite at the end of all current contracts, and forcing everyone into the far more expensive “google workspace”
Everyone I know is working on migrating directly to o365 since last week when it was announced. Absolutely no one is interested in moving to Google, having a 10x per month bill, and getting less features out of it.
O365? “Ten times boost in spam and malware, for 10x(?) less money.”
Microsoft implemented a similar feature, known as SafeLinks, several years ago. There is a way to disable it by contacting MS support. See https://www.askvg.com/why-outlook-adding-safelinks-protection-outlook-com-to-all-urls-in-your-emails-and-how-to-disable-it/
Came to say that m$ has been doing this for years.
If they are now modifying messages does that now mean that google are giving up their Common carrier legal status. Or at least weakening it.
It would be the equivalent of the postal services modifying the text of every postcard.
So put the link in a password protected, compressed text file.
The password is conveyed separately… Boom, quick and dirty 2nd factor.
Gmail treats password protected archives as “viruses”. As a test I changed the name of an EXE file, put it in a password protected ZIP then into a password protected RAR and tried to send it through gmail. Gmail still “detected” it as a “potential virus”, despite it being some completely innocuous little windows exe file.
Innocent windows exe file. Someone should invent one of those.
Yes, because anything they cannot see and spy on is a virus
1000+ upvote.
I just renamed file to .zi_ and that was enough, without password protection. Also – password protected archives still have ‘open’ file directory, as far as I remember.
But that was some years back
Just read emails as intended: as plain text. There is no way you can click on a link that isn’t there to be clicked.
And emails that are pure HTML should be automatically send back to the originator as plain text so they see the utter garbage they are inflicting onto their audience.
I’d like to agree with you but many large organizations with the resources to do better send multi-part MIME with only an HTML part, or a text part that says “Click here to view this message properly”, or worse an HTML part that’s unparsable by html2text.
Gmail has a “signature” feature, whereby a person can create a closing statement and set it up to appear at the bottom of all emails that they send. Originally these could consist of text or graphics or both. Now, although the text remains, the graphics have been removed. Why?
Because anybody that feels the need to have graphics under every single email they send should be taken behind the shed and given a beating?
A pox on their houses for wasting bytes and making it impossible to find that email with the attachment you actually need in the sea of emails with *company logo* attached to the bottom.
Hmmm… interesting… this may be why I see a lot of broken DKIM signatures coming from g00gle lately, all citing the email body has been changed. And those emails would be delivered to my server over SMTP. Worth some further scrutiny!
This also impacts use of the DKIM, a little known email signing process to ensure the sender mail does not get mangled in transit by malicious 3rd parties. In this case google qualifies as one of those parties.
https://en.wikipedia.org/wiki/DomainKeys_Identified_Mail
DKIM can sign the body, or the header or both. In this case if one implements body or both, then it will fail the check and unfortunately I have a rule on my email server that IF a sender chooses to implement email security, and if that security is DKIM and if that message fails the verify, it gets deleted immediately as its untrustworthy. The sender would be unaware of this unless they use DMARC to get feedback. This has prevented a lot of issues at my agency but also created an entire new set. I found like other commenters that so many people change the body of the message for some reason. The only solution will be to have end to end encryption if companies like Google can’t get this right. I wonder if Google still changes such signed messages.. Its in a header, perhaps if they see an untrusted sender they “fix the link” but if they see a signed message they skip it? I don’t know and it would take testing..
DKIM is not handled by your email client is it? Then it is worthless because outside your control.
Also, DKIM is managed by the server themselves, Google could mangle the outgoing links and sign afterwards.
Finally, it appears they mangle the URLs on received emails, so DKIM is verified by Google before it even reaches your inbox.
I posted a comment here critical of dontbeevilcorp, suggesting that they were likely to suppress links and information that they don’t support, but are not illegal, and neither of those made it past the system here. Why is that?
That’s not all they’re meddling in…
GOOGLE LAUNCHES MAN IN THE MIDDLE ATTACK ON THEIR OWN CUSTOMERS
There, I fixed the title for you.
Well, they can’t really usurp all of ones privacy in one go, not yet anyway, so instead they find a likely excuse that will pass the smell test for for the uninformed, namely security, and a little at a time we arrive at “nobody is forcing you to use the internet, or literally anything attached to it”.
We’re geeks. We create our own internet.
Lol, I did say ‘uninformed’. Geeks, makers, builders, programmers, etc, are generally not the uninformed. The masses, consumers of ‘stuff’, en-masse, are largely uniformed as to the extent of what, where and how their information is gathered and to what extent it is shared. To prove that, poll your average consumer and pull up any terms and service agreement for Any piece of software, and ask them to explain what they are reading. This is the foundation Google, and most others, are built on. This article here is but a brick in the wall built on top of a flawed foundation. The informed do have a responsibility as well, even the geeks. I realize the reply had a tinge of humor, however I really dislike the thought of ‘how did we get here’. This question off goes unanswered, not limited to technology.
What I want to see is something that 100% blocks Google AMP. Let’s see browser addons for all the browsers, desktop and mobile, that automatically remove all the AMP crap and go to the unfiltered site.
Just quit using Google then, there are other search engines, better than Google by the way. Qwant to name one.
Convenience over simplicity and protecting the dumb from themselves, instead of providing actual security… it’s a shame people keep throwing their money and data at services like this.
Google doing shenanigans? Imagine my surprise.
Doesn’t Microsoft do the same with their Safelink rubbish?
They also obfuscate the originators IP’s now to ensure the spammers/scammers privacy. It’s all for your benefit.
I thought the PGP messages can not be read by anyone else then the owner of the private key. So, I reckon that PGP messages will not be read nor altered by any mail server.
Please give this company a Buddhist funeral high up in the mountains. Divide up the scraps to the vultures and reincarnate it with restrictions.
Don’t be evil.
So I typed the “Don’t be evil” in some search engine. (Not google of course)
One of the first links that popped up was:
https://www.cnbc.com/2020/01/02/google-abandoned-its-dont-be-evil-mantra-former-exec-says.html
Our company uses e-mail for sending legally binding contracts and everyone knows hơw much it costs to hire a lawyer who crafts these literary masterpieces.
For years we have used e-mail headers as a part of our security / authenticity order verification system. Tampering with ANY communication is plain wrong especially when trust between companies built up over years is broken by some poorly conceived idea.
This ís an ơwn goal for Google, for no longer can their ơwn users e-mails be trusted. A pox on your house, Google.
I’m quite surprised this is such a big security concern for the author and fellow commentators. It obviously is a bad thing, but:
1. Google already scans all of your emails anyway, including links, check e.g. your “shopping” tab or automatic calendar events that appear when you book a flight.
2. This is a private company, so I guess they can just do what they want to do, because you agreed to it. People treat it like some kind of public service that must obey their rules. I understand some rules are universal (like post office not opening letters), but you got what you signed up to, and everybody knows it’ll be only worse with Google. Yet they still use it.
I don’t think this is a big forward step in the direction they are going. I don’t like it at all, but they do massive amount of much worse things with your emails already, and anti-phishing thing actually makes some good for all of our grandmas and not tech-savvy people.
As someone who works in email marketing, I think Google’s explanation is somewhat of a blind. Yes, there may be some secondary advantage to preventing phishing, but having click metics is vital to training the gMail spam filter, and this is the real reason they’re rewriting the links. (With IMAP, there’s no way to know if the user clicks on a link without rewriting the link.) Google probably is trying not to give any official hint at all at the workings of their spam filter, so they are going with some other reason as the official explanation.
That is a man in the middle attack if you ask me. Were is the privacy if any. Google repetitively has taken such actions.
They were using our emails to provide targeted advertisement.
They have a buch of ML algorithms to categorize our emails.
Smart emails feature for auto completion and what not.
Google AMP URLs: TL;DR: Today, we’re adding a feature to the AMP integration in Google Search that allows users to access, copy, and share the canonical URL of an AMP document. But before diving deeper into the news, let’s take a step back to elaborate more on URLs in the AMP world and how they relate to the speed benefits of AMP.
All those features are not derived of an end user needs rather of their need to track us better, and sell our info to gain capital.
IHMO we just need a better email service, which is end to end encrypted by default. Or we need to all get into using Gmail with GPG encryption. Both options are a tall order, but IMHO they are soemthing we need.
And yes, security is critical, and spam and vicious and malicious attacks are a daily part of our life, but we cannot sacrifice our privacy just to get slightly better spam categorization. If anything, Google should not know which sites I visit and why. Internet providers, and companies like google have too much visibility into our actions. They should not be able to read our emails or track the sites we visit or the products we buy or the links we share.