It’s long been common wisdom that one of the safest places to keep your cryptocurrency holdings is in a hardware wallet. These are small, portable devices that encrypt your keys and offer a bit more peace of mind than holding your coins in a soft or web wallet.
But of course, as we know, nothing is totally secure.
And we were reminded of this fact by Kraken Security Labs, when they showed us how they bypassed all of the safeguards in a popular wallet, the Trezor, to dump and decrypt it’s seed.
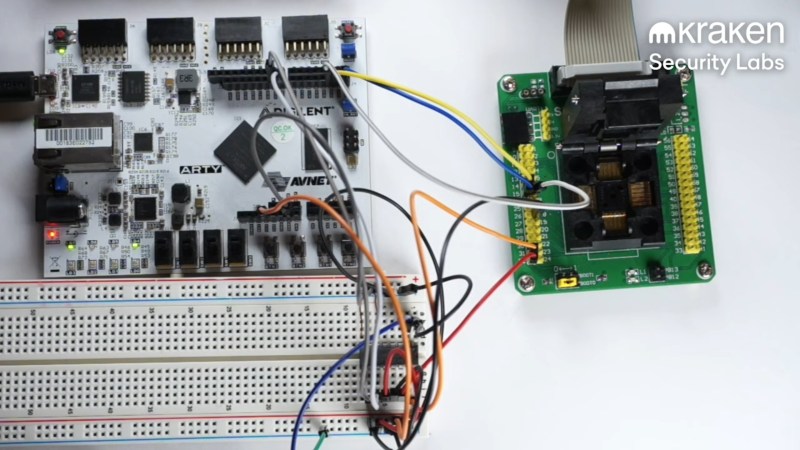
It’s worth noting that the hack does require physical access to the wallet — albeit only about fifteen minutes worth. And by “physical access” we mean that the hack leaves the device thoroughly mutilated. The Kraken team started by desoldering the heart of the wallet, a STM32 processor. They then dropped it into a socket on an interface board, and got to glitching.
The hack relies on an attack known as voltage glitching. Essentially, at a precisely-timed moment during the device’s boot sequence, the supply voltage is fluctuated. This enables the chip’s factory bootloader, which can read out the contents of it’s onboard flash memory. The memory is read-protected, but can be accessed 256 bytes at a time through a second voltage glitch. Neither of these attacks work 100% of the time, so if the device fails to boot or the memory remains locked, the FPGA performing the attacks simply tries again. After enough iterations, the Kraken team was able to fully dump the chip’s flash memory.
There’s one more hurdle here — the memory dump is encrypted. Enter brute forcing. Trezor devices allow a maximum pin code length of nine digits, but if you assume the average user’s pin is only four digits then it can be guessed via an automated script in a matter of minutes. Even a longer pin can be worked out in a matter of days or weeks — certainly within the realm of possibility. This yields the seed, which could then be entered into a new hardware wallet to effectively steal any cryptocurrency assets that lived on the original device.
So, aside from some cool hardware hacking techniques, what can we learn from the Kraken Security Lab’s work? First up, for any designers out there, the STM32 is not suitable for high-security applications. For all the end users, this doesn’t mean you need to trash your Trezor (even though this isn’t the first wallet hack we’ve seen). It does mean that you should keep it away from other people, and that you should enable the BIP39 passphrase, which Kraken says can protect against the attack. Perhaps most importantly, this serves to remind us all that nothing is 100% secure.















This article is a year late. You guys using IE or something?
You know you can submit a tip if you think something might be of interest, right?
Chrome on Samsung S9 Plus
15 minutes?? Just????😂😂😂😂😂😂
Guy did it 10 seconds….. Using a shotgun and a threat!
Here’s to a better year.
Funnily enough things like this make it more likely I’d “trust” one… on the “what happens WHEN it breaks??” level.
“Remember to drink your Ovaltine” ?
I would never let anyone have physical access of my gold, at the value of $2,000 per ounce…likewise, I would never let anyone have physical access to my Bitcoin hardware wallet. At any rate,s beit would much harder for a thief to cash in my Bitcoin than to cash in my gold.
Aren’t you supposed to have separate secure element on such devices? If I read this article correctly Trezor doesn’t use secure element (like Ledger does) but stores keys in microcontroller’s flash where only protection is read disable fuse which is easily bypassed by voltage glitching. If so that device is not much suitable for crypto currency storage than Arduino.
Yes you are. Or to use an MCU that is intended for this application instead of a general purpose one.
Which model do you suggest ????
It’s not that simple. Those “secure” elements are not Open Source and implement security by obscurity. You have to sign NDA to get access to information required for development.
The creators of Trezor decided to create an Open Source wallet, knowing that it’s still useful because the vast majority of attacks are via malware, not physical. Besides they allow users to choose an extra passphrase to protect the wallet. The passphrase makes sense regardless of the hardware because ultimately any hardware could have bugs.
You may prefer a different security model but their model is still reasonable.
Nice, so it looks like all STM32 are cracked now.
F0 was cracked by Marc Schink & Johannes Obermaier https://www.aisec.fraunhofer.de/en/FirmwareProtection.html
Same pair did F1 last year https://blog.zapb.de/stm32f1-exceptional-failure/
And now we have confirmed working attack on F2 and F4.
It would be interesting to know if there are attacks that work on the f7 and h7 chips because if I remember right some of them can be encrypted.
I think the key bit of information, which is unforuntately missing from the summary, is if you password is 9 digits how long will it take to break?
If 4 digits takes 2mins, does 5 digits take 20mins? Then I think 9 minutes would be just under 14 days. (2minutes * 10^4).
Because with a hardware wallet the idea is well if you notice it missing you know you’re in trouble. Two weeks is probably the minimum period one can be expected to reasonably notice it is missing. In practice most people will have them unsupervised for even longer.
I think for most people, the biggest risk is forgetting where they’ve put their wallet/hash/etc, or forgetting the passphrase/password/pin. It’s a weird part of all of this — centralized currency control means you have professionals at a bank or other institution worrying about the ultimate security of your accounts. With cryptocurrency the user is responsible for their own security choices.
“With cryptocurrency the user is responsible for their own security choices.”
Oh well now, that’s going to work out well.
At least we don’t have to pay for bailouts.
This means you can use the services of one that can crack into your wallet if you lose your password………yes?
Interesting work.
A year a ago there was another article about breaking the read out protection of STM32 MCUs:
https://hackaday.com/2020/03/24/breaking-into-a-secure-facility-stm32-flash/
Would that work for the F2 and F4 series used in the Trezor?
Wow
Safepal wallet would self destruction if u tried this. Love it so far. Only downside is it’s not open source. Always a downside tho.
This attack vector can be mitigated by using a passphrase in Trezor. Passphrases are apart of the seed itself and hence can’t be bypassed this way.
Also, this was posted almost a year ago by Kraken, why the repost now?
Papper wallet and seed in your mind
Never use a paper wallet. Or you are trusting paper wallet generator and your printer?
Well I was recently hacked and they got 1.2 million dollars. So how do I get it back or hack it back.
Depends. Did you have it online or in an offline wallet? Do you know who hacked it? If it was in an offline wallet, was it hacked while plugged in or away from a communication device? Details will help to answer.
We find this paragraph:
“There’s one more hurdle here — the memory dump is encrypted. Enter brute forcing. Trezor devices allow a maximum pin code length of nine digits, but if you assume the average user’s pin is only four digits then it can be guessed via an automated script in a matter of minutes. Even a longer pin can be worked out in a matter of days or weeks — certainly within the realm of possibility. This yields the seed, which could then be entered into a new hardware wallet to effectively steal any cryptocurrency assets that lived on the original device.”
Where in we find this: “This yields the seed, which could then be entered into a new hardware wallet to effectively steal any cryptocurrency assets that lived on the original device.”
MY QUESTION: Is “the seed” the list of 24 words required for recovery? And then, Is the following accurate:
“,,, which could then be entered into a new hardware wallet” — ?
Put another way, presuming it’s a hardware wallet issue and not a theft issue, is the list of recovery words plus another hardware wallet all that is needed to recover your cryptos? (
Words plus ANY wallet (even software)
How can I steal my crypto credits back after being scammed into transferring the money from one coinbase wallet Into a codex crypto wallet ?
All communication with the scammers has stopped yet my account balance appears to be increasing on a daily basis .