Among security professionals, a “drop box” is a device that can be covertly installed at a target location and phone home over the Internet, providing a back door into what might be an otherwise secure network. We’ve seen both commercial and DIY versions of this concept, and as you might expect, one of the main goals is to make the device look as inconspicuous as possible. Which is why [Walker] is hoping to build one into a standard USB wall charger.
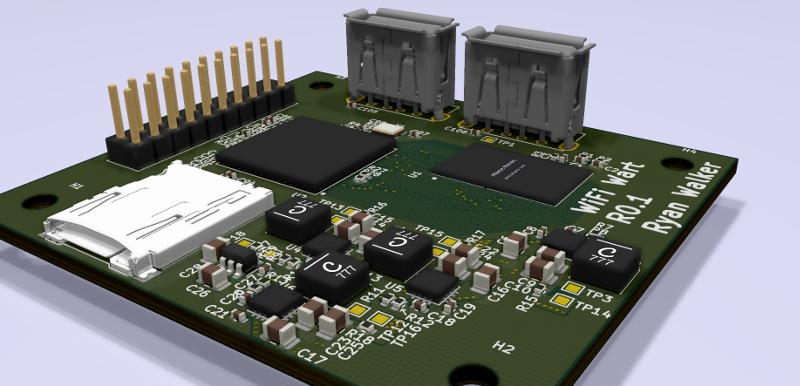
This project is still in the early stages, but we like what we see so far. [Walker] aims to make this a 100% free and open source device, starting from the tools he’s using to produce the CAD files all the way up to the firmware the final hardware will run. With none of the currently available single-board computers (SBCs) meeting his list of requirements, the first step is to build a miniature Linux machine that’s got enough processing power to run useful security tools locally. Obviously such a board would be of great interest to the larger hacker and maker community.

So far, [Walker] has decided on his primary components and is working on a larger development board before really going all-in on the miniaturization process. As of right now he’s planning on using the Allwinner A33 to power the board, a sub-$10 USD chipset most commonly seen in low-cost Android tablets.
The A33 boasts a quad-core Cortex-A7 clocked at 1.2 GHz, and offers USB, I2C, and SPI interfaces for expansion. It will be paired with 1 GB of DDR3 RAM, and an SD card to hold the operating system. Naturally a device like this will need WiFi, but until [Walker] can decide on which chip to use, the plan is to just use a USB wireless adapter. The Realtek RTL8188CUS is a strong contender, as the fact that it comes in both USB and module versions should make its eventual integration seamless.
Even if you’re not interested in the idea of hiding security appliances inside of everyday objects, this project is a fascinating glimpse into the process of creating your own custom Linux board. Whether you’re looking to put into a wall wart or a drone, it’s pretty incredible to think we’ve reached the point where an individual can spin up their own miniature SBC.















Finally someone thought of this! With a nice 3D printed black enclosure.
And tor proxy to penetrate NAT.
better use something like DNS tunneling, Tor would stand out like a sore thumb in most security conscious organizations
Should combine it with power line internet for an almost completely unmonitored channel for data exfiltration.
Certainly not the first time someone has hidden something malicious in a wall wart. Think Samy Kamkar with his KeySweeper back in 2015. This is just a slightly more sophisticated attack device.
Really cool, I look forward to seeing the rest of the series. This is not something I’ve learned much about, though that blog post from the person who wrote the massive $1 mcu comparison suggesting more folks should try this kind of build piqued my interest. While the assumption that Android support means good mainline Linux support isn’t always true, I bet the linux-sunxi community (which works on allwinner stuff) probably has the a33 sorted since it’s popular and older. Might even be able to boot Debian on it.
Pretty sure Debian/armbian works really well with it ;)
Sad to see the a33 as choice though. AllWinner has much cheaper chips with built in ram. Think. H3 etc … And Ethernet Mac which could be colll for an alt. Pie version. ..
I am vaguely aware that stuff like this has a use-case other than malicious intent, but could someone give me a bit more detail about what that use-case is? Is it just to test how to avoid this type of attack from a truly malicious actor?
For me, the knowledge that such devices can be hidden in “everday” devices and easily supplied on Ali-Express (the day after tomorrow?), is reason enough for me.
Correct! You nail it! Stick to your original phone vendor provided charger!
Well, if I knew of any cheap Chinese phone charger that would come with a Linux board inside, I’d probably buy a dozen to take out the SBC and play with it.
Exactly – Its a reminder to never trust the network, even an internal one.
People are paid to penetrate networks, basically an OK from high up in the company is given (to avoid jail time). And after finding flaws (if any) in the security, a report is generated usually listing the good, the bad and the ugly, ideally with a timeline of suggested ways to stop them from ever doing what they did again (updated software, processes and procedures mostly, patch cycles, …). And companies do this to have a slightly higher security fence than everyone else. Basically they kick the wheels of their car a bit before someone who is not being paid by the company does so and walks away with their crown jewels. Sometimes the local people are informed beforehand to shore up the defences, processes and processes, and sometimes they are not. But the approved penetration test does not typically involve any downtime or damage to systems to mask that any event took place, which would not be necessarily be the case in a malicious event.
Some of it could be dedicated LANS or VLANS (production, system management, backup, development, test, finance, human resources), multiple internal firewalls to restrict access to higher value data. An onion layered type approach. Sometimes physical access to a zone/area is required for access to certain data types on certain VLANS that are only tagged to some switches and automatically flagged if modified. So identification badges, pin codes, passwords, and VPN access from the Intranet to one more more higher secure Intranet zones. Guest/visitor WiFi networks or physical RJ45 access that is fully air gaped from internal networks. Multiple layered secure zones and logging on everything. Basically the fundamental three A’s of security, Access control, Authorisation and Audit everything. Most of security is just basic common sense, but ….
Anyhow toys like the above are just tool, and tools are never good or evil. e.g. a hammer can kill or create.
Yes. And it´s even cheaper to let the admins step up the security by falsely letting them believe a security audit will occur at a given date. They suddenly feel very involved with security and process, and patch up wide open doors that were neglected before, and it costs nothing.
Traditionally an internal person improving security will only apply what they know and have experienced. Fresh eyes looking at the big picture and have intimidate knowledge of high to medium levels of security in many organisations can bring insights and improvements that may not always be obvious to someone looking at the problems for years and not seeing any problems usually because – “That is how it has always been done”. And an internal person looking to improve security there is typically no money available for such work which does not directly generate additional profit. It was traditionally seen as a loss, where as if there is an external report which cost additional funds, that needs to be acted upon (crazy though it sounds).
The use case is almost entirely malicious. You could imagine other use cases for a tiny computer, but few that would not be adequately served by something in a slightly larger form factor.
Easy peasy. WiFi thermostat sensor… WiFi garage door opener… WiFi security system controller… Soil moisture monitor… Convert your ir remotes to WiFi….
wireless camera with mic…
an ultra-miniature MPU board a lot smaller than a raspberry pi Model 3 with wifi support that can boot Linux has many potential embedded uses.
Would be interesting to have this connect to “powerline ethernet” systems. You’d have instant network access by just plugging it in, no wifi required.
Powerline ethernet willl usually not make it past the first transformer encountered. You would have to be in or very near the targeted location to use that.
maybe PoE is meant
Nope, Ethernet over Powerline is a thing. But as the responder indicated, the signalling doesn’t manage to cross transformers (and of course, can’t cross phases either!) That said, it might be a nice way to communicate from a location deep inside a facility to somewhere closer to the edge, where wireless wouldn’t be a good option. LoRa is an interesting alternative, of course.
LoRa needs a bigger antenna.
Powerline ethernet uses the powerlines as a way to transmit and receive the data. Transformers (and as suggested by the manufacturers), even breakers may interfere with how powerline ethernet operates.
However, his example might be a bit trivial since powerline ethernet adapters usually come in pairs, and you would need to have another adapter where the server is anyway. It won’t give you any benefit as compared to running an ethernet cable straight to the server, and at this point in a security breach, physical access is already at hand.
*puts evil hat on, for 0.99 seconds*
You know what would be even more evil. If it uses LORA to listen only, and disables all WiFi until it receives a special command to enable WiFi. Passive until activated remotely.
*takes evil hat off fast before it gets too comfortable*
You could go super simple and just use some kind of 433mhz OOK (or the non-EU/UK equivalent), and tie it to a garage remote
Or keyfob ;)
The nice thing about LORA hardware is that you can dial down the bit rate to nothing and get km/miles or range.
of range (r near f on keyboard)
rm -rf
Ahh I hadn’t realised it was quite that far reaching! Yes thats significantly better than the typical 433 setup!
Long as the building in question isn’t acting like a Faraday cage.
In theory you could have a LORA RX sensitivity of nearly -150 dBm (~ -147dBm with a shared antenna for Rx with Tx), if you make the spreading factor high enough (SF12), drop the bandwidth low enough (7.8kHz), and use the lowest centre frequency possible (which would be illegal). Then your equivalent bitrate would be about ~11 (coding rate 4/5) bps to ~18 bps (coding rate 4/8). There is a LORA modulation calculator tool for windows available from the Semtech (owners of the patents on LORA) website, but it is burred well. It is nearly like Semtech do not want people to use it.
sorry forgot my point, which was that cage needs to be good and attenuate the signal very well.
Just did this to wake up a remote solar rig for phone home, ha!
This is just a first concept and (not yet) optimized for small PCB size, but does it have much chance of getting much smaller then for example the NanoPi Neo?
https://duckduckgo.com/?q=nanopi+neo&t=hd&va=u&iax=images&ia=images
http://wiki.friendlyelec.com/wiki/index.php/NanoPi_NEO
Looking a bit closer at the Neo…
If you take of those friendly big extension connectors, mounting holes and the chuncky real RJ-45 connector it’s a pretty damn small piece of hardware.
The NanoPi Neo Air is what you are lookign for, I think. https://wiki.friendlyarm.com/wiki/index.php/NanoPi_NEO_Air
I’m moving to a two board design that will stack vertically. One with the mains -> 5V + all SMPS’s, the other with the AP, RAM, EMMC and radios. I think stacking I should be able to get it into a decent form factor.
Or maybe design something with an OSD335x? The chip size limits this to 2.7 x 2.7 cm, though.
The Vocore2 is 2.54 x 2.54 cm and still has lots of space on the PCB.
I have also seen pretty small designs using the old i.MX23/i.MX28.
How about a similar board in a power bank/USB battery enclosure? I’d happily swap out an 18650 cell for a single-board computer that I could use to read USB sticks into my iPhone while on the go.
TP-Link make some really good travel routers, some of which have USB and batteries integrated. I’d imagine one of these could be used to spin up a share to ingest data into a mobile device. They’re really versatile things, and worth picking up.
I used a TP-Link TL-MR3020 to do exactly that with one of the build it yourself USB battery packs with a pair of 18650’s.
https://hackaday.com/2019/01/24/solar-powered-openwrt-router-for-mobile-privacy/
+1
Grab one of the GL.Inet travel routers, e.g. the Slate AR750S – 128MB RAM, 128MB flash, external USB as well as an internal USB header, as well as I2C and UART, plus a uSD slot. Runs mainline OpenWrt, so almost infinitely customisable.
Those GLINET boxes are sooo under appreciated. You’d be surprised what magic you can bake with one of those and the OpenWRT Image build kit…
I got a “DSTIKE WiFi Deauther Power Bank DIY Kit” to play with and found that I could also mount a RPI 0w inside by removing 2 of the 7 18650 cells so now its twice the fun. I’m sure just about any 18650 powerbank kit would fit most sbc’s with a few batteries left out.
Problem is if you leave a phone charger or powerbank unattended for more then a shift at most workplaces it will probably go home with someone, better to put it in a bigger box and add a logo and and “air quality logger’ or something label on it.
It can be a way to help remind people to be cautious with digital security. The IT group at my workplace occasionally leaves flash drives lying around the office. If you plug it into your computer, it autoruns a program that makes you retake cybersecurity training session
Love the idea. Just might keep centrifuges safe.
Wow! Free thumb drive!
Shiny!
Wait, your machines are configured to autorun from removable media? *facepalm*
Obviously, the use case is to plug it into the computer of your workplace nemesis. After that, you can use your offline disposable computer to try it out, wipe it, and repurpose it.
Interesting project, but I must be missing something. Let’s say this is a finished product and it gets plugged into an electrical outlet at some company. Sure, it’s inside the premises and no doubt has good signal strength on the corporate WiFi, but so what? The WiFi will be secured and the device has no way to get on the corporate wired network, so exactly what information could be gathered and exfiltrated?
I think the main idea is to arm it with wifi attack tools to let it get on a network and/or do man-in-the-middle data interception. Even if it can’t exfiltrate the data while installed at the secure location, being a power adapter, it may be easily taken between multiple locations (whether by you or by the victim), one of which may be insecure, allowing for data to be dumped at a later time and place.
Remember Pirate Boxes?
This project instantly reminded me of the Sheeva Plug.
There was also the Pwnie Express and their power strip and plug. although that was almost a decade ago now.
The image he has shows someone holding a Yagi antenna to fox-hunt the pineapple. I don’t see how hiding the form factor would help in this situation… I think the better method would be to (as other commenters pointed out) transmit on other frequencies and do it as infrequently as possible. Also, if I was an employee who saw a random USB power source plugged in with no one around, I’d unplug it and put it in the lost-and-found box. If you really want to hide your AC powered pineapple, I’d still go with a wall wart, but I’d make it look like one of the generic 5V or 12V wart-to-cable-to-barrel types, and then tuck the wire in somewhere. I see those all the time for displays and lighting and I’d guess that it would draw less attention that a ‘forgotten’ USB wart. Personally, I’d just put a big 18650 bank with it and hide it in those terrible fake plants every business seems to have. For less than $150 you could go to Microcenter right now and get a Pi4, additional USB WiFi module, 20,000mAh battery, and even electrical tape to hold it all together. That combo should go for weeks and be able to be completely out of sight.
A fake plant could allow the use of a longer antenna as well.
I’d just install it straight into a socket. Takes SWIM less than five minutes to replace a generic one…
The Allwinner F1Cx00s might be a better choice if you’re trying to save space and don’t mind having only one sub-GHz CPU core. It has RAM built-in and can quite easily run without a full-featured PMIC. The “linux business card” project featured here a while ago would be a good reference.
I’ve used the RTL8821CU WiFI/BLE module with good success on a project. It has got a USB interface and Wi-Fi Dual-band 1X1 11ac +Bluetooth and the drivers seem pretty solid.
We’ve got several leftover from a project and I figured someone else could use them, so they are posted here:
https://xscomponents.com/product/6221e-uuc/
I really like the AR9331 for this sort of project. Not terribly powerful, but decent WiFi (if only 2.4GHz). Also has a USB host, so you could attack any USB device that gets plugged in to it. And you can make some super tiny boards with it – for example, ZSUN WiFi Card Reader.
Good luck getting a Realtek part in the next 2 years. They are at the top of the list of shortages. I don’t follow the WiFi parts but the Ethernet parts have gone from $1 to over $8 – if you can find any.
What happens in this case – so many boards (embedded and full PC) seem to use RTL chipsets for various things – Is that a redesign and new revision to continue production for the board manufacturers?
A souped up version of COTTENMOUTH, but larger and hidden inside a mobile phone charger.
Add a super capacitor or a small lithium cell to shutdown in the event the power is removed.
It could read the data lines on a mobile phone.
Waiting a few minutes before it tries to gain control and grab data, then it could upload it to the Internet, maybe looking at the facial proximity sensor to see if it’s face down first. Perhaps even, also, monitoring the power/earth line for those plug in ethernet extension boxes. Pretty scary to contemplate how powerful this little board is for it’s size.
At least for iPhones, that would be a challenge since they generally pop up a notification that an untrusted device is trying to connect. But if it could be pulled off, the payoff could be huge.