The modern smartphone is a marvel of sensors, radios, inputs, outputs, and processing power. In particular, some of those radios, such as WiFi and cellular, have grown fiendishly complex over the years. Even when that complexity is compressed down for the user into the one-dimensional space of the signal strength bars at the top of your phone. So when [David Burgess] was asked to look at some cellphone records of text messages and figure out where some of the more mysterious messages were coming from, it led him down a rabbit hole into the dark arts behind the glowing phone screen.
The number in question was 1111340002, sent by a phone connected to AT&T at the time, and was crucial for a legal case around distracted driving. [David’s] tools in his investigation were YateBTS (a cellular network simulator), SimTrace2 (pictured above), and old reliable Wireshark. Since the number isn’t a specific phone number and is not reachable from the public phone network, it must be a unique number inside AT&T processed by one particular AT&T SMSC (Short Message service center). The SMSC in question is in Atlanta and isn’t a typical texting center, so it must have some particular purpose. The message’s payload is raw binary rather than text, and [David] has done a pretty good job of decoding the majority of the format.
The most exciting revelation in this journey is that the phone (in the traditional sense) does not send this message. The processor on the phone does not know this message and executes no code to send it. Instead, the SIM card itself sends it. The SIM card is connected directly to the baseband processor on the phone, and the baseband polls the sim every so often, asking for any commands. One of those commands is an SMS (though many other commands have worrying consequences).
The SMS that [David] was chasing is triggered whenever a SIM detects a new IMEI, and the message lets the network know what about the previous and current IMEI. However, in the case of this message, it was unlikely that the SIM changed phones, so what happened? After some additional lab work and the deposition of an AT&T employee, [David] showed that a baseband firmware update would also trigger this SMS.
It’s a fascinating journey into the fragmented world of a smartphone’s minds and [David] does a fantastic job on the writeup. If you’re interested in sniffing wireless accessories, you will enjoy this soundbar’s wireless protocol laid bare.

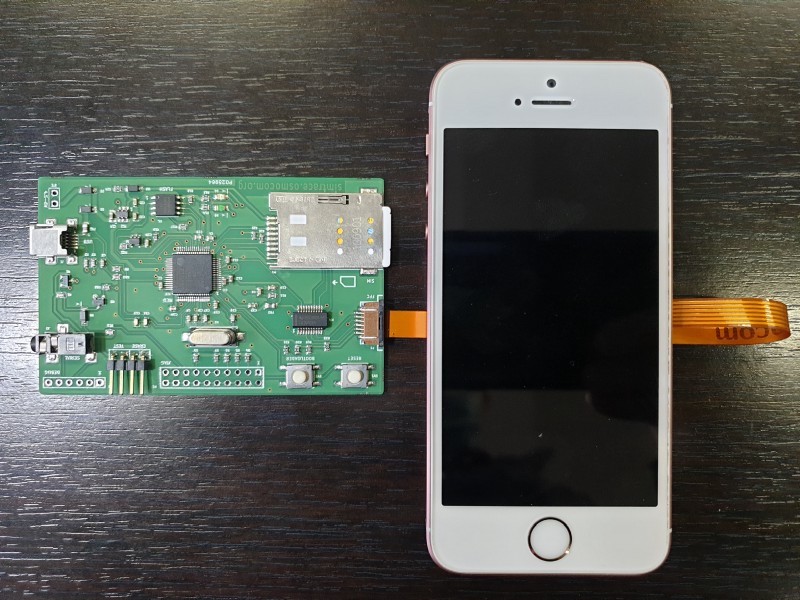













SIMs can send sms!? That seems….nasty
If you look into how they actually work, they are small computers that are directly connected to the modem, completely taking the rest of your phone out of the loop.
Sort of the AMT/PSP of the cellular world.
I suspect this feature is also used by banks to prevent phishing, I know that some banks in the Netherlands had deals with all the telcos to receive notification on sim changes, after which your 2FA would be temporarily blocked
Ol’ Snowden wasn’t so off-base after all…
Maybe people should be suspicion of their cable modem?
Hopefully the sim can only send sms back to the mothership and not a definable phone number.
I can imagine a manufacturing company with strong ties to their countries government (Russia, China, Isreal) creating malicious SIMS that are distributed across the world that would in fact send messages back to both a carrier (mothership) and a separate data center. According to this site, there are at least 6 Chinese manufacturers. Yikes!
The SIM can send whatever it wants where ever it wants …
It can also be updated over-the-air and loaded with new software applets that can a lot of things.
Nothing new with that, it’s all in the spec and documented.
So…
The driver was not actively using the phone, so at least the phone was not a factor of a possible distraction.
The thing is that they checked the phone records and thought the driver was actually texting right before the accident, in which case the defense had to go to great lengths to prove otherwise. I seen a much more in depth article about the case and they detailed the architecture of the phones and the whole process, etc., and it turns out that the sim is not only sending out messages after an update but several times daily with location information and all sorts of data.
“After some additional lab work and the deposition of an AT&T employee, [David] showed that a baseband firmware update would also trigger this SMS.”
It probably triggers off of the IMEISV which is the International Mobile Equipment Identifier + Software Version which is intended to clarify the possible behavior differences between devices of the same physical design but with a different software loadout (mostly the baseband). It came about early on because phones were getting more complex and operators needed a way to control which software versions of phones were allowed on their networks
For example, a phone with an old firmware may have a known incompatability with a certain brand of base station infrastructure and the operator won’t want it on their network, so they’ll add it to the deny list for their VLR/HLR.
Most of my experience is on the infrastructure side, but I have been involved with SIM provisioning from the operators point of view. I’ll have to agree with anyone who is freaked out by what all the SIM is allowed to do to/with your phone. It’s a completely autonomous and cryptographically hardened computer inside of your phone that you can neither control nor inspect. It can do pretty much anything it wants–and it works for the operator, not for you.
There is no privacy. Cookies track you, your ISP records your browsing, all social media tracks you and your behaviour, your search habits are recorded, your alexa records everything, and your OS reports back too. All data collected so you can be processed, tracked and packaged. Even your SIM is silently reporting on you. Welcome to Big Brother.