An age-old vulnerability of physical keypads is visibly worn keys. For example, a number pad with digits clearly worn from repeated use provides an attacker with a clear starting point. The same concept can be applied to keyboards by using a thermal camera with the help of machine learning, but it also turns out that some types of keys and typing styles are harder to read than others.
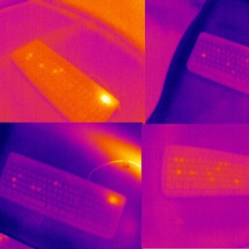
Touching a key with a fingertip imparts a slight amount of body heat, and that small amount of heat can be spotted by a thermal sensor. We’ve seen this basic approach used since at least 2005, and two things have changed since then: thermal cameras gotten much more common, and researchers discovered that by combining thermal readings with machine learning, it’s possible to eke out slight details too difficult or subtle to spot by human eye and judgement alone.
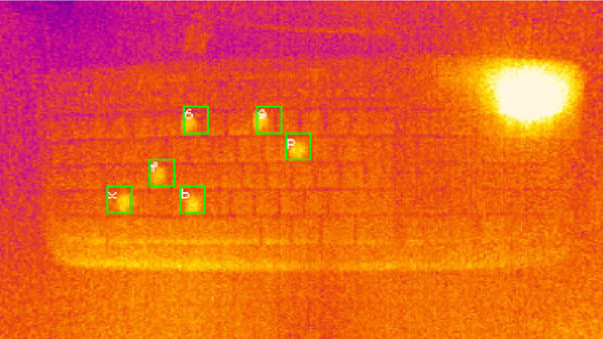
Here’s a link to the research and findings from the University of Glasgow, which shows how even a 16 symbol password can be attacked with an average accuracy of 55%. Shorter passwords are much easier to decipher, with the system attacking 6 and 8 symbol passwords with an accuracy between 92% and 80%, respectively. In the study, thermal readings were taken up to a full minute after the password was entered, but sooner readings result in higher accuracy.
A few things make things harder for the system. Fast typists spend less time touching keys, and therefore transfer less heat when they do, making things a little more challenging. Interestingly, the material of the keycaps plays a large role. ABS keycaps retain heat far more effectively than PBT (a material we often see in custom keyboard builds like this one.) It also turns out that the tiny amount of heat from LEDs in backlit keyboards runs effective interference when it comes to thermal readings.
Amusingly this kind of highly modern attack would be entirely useless against a scramblepad. Scramblepads are vintage devices that mix up which numbers go with which buttons each time the pad is used. Thermal imaging and machine learning would be able to tell which buttons were pressed and in what order, but that still wouldn’t help! A reminder that when it comes to security, tech does matter but fundamentals can matter more.
















Ok, an 8 letter password will give you 256 possible combinations.
Add shifted and special characters and not even machine learning is going to help.
No, 8 letter password would give you around 40k combinations, or 8! to be exact. Not counting shifted combinations.
How will it read my password if I have the letter “a” 13 times in a row as a password?
That would be hard. :) 8! Is number permutations of eight keys without repeated or letters or use of shift.
Add a regular deliberate errors and backspaces and things get very complex rather quickly.
binary “letters” ahahaha
Not to mention, this technique depends on the user not typing anything else but the password and then walking away, leaving his warm finger grease out for an expensive thermal camera to snoop. And since this thermal signature fades rather quickly, one would wonder if there’s a realistic situation where this would be preferable to using a more pedestrian webcam or similar to record the fingers in the act of typing instead.
I suppose if you ever find somebody who both snoops for cameras aimed at their keyboard, but also has a bad habit of entering his password and then leaving his desk immediately to get coffee…
Still wrong. An 8-character password, typed on a typical computer keyboard, has about 6 x 10^15 combinations. (26 letters in two cases, 10 digits that also have symbols, and 11 keys with two symbols, for a total of 94 characters; 94^8 = 6 x 10^15)
Some other combinations:
An 8-letter password, all lower-case, is 26^8, for 2 x 10^11 (200 billion).
An 8-digit password is 10^8, 100 million.
Factorials never come into it (that would be 8 possible characters, each only able to be used once, in an 8-character password; obviously dumb).
8! IS (mostly) right if you consider we’re talking about 8 known keys and not about 8 random character.
‘Mostly’ because if a key could has been hitted twice or more then result will be > 8!
Good point. Re-using a key in an 8 character password will mean only 7 keys touched though, for 7 x 7! combinations, or 35k.
Many passwords will have an upper case in there somewhere (the not counted shifted combinations in the post I was trying to reply to), for 16 characters possibly used. Still assuming an 8-character password (with no repeated characters), that comes to 520 million combinations (16!/8!). Reusing one there (7 keys plus shift touched in an 8-character password) drops it to 240 million.
But further on the attack, it won’t work well if you’re like me and rest all your fingers on the home row before starting typing, let alone touching other keys… Then start typing something else soon after entering your password, and that will mess it up even further.
I thought of 8 lightedup keys where1 has been hitted twice.
So that would be 8 x 8!
Yes, and if shift is glowing, it rases number of permutations 256 times for eight character password. 255 actually, as we know that at least one key is shifted. :)
Correct, but now you have a 9-character password.
Yeah but in this case you know which eight keys (or fewer if a character is repeated) are used, so you’re not going to use that same formula. You just have to find the order of 8 characters, and this would be totally agnostic of symbols etc (but you would have to test for the variants of each key when holding down shift).
It would still contain an impractical number of possibilities and a lot of uncertainty. Say the shift key has heat; how do you tell which character was depressed when the shift key was? That would require some impressive thermal resolution.
It’s all just academic, but it’s fun to get nerd sniped sometimes.
I saw this in a film a few years back. I can’t for the life of me remember which one it was. Somehow the character managed to use the right combination of keys first time.
Original Mac Gyver did this
I still remember it !
Humans do tend to fall into patterns, many of them relatively predictable – so if you know the value/position of every key pressed you can have a reasonable chance at noticing one of those lazy patterns or easy to remember in this context number those keys fit.
Obviously there is no such thing as entirely reliable there, but knowing little details about human tendencies, which usually means lazy low effort tactics either to input or to remember. It will never cut the guesses down to zero but starting with those ideas in mind SOMETIMES will mean you just get lucky and cuts the possibilities you have to brute force down hugely.
There was something similar in the movie National Treasure as well.
Relevant for PIN pads and similar, but on computers it is quite rare to type *only* your password and then leave the computer less than a minute later.
and I’ve definitely some fingers on some key I do not push when I type… eagle typing is not my kind…
$ sudo some_command_that_takes_time
Enter password: *****
*goes make coffee*
But yeah, i am not afraid of this. I don’t have a (thermal) camera pointing to my keyboard…
You don’t know it yet ;-)
I think the only advantage of this is that it could be done a little after you leave, so the camera wouldn’t have to be hidden beforehand. Otherwise why not just record plain optical video of your fingers poking the keys in their proper order? Much easier. But if somebody is very careful about that, perhaps one could walk up and snap a photo while you’re off to the WC. Assuming you didn’t type anything but a password (before OR after), which is kind of a silly assumption.
Presumably this relies on the user entering their password and then showing their keyboard to a thermal camera fairly promptly without doing any actual work (which would cause further key presses).
Which won’t be that unusual – you log in and sit back with your cuppa as it loads, you sudo a process and wait for it to finish. If there is a camera on that keyboard it will have more than enough time to know which keys were pressed on many occasions. Sure many times you will authenticate and go right on working, but those times you are not doing that could be enough.
That said this seems massively complex to set up and still unreliable – simpler and really reliably is to just put a USB sniffer in the cable between the keyboard and computer instead of trying to set up the camera… As long as you are not caught in the act of placing it you can capture all their keystrokes and deliver them via whatever method you set up, with far less difficulty than getting a good angle on the keyboard. And if they are using a wireless keyboard you can probably manage to sniff the traffic without getting that close too – obviously that will run into issues of correctly capturing all the right packets with frequency agile wireless techs and then most likely decrypting the output. But still probably way more reliable than a camera that just says these keys are warm…
Lot of fallacies in article. A keyboard that has been sitting out in my garage for a year in New England weather will not exhibit latent heat of any kind until used in a normal environment. This is an extreme case. A PC sitting in my house that has never been used also will not yield patterns squiggly things or anything else until used by the 4 and 7 yr Olds in my house.
The fundamental facts are true. If I were to use a KB everyday writing the same thing over and over, including passwords, it would only yield a jumble of key numbers. However for the sake of science it must be fun to use a Billion $ AI system and expensive cameras just to find if my letter to ‘Dear Martha’ contained any secrets, or repetitive key strokes as in: the, and, on, off, her, him, them, etc.
Thks for listening
A
Thermal cameras are not even $1000 and AI can run on a potato (albeit slow). Beyond a few characters it simply can’t get any information out because keyboards don’t have enough unique keys and words use letters too uniformly for the data to be turned into anything other than a heat smear.
Looks like this user managed to enter their password without pressing “Enter”. Who the heck types their password and then moves the mouse to click the button?
Anyway, like others, I don’t feel this is a security issue due to the sheer impracticality and countless assumptions (shot taken pronto after password, no repeat keystrokes, etc). If you are going to attempt anything like that, you’ll have much better luck just sneaking in a real camera and record a video in the style of the cash machine passwords grabbers.
“Who the heck types their password and then moves the mouse to click the button?”
Quite a few actually. Although it’s more password manager auto-fill then enter.
Personaly I know few, all are age 70+ :)
Some things I’ve noticed recently know when the string you entered is the right length and auto submit on you as soon as you put in that last character.
Also there are the peck typist, they may have kept a hand on the mouse as they peck away, and as Martin says old folks on computers do things in many rather unique ways…
The application here is for ATM’s, surely. So now we have to mash all the keys after entering our PIN number numbers.
I was thinking the same thing.
Which is what I already do regularly… My young years of watch McGyver have finally become useful.
Fortunately all my passwords are made of dots (or asterisks) no matter what I type.
Morse code keypad.
With fast typers, the heat absorbed by the keys is less, but there is also less time between the keys (and I assume less temperature difference). The time a key is actually touched will probably dominate.
And of course there is the typing style. When you take a thermal image from my keyboard, “asdf” and “jkl;” will be extremely hot, and keys on the bottom row will register a lot less, also depending on when I last clipped my finger nails.
Yet another big factor is the assumption that the keyboard is only used to enter the password, and that is rare too. Usually it’s a username / password combination, and typing this text for hackaday also takes quite some keystrokes… Even for ATM’s, I normally also press some menu keys, and enter a non custom amount to dispense. But it’s still valid though. I quite often use a few key strokes to start Keepassx (others do that with a mouse too) type the master password, and do the rest with the “autotype” (activated by mouse clicks because I don’t do it often enough to get the key combinations into muscle memory. It may work pretty well for some entry keyboards, but the picture of showing a standard PC keyboard with this article sort of implies probably much more is being typed.
Or in case you have a shitty interface where hitting ENTER just won’t suffice and you actually have to use the mouse to click that damn button.
I think a previous commented was alluding to the fact that having a password that includes one or more characters requiring the use of the Shift key would surely reduce the success rate of this method.
Additionally, having one or more characters that are used more than once in the password would seem to make this method less effective.
If this attack vector is open then that means there’s some sort of physical access available to the attacker. This might be for a remote login, but still there’s other vulnerabilities this could introduce. Other than the lack of encryption (or a non-hardware-based drive encryption) for a machine co-located with its keyboard, another example would include an in-line keylogger between the keyboard and computer would make this attack form unnecessary.
And who logs in to a machine and immediately logs out of it without using the keyboard for other input? This additional input would surely reduce the success rate of this attack to nearly zero.
I’m sure there’s a special use case or two where this might be effective, or perhaps this attack coupled with another method could increase its effectiveness, but by itself it seems more of a curiosity.
How much does RGB affect this?
I was thinking the same thing!
2FA on another device kills this attack I think. Passwords are basically dead on reasonably secure systems now anyway so perhaps this does only matter for low security systems like 4 digit pin codes? NFC tap to pay seems to solve this as well. Thanks for the heads up though – next time I need to use my pin I will mash some other buttons first or just put my hand on the whole keypad for 10sec… :)