It’s a story we’ve heard many times before: if you want to get your data from the Domyos EL500 elliptical trainer, you need to use a proprietary smartphone application that talks to the device over Bluetooth Low-Energy (BLE). To add insult to injury, the only way to the software will export your workout information is by producing a JPG image of a graph. This just won’t do, so [Juan Carlos Jiménez] gives us yet another extensive write-up, which provides an excellent introduction to practical BLE hacking.
He walks us through BLE GATT (Generic Attribute Profile), the most common way such devices work, different stages of the connection process, and the tools you can use for sniffing an active connection. Then [Juan] shows us a few captured messages, how to figure out packet types, and moves into the tastiest part — using an ESP32 to man-in-the-middle (MITM) the connection.
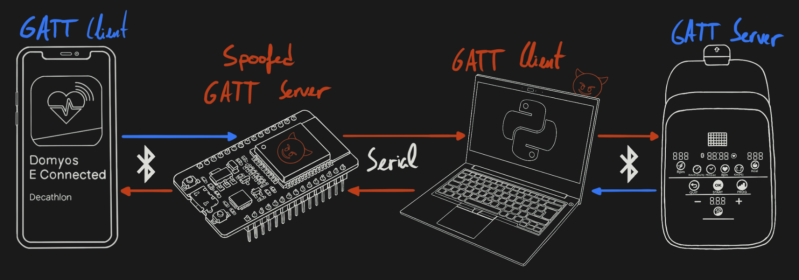
The MITM consists of two parts: a laptop with a Python script talking with the Domyos EL500, and an ESP32 that’s spoofing the EL500 to a smartphone app, tied together with a serial link. You can capture all the messages that the app and the trainer are exchanging, modify them in real-time and see the reaction, and figure out how to extract all the data you could dream of. This is more than enough to conquer the next frontier — writing a third-party app to capture workout data, and we can’t wait to see this experiment conclude.
BLE is ubiquitous and used in what feels to be every IoT device under the sun, which makes it all the more wonderful that we’ve got yet another tutorial on how to bend it to our will. The tools are easy to find, too. You can use an ESP32, a Raspberry Pi, or an nRF dongle. You can even get pretty far using nothing more exotic than an Android device. Whatever approach you take, the journey is sure to pay off.















There are wearable heart rate monitors out there that ONLY work with a smart phone and ONLY with the manufacturer’s proprietary app. You can imagine what happens to your data.
Yeah I have a heart rate + SpO2 monitor that I’ve been wanting to hack in this way for similar reasons. I once asked the manufacturer if they had an API or any other means of getting the data out and they started trying to sell me an OEM mass-manufacturing license and said that they’d only be interested if I could guarantee shipping some ridiculously high number of units, and didn’t seem to understand I was just trying to get my data out for a twitch overlay.
Do I look like like I know what a jaypeg is? I just want a spreadsheet of my god dam workout!
YES lmao that’s an amazing summary
Oh, man!!!! This is exactly what I needed!!!!
yesss that’s Juan’s MO, he’s been writing the “exactly what I needed” articles for a while now =D
Shame we have to hack into our own devices.
Yeah, wallet-voting implies resisting marketing violence.
The real challenge is talking with manufactors, explaining them what you really want.
I understand why a company would opt for a proprietary protocol, it easy to implement compared to working with the Bluetooth SIG. The difference oppressive.
Perfect timing, was trying to do the exact same thing to a blood pressure monitor this week! Great writeup
I just took out the computer in my rowing machine and replaced it with an esp8266 running Tasmota.
Which machine? I was hoping to do the same with mine.
oo nicenicenice ever documented that anywhere? sounds like prime Hackaday material, send that in whenever you have some details, sounds like others could benefit from that too ^~^
There is a robust project on GitHub to do a lot of this already, https://github.com/cagnulein/qdomyos-zwift
Yep, this is a great project and this dev also has ios and Android apps available (QZ Fitness) for folks that don’t want to tinker.
Is the manjaro face worth it rooted wireless still trying to understand some of processes and mods it carries!!! Seems pretty legit got into the list of extras on the wifi aka the labs about to open the certificates to download?
Hi, did you check the QZ project? it covers this and much more! https://github.com/cagnulein/qdomyos-zwift