When you think of attacking or defending computer systems, you probably think of software viruses and the corresponding anti-virus software. But MIT’s 6.5950 class teaches secure hardware design — how to attack and defend CPUs from bad actors. Interested? The course is open source, so you can follow along as long as you don’t mind not getting a grade.
Browsing some of the lecture slides shows that the material isn’t as stuffy as you might imagine. A slide about side channel attacks, for example, features an article called “And Bomb the Anchovies,” which says that Washington DC pizza places know when big news is about to break because pizza delivery to places like the White House or the Pentagon trend upward (something spies call pizza-int, by the way).
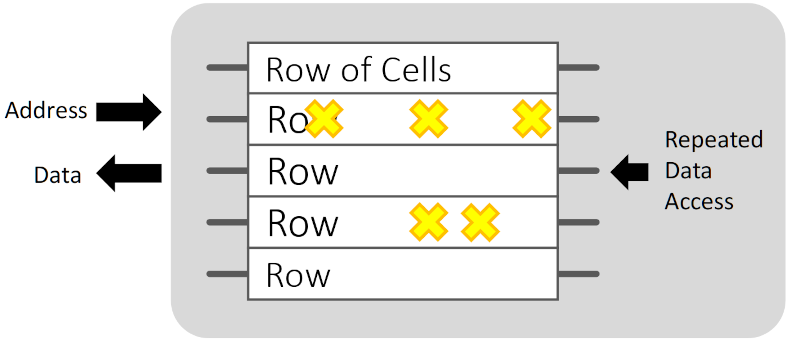
Even if you don’t have a burning desire to design more secure hardware, some of the lecture slides make for an interesting flip through on a rainy weekend day. For example, the charts about RowHammer (“RowHammer in One Sentence”) is a great explanation about how software can cause DRAM failures to attack a computer. We only wished they’d identified companies A, B, and C in their study. There are also labs and they politely clarify what setup you need to do each lab (typically, just a Linux server, although some you can do with just a browser).
One of the great things about the Internet is that you can virtually audit classes from anywhere in the world, often for free. MIT is always up to something interesting.















And the sources repo is https://github.com/MATCHA-MIT/SHD-StarterCode ?
I know its probably the wrong outlook to have but whenever I hear “security” in context to hardware, I just roll my eyes mentally. Its just a lot less serious in my mind, compared to software vulnerabilities for whatever reason
Hardware security is as much about building secure hardware architectures as about the software running on low level hardware. This training, even if you aren’t going to develop hardware, shows software isn’t executed in a vacuum. You will have to be aware of the limitations and requirements.
One important requirement is to maintain the root of trust. Root of trust starts with the hardware, and is passed from the n-th stage bootloader to the operating system to the applications. Wherein, no software is secure if previous boot stages are compromised.
Another disturbing fact is that your bug free code can be compromised when it is executed on hardware. Fault injection attacks compromise the execution flow by manipulating the physical chip. E.g. by shooting at it with lasers. If the attacker can skip an instruction through FI, any code can be compromised.
These are just examples, and they aren’t limited to theoretical software. Mathematically sound cryptography doesn’t fare much better. While unbreakable within the current computational limits, implementations are sometimes broken in a matter of days through hardware attacks.
Isn’t that partly the point – to start doing things in-house? The other part being to bring the other parties to a negotiating table. This isn’t a tariff war, simply a time for the US to stand up for itself and get a better deal from its trading partners.
“US to stand up for itself ”
Don’t think you will feel that way in a few years. Hope I’m wrong. :(
Are there actual lectures for this MIT hardware course? Poking around and can’t seem to find them…
Lectures from 2022
https://www.youtube.com/@NickolaiZeldovichMIT/videos
More recent lectures.
https://css.csail.mit.edu/6.858/2024/