If you talk about Starlink, you are usually talking about the satellites that orbit the Earth carrying data to and from ground stations. Why not? Space is cool. But there’s another important part of the system: the terminals themselves. Thanks to [DarkNavy], you don’t have to tear one open yourself to see what’s inside.
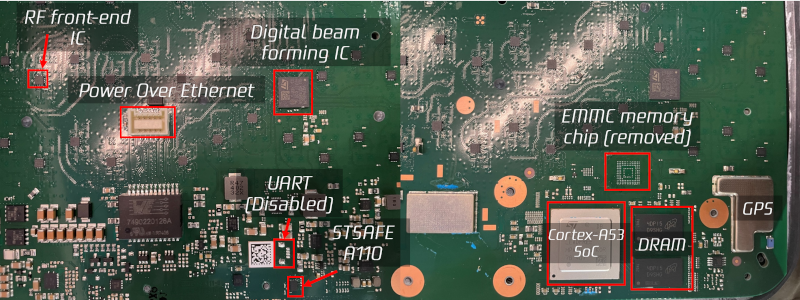
The terminal consists of two parts: the router and the antenna. In this context, antenna is somewhat of a misnomer, since it is really the RF transceiver and antenna all together. The post looks only at the “antenna” part of the terminal.
The unit is 100% full of printed circuit board with many RF chips and a custom ST Microelectronics Cortex A-53 quad-core CPU. There was a hack to gain root shell on the device. This led to SpaceX disabling the UART via a firmware update. However, there is still a way to break in.
[DarkNavy] wanted to look at the code, too, but there was no easy way to dump the flash memory. Desoldering the eMMC chip and reading it was, however, productive. The next step was to create a virtual environment to run the software under Qemu.
There were a few security questions raised. We wouldn’t call them red flags, per see, but maybe pink flags. For example, there are 41 trusted ssh keys placed in the device’s authorized_keys file. That seems like a lot for a production device on your network, but it isn’t any smoking gun.
We’ve watched the cat-and-mouse between Starlink and people hacking the receivers with interest.















At a guess, they are the exact same public ssh keys on all StarLink terminals globally. I can not see anything that could possibly go wrong with that :)
Probably one for the spooks of every country that allows the use of Starlink.
I’m not sure I’ve seen the word “spook” used like that before, could you explain what you mean by that?
It just means a spy.
Yes, but.. (apologies in advance for my pedantic linguistic elaboration)
It also implies a specific type of spy, though I don’t think the meaning universally agreed upon.
To me, and I think to people in the US and UK generally, it’s a spy that works for a government intelligence/espionage agency, like the CIA, NSA, MI6, or your country’s equivalent. It implies to some extent that they’re involved in foreign intelligence gathering rather than domestic (“CIA Spook” is classic, but “FBI Spook” sounds odd).
In the past, it was used more generally to mean spy in the sense of “secret agent” or “undercover agent”, not necessarily one who works for the government. It may be used that way today in other countries, I’m not sure.
In any case, it’s both a perjorative (even more than spies, spooks can be presumed to engage in morally questionable activities) and a bit of a backhanded compliment (spooks are competent, anonymous, high level spies)
If you disagree, and it means something different to you, I’d love to know. Language is fascinating that way.
ref: https://en.wikipedia.org/wiki/Spooks_(TV_series)
They were called spooks in the industry way before that. Maybe the late ’60s.
Quite a bit earlier.
References to use referring to “undercover agents date back to at least 1942. Some Tuskegee black pilots actually calling themselves SpookWaffen.
Most likely Dutch origin, it may have been a term for will’o’wisp. Sometimes in the early 1800’s the term moved from Pennsylvania Dutch to English as a type of ghost, then shifted to cover people. By the 1900’s was used as a label for people instead. An insult to white jazz performers, a questionable name applied to frightened black men, a derogatory term for both female and male students, even inexperienced pilots.
He means International spies Karen
‘Spooks’ or ‘haunts’ were actually an intelligence term used when the CIA was created to describe the way someone stalked their subject in surveillance. This was a post-WWI term from the 1920’s, back when all the detective novels started being written from veteran’s stories.
I wonder does each StarLink terminal have the exact same private (and public) ssh host keys (usually seen with “sudo ls -l /etc/ssh/ssh_host__key“). Every host should have unique host keys. Host keys that are shared is a bad idea, because they can result in being vulnerable to man-in-the-middle attacks.
There should be an asterisk between the two “_”‘s above, but I guess word press stripped it away.
This wouldn’t be the first time that a project has had multiple people working at slightly cross purposes, so I can’t rule it out on that basis; but it would be a bit surprising if they were reusing host keys when they went to the trouble of dropping the A110 in there.
That chip’s whole thing is being aggressively unique per device in a remotely verifiable way(with mutual TLS being STMicro’s focus; but including support for keypair algorithms that SSH uses); so not taking it up on that, potentially even to the point where the host key is not visible to the host OS and authentication is handled within the A110 so as to make cloning harder, seems like it would be a waste.
And that’s why this is interesting, will we find out they are undermining their own security design? If not, why are they relying of hard coded keys? After all, that could just be in the configuration machine during the automated QA.
…Or maybe they bought a design with no idea how to use it. That would be tons of fun right?
The host keys are generated on “first boot” of the factory image.
The auth public keys are the shared ones. They come down through updates. Which makes 40+ keys even more strange. Private keys that are no longer active should be removed. Either they aren’t, or they have a scary amount of active key pairs.
There’s also other public keys in etc/ssh but not in auth hosts. Three without a matching private key. I assume verifying update signatures and such.
Here’s to hoping they have a well thought out and set up key management process.
Maybe 40+ keys is just to confuse?
Which of the 40 is the real Mr. Key.
Are there any hacks of newer devices?
I can’t imagine what they must be paying for such a massive impedance controlled PC board
Also anyone knows what the RF front end IC is? A part number maybe?
They’re really not expensive in bulk. I’d actually be surprised if it’s impedance controlled, though, it’s easier to just design to the stack up and deal with the tolerance variations.
Given the fact that they don’t shield like, anything, my guess is they’re dealing with it via the time tested method of “more power.”
They manufacture the PCBs themselves (Recently boasted that they are going to be the biggest PCB manufacturer in the US) Makes easier to tune design/manufacturing.
The RF frontend is a STMicro, not public:
https://x.com/olegkutkov/status/1726718563627786631?t=CJQ_4sr17RqcddtYgFw58g
Not too keen on the integral GPS.
How else would you propose to get the location and time data required to connect to the constellation?
I mean, it does make sense to duplicate the GPS function in the starlink system itself, and eliminate dependence on a system you can’t control. But you still end up with the same effect: The system requires knowledge of the location of the dish in order to work at all.
Why? GPS by itself does not pass on its location. Are you concerned that the device having GPS provides it with precise location that could then be sent out? GPS would help the receiver find the subset of satellites to communicate with. With no GPS its location could be determined using the Starlink satellites in a similar manner. The result, the receiver knows its location.
Just like when using cell phones, GPS or the lack of it does not mean the receiver can or cannot have its location identified.
Just makes it easier and faster. Plus GPS chips are near commodities.
Starling have been boasting they can offer a gps alternative. They already know the precise location of every terminal without the use of gps.
Starlink satellites doesnt carry accurate enough timekeeping devices to rival GPS. They would have to be synchronized to a starlink provided timekeeper with the necessary accuracy, itself trivial, but actually doing it vs claiming to be able to do it are two separate things.
The GPS is not to help connect to the starlink satellites, it is to find out where you are using the service so they can be a typical greed driven company and charge you more to use the service in one place over another, even though it costs them nothing more.
Just look at their plans and you will see.
How can the gps be disabled.
Typo, the author meant, “per se”.
You know how language is evolving to be more inclusive, right?
So, it’s plural. se (itself) , see (themself)
:-)
(no, right, Latin isn’t evolving. It’s a dead language. Strike all that.)
The tin foil hat folks have arrived to the thread!
Stop all the hating and admit StarLink is cool technology.
Elon is the same genius he always was, only now he’s joined the common sense crowd!
I’m going to push back a little on calling Musk a genius. If you have any evidence of this, I’d be interested in taking a look.
I don’t think anyone disputes that StarLink has cool aspects; it’s just that people who can afford OneWeb are probably going to weigh up the pros and cons.
I presume there will be other competitors along shortly.
Some of us have very low bandwidth requirements; we could probably get by with Meteor Burst Communications!
It was actually in italics, so I just read it as “Per Saayyyyyyyyyyyyyyyy” in a very sassy way that I think is equal in intent.
If you are interested in security, you are NOT using the router that came with Starlink, or you have carefully firewalled it from the rest of your network and you don’t use cleartext for anything. To say that this is a transport you cannot trust is a gross understatement.
This applies to every network device. Everything is compromized unless you run VPN from a reputable company.