In an era where running a website without HTTPS is shunned, and everyone wants you to encrypt your DNS queries, you’d expect that the telecommunications back-ends are secured tightly as well. Especially the wireless bits between terra firma and geosynchronous communication satellites.
But as recently discovered by US researchers, the opposite is actually true. The paper by [Wenyi Morty Zhang] et al. (PDF) goes into great detail on how they discovered these unencrypted IP traffic flows and what they found in these captures.
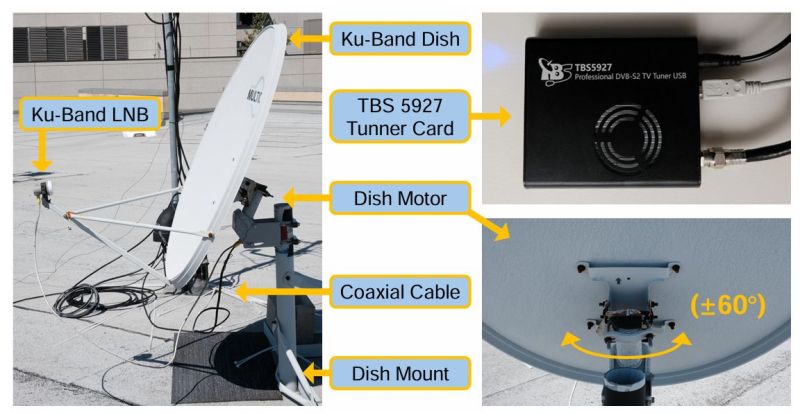
With an off-the-shelf consumer satellite dish mounted to the roof of a university building in San Diego, they performed a scan of IP traffic on 39 geosynchronous satellites. To their surprise, they found unencrypted data that belonged to companies like T-Mobile for their cellular backhaul, Internet traffic targeting airliners, and VoIP communication — all in the clear.
Even more worrying was what looked like military traffic and corporate VPN data containing unencrypted login details, corporate emails and much more. While T-Mobile immediately enabled encryption after this discovery, it remains to be seen whether anyone else will. It’s probably best to assume that any communication can be intercepted and to use e.g. PGP-encrypted emails for anything sensitive.
The researchers have made the IP encapsulation parser (in Python) for DVB-S2(X) captures available for anyone who wants to give this experiment a whirl themselves.















The classic corporate cybersecurity catch 22. If they encrypt traffic they are safer against sniffers and sensors. Meanwhile though they can’t sniff their employees traffic to monitor them as easily. Of course there are ways to have a bit of both worlds and many of these incidents are near complete gaps in their defenses, but it seems to happen more than it should.
This doesn’t make much sense to me since most (all?) corporate environments control the point at which all traffic is routed on the internal backhaul (usually a proxy server) and control the end device on which users make the request, so can easily check what you’re doing via endpoint security products.
It makes much more sense in my opinion that this is just a classic case of incompetence/lazyness, some architect or network engineer thought to themselves “who would sniff traffic on a satellite backhaul?” and didn’t enable encryption.
Forgot to take your meds? 😂
I can confidently assure you that corporations can both fully encrypt their communications and easily and happily monitor all their employee communications so long as they occur on company issued or approved hardware and channels. This includes many things employees don’t usually think about, including SMS if sent from or to corporate “enrolled” devices.
It’s funny if you compare it to how extreme the efforts are to encrypt normal things that don’t actually need insane encryption.
But my cat pics are VERYYYY IMPORTANT!!!
It’s not only about confidentiality.
Encryption also offers integrity of data.
If an attacker can meddle with unencrypted traffic, your cat picture might suddenly include exploit code.
Wrong
I’d argue that all data is worth encrypting and strong encryption should be the default. Our computers are plenty powerful and can encrypt all data with little effort. People send sensitive info like passwords all the time and share passwords between accounts. There is no need to classify data or use-cases as “need” or “don’t need”, they’re all deserving.
AES and other “strong” crypto algs are legalized now only because NSA can crack them. It’s been the same way during Cold War where rotor machines were marketed to business and individuals as “secure” but in fact they were designed to be weak and on top of that manufacturer was forced by the US to make them weak to TEMPEST.
Internet is not anonymous, never was, never will be.
Big difference between in the clear trivial data breach and doable but needs real effort though. Sure you can crack many cryptographic methods, perhaps even in a moderately timely fashion if you have 3 letter agency or giant corporation money to throw at the problem, but with millions of people sending many messages that take some time to crack even for those agency unless they have a reason to focus on you its just part of the noise that won’t be decrypted.
You seriously believe NSA is not spying on you right now? Microsoft would not be able to exist if they didn’t cooperate to help them (and the CIA) to protect american interests at home and abroad.
Being paranoid is what helps me avoid jail for the last 38 years of my life…. and I’d rather not end up waterboarded in some black site because I know how to bypass their backdoors.
@Joshua, The giant data hoover is doubtless pulling in whatever data it can, but they are going to be doing that on everyone, and millions of people’s worth of data is more than can actually be dealt with, especially if its all even very lightly encrypted with something the average gamers PC could decode in an hour or less. That encyrption can’t save you should there be a reason to look at you closely, but no encryption can really do that – if they really want to know they can always find the $5 wrench…
So @Maave is quite correct just encrypt everything, even if its low priority stuff, then you are protected from pesky snoops of the more normal not state sponsored level rather well and if we are all doing it blending in the crowd enough even those with deep pockets are not going to be so successful in their data harvest, or you have made them really work some for it.
Take your meds
That’s you view, let’s accept it’s a single view and not a global mandate OK?
OK then.
Incidentally, I could read your comment in plain text, tut tut.
nah these are the new expectations and standards. You’re free to send data unencrypted. Anyone handling data (like ISPs) is expected to NOT expose user data. Users expect privacy. Go ahead, tell the users that their passwords are being transmitted across the entire country, see if they’ll buy your service or product.
Diffie-Hellman algorithm (invented in 1976) involves modulo math that can be done with natural numbers.
I would have to assume this is generally known and exploited by intelligence agencies around the world
Otherwise why would people want their own system of satellites? But space Xpensive, so maybe don’t be Russian in?
One of the well-known doomsday radios run by russkies is not encrypted at all. What it transmits, however, is anyone’s guess.
Worked satcom most of my career and this made me mentally double check every link I ever set up. Sheesh.
This story seems kinda odd given most traffic is E2E encrypted (https, email/TLS – in my tests, almost all client/server and most server-server traffic is encrypted, etc). Very little traffic leaves a device without being encrypted these days.
I think this is mainly about SMS and RCE messaging.
some is SMS/RCE, some isn’t. Check the paper, they give examples
“We also observed large volumes of plaintext DNS traffic.”
“We identified three satellite beams carrying unencrypted Walmart-Mexico internal system traffic that could be received across North America.”
“Tunner”?
Anyone moving any data that’s important should assume that if the data is transmitted (wired or wireless) in a way that leaves your property, it could be intercepted by an adversary and therefore it should be encrypted.