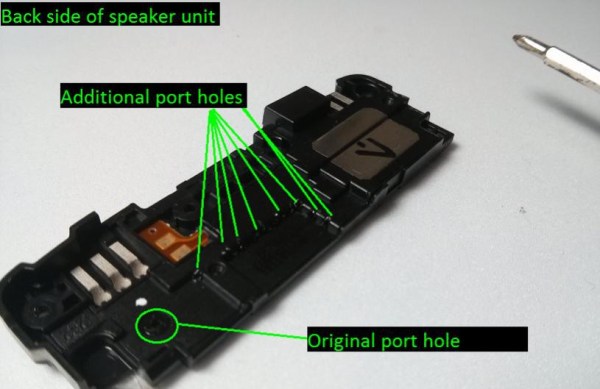
The much-anticipated Nexus 5 starting shipping out a few weeks ago, and like many new products, some people have received phones with manufacturer defects. This is always unfortunate, but [Adam Outler] over at the XDA Developer forums thinks he’s found a solution to one of the ailments — a low speaker volume fix!
[Adam] noticed that his phone wasn’t quite as loud as he was used to, so he decided to take it apart and see if there was something causing the muffled sound quality. He assumes glue seeped into part of the speaker where it’s not suppose to during assembly, and what he discovered was, you can increase the audio output by opening up the speaker chamber. He found you can easily port the speaker chamber by popping a few holes in it using a hot needle, which helps increase the volume of the phone. It’s not exactly a confirmed hack, but he will be featuring it on XDA-TV in a few weeks, and hopefully a few more cases pop up in order to evaluate the effectiveness of the hack — it might even help users whose phone isn’t unusually quiet!
Now, most people will just return the phone under warranty, which makes sense. But this is Hackaday and XDA we’re talking about. It’s probably less effort to just suck it up, and fix it ourselves. Who cares about warranties?
[via XDA Developers]