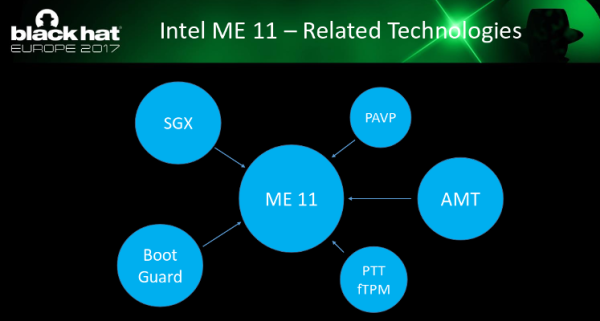
If you have a computer with an Intel processor that’s newer than about 2007, odds are high that it also contains a mystery software package known as the Intel Management Engine (ME). The ME has complete access to the computer below the operating system and can access a network, the computer’s memory, and many other parts of the computer even when the computer is powered down. If you’re thinking that this seems like an incredible security vulnerability then you’re not alone, and a team at Black Hat Europe 2017 has demonstrated yet another flaw in this black box (PDF), allowing arbitrary code execution and bypassing many of the known ME protections.
[Mark Ermolov] and [Maxim Goryachy] are the two-man team that discovered this exploit, only the second of its kind in the 12 years that the ME has been deployed. Luckily, this exploit can’t be taken advantage of (yet) unless an attacker has physical access to the device. Intel’s firmware upgrades also do not solve the problem because the patches still allow for use of older versions of the ME. [Mark] and [Maxim] speculate in their presentation that this might be fixed on the next version of the ME, but also note that these security vulnerabilities would disappear if Intel would stop shipping processors with the ME.
We won’t hold our breath on Intel doing the right thing by eliminating the ME, though. It’s only a matter of time before someone discovers a zero-day (if they haven’t already, there’s no way to know) which could cripple pretty much every computer built within the last ten years. If you’re OK with using legacy hardware, though, it is possible to eliminate the management engine and have a computer that doesn’t have crippling security vulnerabilities built into it. This post was even written from one. Good luck doing anything more resource-intensive with it, though.