It’s fair to say that fingerprints aren’t necessarily the best idea for device authentication, after all, they’re kind of everywhere. But in some cases, such as a device that never leaves your home, fingerprints are an appealing way to speed up repetitive logins. Unfortunately, fingerprint scanners aren’t exactly ubiquitous pieces of hardware yet. We wouldn’t hold out much hope for seeing a future Raspberry Pi with a fingerprint scanner sitting on top, for example.
Looking for a cheap way to add fingerprint scanning capabilities to his devices, [Nicholas] came up with a clever solution that is not only inexpensive, but multi-functional. By combining a cheap USB hub with a fingerprint scanner that was intended as a replacement part of a Thinkpad laptop, he was able to put together a biometric USB hub for around $5 USD.
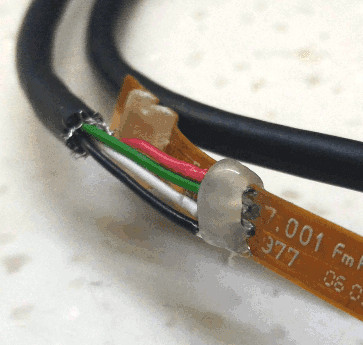 After buying the Thinkpad fingerprint scanner, he wanted to make sure it would be detected by his computer as a standard USB device. The connector and pinout on the scanner aren’t standard, so he had to scrape off the plastic coating of the ribbon cable and do some probing with his multimeter to figure out what went where. Luckily, once he found the ground wire, the order of the rest of the connections were unchanged from normal USB.
After buying the Thinkpad fingerprint scanner, he wanted to make sure it would be detected by his computer as a standard USB device. The connector and pinout on the scanner aren’t standard, so he had to scrape off the plastic coating of the ribbon cable and do some probing with his multimeter to figure out what went where. Luckily, once he found the ground wire, the order of the rest of the connections were unchanged from normal USB.
When connected to up his Ubuntu machine, the Thinkpad scanner came up as a “STMicroelectronics Fingerprint Reader”, and could be configured with libpam-fprintd.
With the pintout and software configuration now known, all that was left was getting it integrated into the USB hub. One of the hub’s ports was removed and filled in with hot glue, and the fingerprint scanner connected in its place. A hole was then cut in the case of the hub for the scanner to peak out of. [Nicholas] mentions his Dremel is on loan to somebody else at the moment, and says he’ll probably try to clean the case and opening up a bit when he gets it back.
[Nicholas] was actually inspired to tackle this project based on a Hackaday post he read awhile back, so this one has truly come full circle. If you’d like to learn more about fingerprint scanning and the techniques being developed to improve it, we’ve got some excellent articles to get you started.







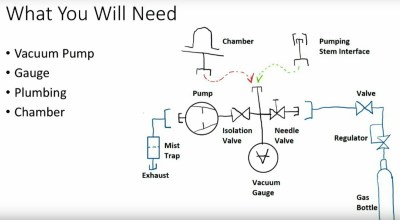 Introduction over, he starts on the subject of equipment with a quick word about safety, before giving an overview of the components a typical small-scale vacuum experimenter’s set-up. We see the different types of vacuum gauges, we’re introduced to two different types of service pumps for air conditioning engineers, and we learn about vacuum manifolds. Tips such as smelling the oil in a vacuum pump to assess its quality are mentioned, and how to make a simple mist trap for a cheaper pump. There is a fascinating description of the more exotic pumps for higher vacuums, even though these will be out of reach of the experimenter it is still of great interest to have some exposure to them. He takes us through vacuum chambers, with a warning against cheap bell jars not intended for vacuum use, but suggests that some preserving jars can make an adequate chamber.
Introduction over, he starts on the subject of equipment with a quick word about safety, before giving an overview of the components a typical small-scale vacuum experimenter’s set-up. We see the different types of vacuum gauges, we’re introduced to two different types of service pumps for air conditioning engineers, and we learn about vacuum manifolds. Tips such as smelling the oil in a vacuum pump to assess its quality are mentioned, and how to make a simple mist trap for a cheaper pump. There is a fascinating description of the more exotic pumps for higher vacuums, even though these will be out of reach of the experimenter it is still of great interest to have some exposure to them. He takes us through vacuum chambers, with a warning against cheap bell jars not intended for vacuum use, but suggests that some preserving jars can make an adequate chamber.
![[M0CVO]'s Tweet that started it all](https://hackaday.com/wp-content/uploads/2017/10/screenshot-2017-10-31-nigel-booth-on-twitter.png?w=298)










