[TrendMicro] are reporting that yet another IoT botnet is emerging. This new botnet had been dubbed Persirai and targets IP cameras. Most of the victims don’t even realize their camera has access to the Internet 24/7 in the first place.
Trend Micro, have found 1,000 IP cameras of different models that have been exploited by Persirai so far. There are at least another 120,000 IP cameras that the botnet could attack using the same method. The problem starts with the IP cameras exposing themselves by default on TCP Port 81 as a web server — never a great idea.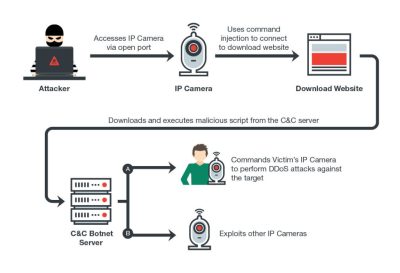
Most IP cameras use Universal Plug and Play, which allows them to open ports from inside the router and start a web server without much in the way of security checks. This paints a giant target in cyber space complete with signs asking to be exploited. After logging into a vulnerable device the attacker can perform a command injection attack which in turn points gets the camera to download further malware.
The exploit runs in memory only, so once it has been rebooted it should all be fine again until your next drive by malware download. Check your devices, because even big named companies make mistakes. IoT is turning into a battlefield. We just hope that with all these attacks, botnets, and hacks the promise of the IoT idea isn’t destroyed because of lazy coders.
Part of feature image from Wikipedia, Creative Commons license.
















A number of these issues can be picked up with static analysis or data flow taint analysis tools. Done right, static analysis tools can hook repository commits, so that these problems can be identified before the code has even been compiled!
Check the taint
https://www.youtube.com/watch?v=xehR7PQ2crQ
Is that a one hole balaclava or a beard and a beanie?
And of course the old fashioned ‘lone ranger’ eye mask, wasn’t aware that these made a comeback.
Good reason to turn uPnP off at the router.
Amen. Too many options these days to make it “easy” sacrificing security.
I always turn off uPnP, all extraneous network connection protocols in the cameras, and firewall all cameras and other devices that don’t need outside access from the internet.
The cameras are only permitted to talk to their DVR.
Can’t be a botnet without a connection in or out…
What about a highly localised botnet?
Quote [Jack Laidlaw]: “We just hope that with all these attacks, botnets, and hacks the promise of the IoT idea isn’t destroyed because of lazy coders”
Comments like this tempt me to write a HaD article about security myself and I am NOT a security expert. I have however been a web server admin for shared servers where there are many security issues. I was also responsible for writing custom “secure” code which on a web server is not as secure as you might want it to be.
I have made many comments about IoT security.
We can’t dismiss this issue as “lazy coders” because, quite simply, that is not the reality of the case at all!!!
I would love to see a decent article on security that reflects practical models.
This attack relies on lazy security practices by the companies who manufactured and wrote the firmware for the devices, I am not so much blaming end users. Why are companies releasing products that by default run a web server? I know it’s an IP camera but surely this should have to be activated perhaps pick a port instead of all being the same by default and stop using default passwords. That is the problem. If you can’t see why that is lazy then I’d hate to see what you define as lazy.
Normally I agree with 99% of your comments but I think you are off on this one RÖB, Perhaps I didn’t explain the position well enough.
I was responding generally to IoT security and not specifically about this case. The last case was a result of uPNP being enabled by default in routers.
In an case though it’s not a “lazy coder” that is responsible as the coder is coding according to company objectives in both of the above cases, so it’s more about corporate/company ethics than anything else.
All systems that have some “security features” have a security model. In the case of IoT, that model is being publicly thrashed out as we speak and we are seeing it’s failures unravel day by day because it is being developed from already failed security models.
Corporate marketing has suffocated ethical engineering in the quest to optimize profit. That is why we have this non-secure junk saturating the market place – put simply – consumers who are less tech savvy are happy to pay for something that works first time without configuration as they don’t have a clue or even care if the device is used in a botnet DDOS attack unless, of course, it slows they internet connection.
Likewise the company selling the devise doesn’t care either as their primary consideration is profit and security gets in the way of that objective so it is ignored.
So to summarize, I am not here to dispute what you have said. I am simply stating that I believe that there is much more to it than lazy code.
As for default passwords – FLASH chips are often bank programmed. From a manufacturing point of view it’s quite expensive to have different passwords on sequentially produced items but there has been some slight improvement in that regard.
All of these problems are solvable. And the people (hackers) on HaD are just the people to solve these problems because open source solution is the only solution that manufactures can possibly agree on.
We should be talking about a Model for IoT security because we now have the opportunity to break away from the more common and currently used failed security model that proliferated from the PC and internet.
Currently, the most common security model is to black list the actions of (black hat) hackers. Ironically this model is dependent on those very hackers succeeding in order for security to improve. It is simply a progressive process where there is increasingly more to be lost to successful hackers as time progresses.
Having worked in M2M, I believe that IoT could end up being a very useful technology. Alternatively it could possibly end up as an abomination. The *make or break* factor will be security.
Of course I don’t believe my opinion is the absolute truth and I would very much like to hear other peoples perspective.
As I stated, I am not a security expert but I have had some limited exposure to that industry.
I agree with everything you just stated perhaps lazy coding wasn’t the right terminology however it is rushed code to get the devices out the door to meet unreasonable deadlines by sales/marketing that kills any chance of implementing proper security. I don’t think it’s the coders fault they have a job to do. More an upper level misunderstanding of the ramifications or just lack any care. You are right it is make or break for IoT I want it to succeed but when malware can literally take down a whole countries healthcare system we have a problem (even if that wasn’t IoT related). It seems to me that there is some kind of cyber war arms race going on right now, and the more people heard about IoT botnets, “hacks” and attacks the less likely people will want the technology. We need to setup up a standard and certification system or something before it goes too far. Pay a fee have your device penetration tested and get a sticker for your box something along those lines. Obviously this will not protect against newly found 0-days but it will weed out the companies rushing out crap and help restore some sort of Tech savvy consumer confidence (as the general public don’t know/understand). This is my opinion on the matter I don’t think there is an easy fix but there are things we can do to improve the industry before it destroys its self.
The default password vulnerability that so many IoT devices suffer from could be greatly reduced if the device refused any access from outside the local network until a private password was set. Less convenient for the user, but such is the price of keeping out bandits.
Just make a first installation wizard that makes the device work which demands a proper password set. We used to had routers with default (guessable) password before this practice became common. Wont help against an user entering weak user/pass combo’s.
I.e. with the camera no mefia stream if the installation wizard isnt completed.
Indeed; most end users probably don’t care about their camera being part of a botnet as long as it still works. As a result, the manufacturer doesn’t care either.
So while I disagree with destroying other people’s property, I think the malware bricking those cameras is perhaps the lesser of two evils; the consumer is pissed because their expensive camera stopped working, and the manufacturer gets a bad reputation and has to eat the cost of warranty replacements. Eventually, they will start to care about security of go out of business.
About consumers not wanting IoT devices after such an experience; if they are incapable of changing a default password, it’s better for all of us if they don’t have such things.
You don’t get Lazy coders, I don’t think I’ve ever met one, and I’ve been a coder for over 25 years. What you get is a mix of inexperienced coders given a task that they are not given enough time to prepare for, plan, research and test their implementation. And even experienced coders can fall foul of this. Boss: “Got a quick project for you, company X needs a web camera distro like yesterday, you got till Friday as I only quoted them 3 days work”…….
I am also a coder and I don’t care what line of work you are in there is always going to be lazy people cutting corners. I do agree though that it is more likely that they have been given unreasonable deadlines etc. I probably shouldn’t have said lazy coders on this occasion.
Laziness is everywhere, in every single field. It is where immaturity, selfishness, and pride walk hand in hand, saying “I don’t want to do this, I shouldn’t have to, and nobody has any right to make me, even myself.” :sigh: Lordy, but do I hate it when I see myself being lazy.
I agree I’ve written sloppy code just to get something running it wasn’t a commercial product but I know I could have done a better job but because of time restrains I took the easiest route. If I was selling something I would try my up most never to be lazy but some people working for companies etc may not have the same drive to make the company look good as I would for my freelance work.