If it were sixty years ago, and you were trying to keep a secret, you’d be justifiably glad that [Ben North] hadn’t traveled back in time with his Raspberry-Pi-and-FPGA code-breaking machine.
We’ve seen a lot of Enigma builds here at Hackaday — the World War II era encryption machine captured our readers’ imaginations. But perhaps the more important machines to come out of cryptanalysis during that era were Turing’s electromechanical Bombe, because it cracked Enigma, and the vacuum-tube-based Colossus, because it is one of the first programmable electronic digital computers.
[Ben]’s build combines his explorations into old-school cryptanalysis with a practical learning project for FPGAs. If you’re interested in either of the above, give it a look. You can start out with his Python implementations of Colossus to get your foot in the door, and then move on to his GitHub repository for the FPGA nitty-gritty.
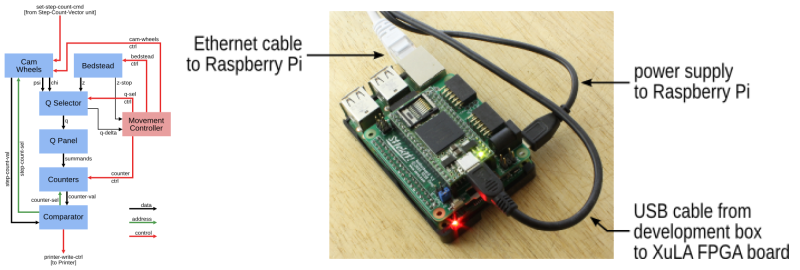
It’s also a cool example of a use for the XuLA2 FPGA board and its companion StickIt board that plug straight into a Raspberry Pi for programming and support. We haven’t seen many projects using these since we first heard about them in 2012. This VirtualBoy hack jumped out at us, however. It looks like a nice platform. Anyone else out there using one?













Thanks Mr Williams for the insightful aspects of different incription methods! For most people It’s hard to appreciate the amount of thought that goes into those machines functionality. It just reminds me of when dad used to give me his key card when I was a kid and I would run around in digital corporation… I got to see the old hard drives that were hanging on a wall ,they were the size of a 60″ flat screen. To see what they were and what they are now it’s come a long way…!!
So far, it´s an editorial choice. When you write “We’ve seen a lot of Enigma builds here at Hackaday — the World War II era encryption machine captured our readers’ imaginations” you are actually transposing your obsessions on us, readers.
They’re not wrong though. The Enigma machine was, well, an enigma of it’s time, and still stands to show how complex cryptology can be. And sure, maybe they are influencing us just by making that statement, but at the same time, anything you say to anyone can often influence them to become exactly that. It’s not a crime to make a statement about someone else (in most cases), it’s up to person/people being talked about to decide how they really feel. If you easily accept what someone else says about you as truth, then that’s your fault, not theirs.
It also helps that the Enigma design has flaws that let everyone in at pretty much every level of education. The calibre of the people involved were the best several countries could produce and the stakes could not have been higher. A more modern obsolete cipher – DES appears to have been optimised for protection against attacks that weren’t publicly known. It’s too advanced, too theoretical and stories about it have too few nazis.
Re: projecting: We’re rubber, you’re glue!!
Seriously, though, the majority of what we write up for the blog is sent in to us by either the hackers or our readers (or our readers who are hackers) before they’re read by the editors (who are all Hackaday readers and hackers) and written up for you, the readers, and the hackers. We certainly select, but we also reflect.
Incestuous? Ouroborussian? Or just a positive feedback loop? Anyway, in the wise words of John Lennon, “I am he as you are he as you are me and we are all together. I am the walrus, coo coo cachoo.”
Dig?
Above claim does not seem to be statistically valid.
Recommendation, ignore until validated, tag author as suspect.