A couple of weeks back a report came out where [Tavis Ormandy], a widely known security researcher for Google Project-Zero, showed how it was possible to abuse Lastpass RPC commands and steal user passwords. Irony is… Lastpass is a software designed to keep all your passwords safe and it’s designed in a way that even they can’t access your passwords, the passwords are stored locally using strong cryptography, only you can access them via a master-key. Storing all your passwords in only place has its downfalls. By the way, there is no proof or suggestion that this bug was abused by anyone, so if you use Lastpass don’t worry just yet.
But it got me thinking, how worried and how paranoid should a regular Internet user should be about his password? How many of us have their account details exposed somewhere online? If you’ve been around long enough, odds are you have at least a couple of accounts on some major Internet-based companies. Don’t go rushing into the Dark Web and try to find if your account details are being sold. The easiest way to get your paranoia started is to visit Have I Been Pwned. For those who never heard about it, it’s a website created by [Troy Hunt], a well-known security professional. It keeps track of all known public security breaches he can get his hands on and provides an answer to a simple question: “Was my account in any major data leak?” Let’s take a look.
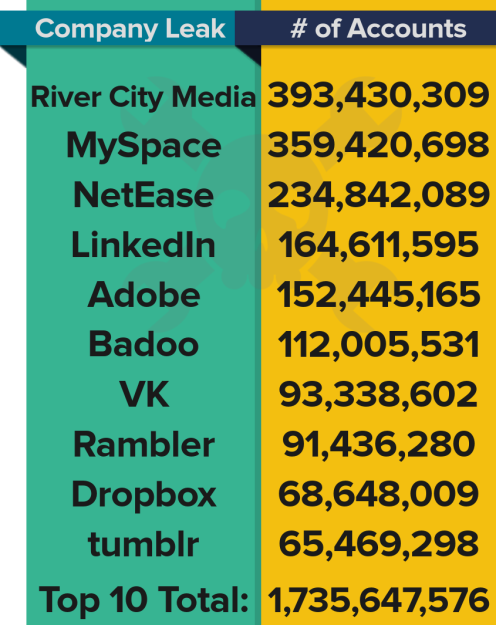 Yes. Yes it was. One of my oldest accounts was already involved in 5 major leaks and 1 minor leak. Some of them contain pretty sensitive information (no, I did not have an Ashley Madison account). The website claims to have logged over a staggering 2.6 Billion accounts. Notice the B in Billion. That’s more accounts than the entire human population in 1950. Of course, a lot of those accounts overlap and some that I examined are not 100% accurate but it is still a very high number.
Yes. Yes it was. One of my oldest accounts was already involved in 5 major leaks and 1 minor leak. Some of them contain pretty sensitive information (no, I did not have an Ashley Madison account). The website claims to have logged over a staggering 2.6 Billion accounts. Notice the B in Billion. That’s more accounts than the entire human population in 1950. Of course, a lot of those accounts overlap and some that I examined are not 100% accurate but it is still a very high number.
Here you can see the top ten sites to leak passwords.
Does Someone Know My Password?
Notice that the Yahoo breach is not there, add 1 Billion accounts more, plus another 500 Million on another Yahoo breach. Does this mean that the attackers automatically have my password? Well, it’s not that easy.
When you create an account somewhere and send in your data, your password is not (hopefully) stored in clear text. Usually it is not stored at all, only an irreversible hash representation of it. In a nutshell, instead of storing the plain text password, a cryptographic hash function is used to calculate a value based on your password and this is value is what gets stored. There is no way to reverse the process and get the password from the stored value. This is the good news.
The bad news is that the hash function chosen by the website can be critical for your security in the event of a data leak and you have no control over that. Despite the fact there is no way for an attacker to reverse a cryptographic hash function, it is pretty easy to test if a given password matches a given hash function output value. This is a process known as brute-forcing; a program runs every possible combination of passwords through the algorithm and compares it to the leaked hash value. If they match, they know your password. This is why longer passwords with more character variety (punctuation, capitalization, etc.) is universally recommended — it’s harder to brute force.
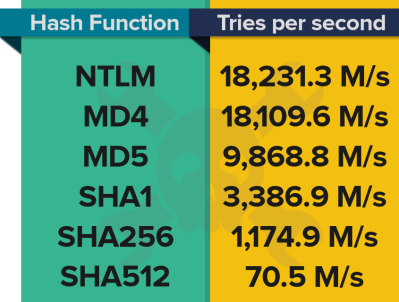 Just as a reference, an attacker with an already outdated AMD HD 5970 graphics card could brute force different hash function implementations at the speeds shown here in millions of tries per second.
Just as a reference, an attacker with an already outdated AMD HD 5970 graphics card could brute force different hash function implementations at the speeds shown here in millions of tries per second.
As you can see, a website that chooses the right hash function to store its passwords can dramatically reduce the speed at which a brute force attack can run by several orders of magnitude (in case of a leak). These numbers represent the attacker using just one, fan cooled, graphics card. Imagine using a data center, refrigerated by 1.7 Million gallons of water, like NSA Utah Data Center. But let’s not dwell into state sponsored attacks.
The hash function can (and should) be complemented by using what is called a salt. A salt is essentially a random number ‘added’ to the password before the hash function runs. This ensures that the same passwords result in a different hash output values, so that if an attacker cracks any given password in a list other users that share that password are not affected since their salt is different. This adds an additional layer of security.
Not all leaks are alike in severity. For example, The NetEase leak contained clear-text passwords, pretty much as bad as it gets. The Yahoo leak contained some MD5 hashes. The LinkedIn leak contained SHA-1 hashed passwords in which no salt was used. The following days more than 90% of all passwords had been cracked. The Dropbox leak had usernames and salted hashes of passwords, half of them SHA1, half of them bcrypt, which is pretty good given the circumstances. Leaks security impact mileage varies a lot.
So What Can You Do? Trust No One.
 It’s clear that you cannot trust any website when providing your password since you usually have no choice or knowledge on how they will handle it. Since you can’t enforce any website into safely storing your password, what can you effectively do? Well, you can stop using 123456 as a password. And I don’t mean use the more secure version, 123456789, either. You! Yes, you!
It’s clear that you cannot trust any website when providing your password since you usually have no choice or knowledge on how they will handle it. Since you can’t enforce any website into safely storing your password, what can you effectively do? Well, you can stop using 123456 as a password. And I don’t mean use the more secure version, 123456789, either. You! Yes, you!
I know, I know, Hackaday readers are an informed audience and surely have not chosen any password in the 2016 most common passwords but if this warning worked for one person that’s already worth the pun. There is just no way to believe that 17% of the folks reading this right now use them. Right?
No matter how good the algorithms are and how they are used, no security can protect the users from their own selfs. Can you answer this in all honesty that you have never had a Top 25 password?
- Don’t choose obvious passwords. Really don’t. Even if you think no one cares about you or your particular account and you’ll never be a target of a malicious attacker. This include words, names, dates, phone numbers. Ideally use lower/upper case letters with numbers with 10 or more chars.
- Don’t choose obvious security answers either. What good is it a 30 chars long password when your security question is your mothers maiden name?
Since you can’t control how passwords are stored, don’t use the same password for all your accounts. This one can get tricky. It can be hard to remember that extra secure password, but chose one different for every account? That’s just too hard. In case you don’t happen to have photographic memory, you can reduce the number of passwords you need to remember by categorizing your accounts into different types. Less sensitive accounts can have an easier to remember password, but this does not mean 123456 is acceptable.
- When possible, use two factor authentication (2FA). An increasing number of websites already provide 2FA, either via email or SMS. This can drastically reduce the impact of a stolen/leaked password. Consider using a hardware token in critical accounts, like Yubikey.
- Check online for any leaks that might have affected you. Change your passwords accordingly. If you used it on multiple websites, they too must be changed.
Some say to use a password manager. I must admit I dislike putting all my eggs in the same basket. It has advantages and disadvantages, you should definitely think about it and make an informed decision if this is right for you.
My Advice: Do Your Own Thing
When writing this article I keep thinking common sense. But common sense is not enough. Working in the security industry I know how hard it can be implementing an effective password policy in a company. It’s easy to talk about in theory, and a pain to approach in practice. If you make it too complicated, you’ll start seeing post-it notes appearing everywhere. Make it too simple, and successful brute-force attacks start showing up like mushrooms.
My advice is to spend some time thinking about your passwords and find your own thing. What’s your own thing? For some it can be the way that they pronounce their password letters. Despite being random, choosing passwords with some rhyme or musicality when read results in something that sticks in your head. For others it might be invented words from childhood. Throw in some numbers you know but aren’t public or attached to your person. Choose your own sign or punctuation char(s) to mix in.
I understand that this might sound a bit vague but it works. For this to work, it has to be vague, otherwise it’s my thing, not yours (and will probably end up coded somewhere in John-the-Ripper rules). I’ve seen this method turn a room of people into random password generators in less than half an hour but, as everything, it’s takes some persistence. Anyway, my advice is my own, I’m pretty sure a lot of you disagree with the method.
Goldfish Memory
“Good passwords are hard to memorize. I’ll just write them down on a piece of paper.”
Well, there are worst things to do. I mean, where do you put your credit card? If you really can’t memorize it, sure, write it down and keep it safe, like in your wallet. The keep it safe part is important, you don’t leave your credit card around in public places right? I bet you don’t tape it underneath your keyboard either. Over fifteen years ago [Bruce Schneier] saw this coming. Keep a duplicate copy somewhere really safe, like an actual safe. Plan ahead so that if someone steals your wallet or wherever you keep your passwords, you can rapidly change them.
The Future
The future of passwords and overall authentication mechanisms is widely debated. Some say passwords are dead and the future is biometrics. Hackaday has been known to argue against that. Some, like PayPal, say traditional biometrics aren’t the way but an easier to use, “Embeddable, Injectable and Ingestible Device” solution is ideal. What if you could authenticate just by thinking about it? And how would that unique identifiable data would be stored? Would we gain security or just trade the challenges we face now for another set of challenges?
In any case, remember, “password” is not a good password.
















“An increasing number of websites already provide 2FA, either via email or SMS.”
… and every single one of them should eat flaming death – U2F, TOTP or f* your so-called “2FA”.
Slight hint: where exactly does the second-factor email or SMS end up? Oh, it’s almost certainly the same device[*], quite likely the same browser you are trying to log in from in the first place! Really good separation, really good.
[*] Maybe, just maybe not so much for text, although that “maybe” is getting pretty thin these days.
You do know that, if someone steals a password database, your phone doesn’t magically disappear out of your pocket and into theirs, don’t you?
Simple definition for 2FA: authentication based on something you know and something you have. It is a fairly common occurrence for a) you lose your phone (or email or whatever) or b) someone breaks your password. It is far less likely that a & b happen at the same time, unless you are taping your password to the back of your phone, which you should probably stop doing.
This is one of my favorite articles for explaining why SMS, for instance, shouldn’t be used as 2FA: https://www.theverge.com/a/anatomy-of-a-hack
Your phone doesn’t have to disappear out of your pocket for someone to be able to receive your SMS messages. Personally, I don’t entirely trust services that offer 2FA through SMS only. OTP, and preferably U2F, are the better choices.
I use a burner “Dumb” phone for the purposes of 2FA and if I think my password is compromised then my 2FA burner SMS phone is presumably compromised (Thinking in worst case terms, just incase).
I change passwords, then buy a new phone, then change my password again whilst changing the SMS number and then burn the burner phone…. Just incase.
‘I use a burner “Dumb” phone ‘ – I mean: ‘a SEPARATE burner “Dumb” phone’
so every time you change a password it costs you $10?
Nope, It only costs $10 if I suspect being hacked…. The phone is reusable… Until hacked as someone may already try stealing/cloning the phone/sim. By having everything different after a breach will only leave most amature attackers confused and they’ll give up.
You just highlighted why 2FA is so good. When it’s a legit user, he will have both halves of his login. When it’s an attacker, he will probably not have both halves.
The scenario where your comment makes sense is when a mobile device is lost or stolen. For that case, though, there are still ways to protect, like a password protected device, or the fingerprint scanner.
I use a waterfall method – lets say I start off with passwordA on all accounts, high priority account, medium priority account, low priority account.
When I come to updating my accounts passwords, I create a new password for the High account, PasswordB
Next time I change my account I create PasswordC for the High Account, the Medium account becomes PasswordB and Low remains as PasswordA
and so on,
PasswordD for High, PasswordC becomes the Medium Accounts password, PasswordB becomes the Low Account.
All the passwords shuffle down in priority,
So why do this, because you only have one new password to remember each time, and they ALL get complex passwords
2FA is good but not all sites offer this opportunity. For me this article – https://thebestvpn.com/password-generator/ – brought an enlightment. Now I prefer ‘pass phrase’ to those generated passwords and keep them in managers. btw I don`t belive in the story with Lastpass.
Websites that allow millions of password retries every second are the first problem. If you limit three failed logins with a one minute timer between each failed attempt, it doesn’t matter if a hacker can compute millions or billions of passwords per second.
I do not think many website would allow this. Bandwith alone would make this kind of attack rather hard.
Milions tries per second is when you can make offline attack and website can not protect you from these if they already stolen hashed passwords. They could make it more difficult using bcrypt, or other similar methods, but it doesn’t protect simple password like 123456.
That methodology thwarts online logins to the account, but if the site is breached and the attacker obtains the hashes of passwords…offline brute-forcing goes as fast as the cracking rig can crank out strings.
If your website allows millions of attempts per second, you have Amazon’s pipes. Not AWS pipes, but Amazon.com pipes. I’m pretty sure this has more to do with offline cracking, where the hash is somehow obtained.
Presented with such a secure website, that is, one which time-limits attempts, why wouldn’t the hacker simply cycle accounts first then passwords?
For example:
password1 account1
password1 account2
password1 account3
….
password2 account1
password2 account2
…
By the time PASSWORD1 was attempted on all the accounts, the timer would be expired and he could then proceed to the next password.
No way for the website to protect against this.
Websites I’ve built often put timers on the IP address. After some number of failed attempts, *any* attempt from that IP address will be denied. Not blocked since you don’t want them to know it happened, but simply any login attempt will be told it failed. The account cycling method is a clever one but sites that watch *where* the attack comes from won’t be fooled.
Botnet. From my logs, most password brute force attempts these days come from botnets .
In companies is very common to have IT policies that requires you to change your password often and forces you to use combinations of numbers, capitals, etc. As a side effect no one can memorize so many passwords and then the most human-expected behavior is to write the passwords on a sticky note glued at the monitor.
This is just like make temper on steel! the most hard you get, the most fragile it is.
Apple are the biggest culprits for this.
When you have several devices it’s a royal pain at password update time. :(
Take the password (example):
FTW62ML1C292FGTBRVRTW17RBBL18HJHXJC55BVR2VTR8BTVCR(Tack two phone numbers or something to make another twenty two characters).!
Total of 66 characters or excluding the .! from the end is 64 (That is a 512bit password, larger if UTF).
Trust, with practice, you’ll remember the whole of it ready to use it.
Whenever a password change is needed, just write the offset on a stickie:
7-20AM – check windows .!
That will remind you your password is currently:
1C292FGTBRVRT.!
Rinse, create such rolling variances for various websites etc, repeat….
Who can extract such a password creating password from a brain?…. Even with the obligatory KXCD quote of beating it out of someone…. The fear and agony will only make it fade due to the sheer length!!!!
Blah, Blah,
And many other tequniques to make the password harder to guess but easy-ish for you to remember!!!
Certainly writing passwords on a sticky note is a terrible practice if the point is to try and keep people out of your accounts at work. If I do it at home because some site insisted I change my password frequently enough – and I used really hard to guess random-ish ones as experts suggest, then why is that a problem? If you broke into my house, I have much bigger things to worry about than a thief logging into my computer and looking at my Amazon purchase record.
Don’t bother making up obscure words, just use phrases without spaces to give passwords as long as you like and easy to remember. For instance “Theboystoodontheburningdeck” will be rated by all the password evaluation sites I’ve tried as “Strong” – you can match phrases to the sites you use them with and use misquotes, odd spellings, numbers or whatever to defeat a hypothetical attack from someone armed with a dictionary of quotations.
Running a quotation dictionary with l33t substitutions is as trivial as running a regular dictionary attack.
That is false. If my password is Cottoncandy1sgross, that single substitution dramatically increases the password space. It is anything but trivial to iterate through all the substitutions for all of your dictionary words
C0ttoncandyisgross
C0ttonc@ndyisgross
Cottoncandyisgr0ss
C0tt0ncandyisgr0ss
Cottoncandyisgro55
etc.
Substitutions are only “trivial” for short dictionary passwords. It adds up quickly for even moderate passphrases.
Okay, immediately after posting I see you were addressing quotations. I suppose if that is the only methodology you are taking then you are correct, you would be able to crack the password. But you could say the same about any themed dictionary (industry, sports, pop culture). Unless you’re hacking the English or Theater department at the local university, that is probably not the angle most people would take.
I intended to imply “with l33t substitutions” on the end of the sentence too.
But anyway, yes, you’re getting it, sports, pop culture, anything ever put into print or memed around by any method, don’t use it as a password.
Probably the top 10,000+ sayings are all prehashed in various cyphers and it’s a simple game of “snap” for the “career” attacker, whatever hat worn.
Yah, right. badboys…..
moooltipass!
on a more serious note, we have a very nice collection of breaches that happened in the last months on our repo: https://github.com/limpkin/mooltipass
If you really care about your security, Mooltipass is your best choice. Using the same password everywhere, no matter how complicated, is a bad idea. Remembering secure passwords for dozens of sites is beyond most people, and changing those passwords regularly is a horror to even think of. That means you need a single place to store your passwords. The problem with software password managers is that they ALL are vulnerable. Simply adding a keystroke recorder will easily get your master key, and easily steal ALL your passwords. The Mooltipass is hardware. It will not hand over ANY passwords unless if you tell it to on the device itself. No remote hacker can access your passwords, unless if you’re foolish enough to allow it. Even then, they could only get one password at a time. There is nothing 100% secure, and usually more secure solutions are more cumbersome, and less likely to be used. The Mooltipass is VERY easy to use. They need to polish their software a bit, but they’re busy doing just that. With an early copy of their software, it’s VERY usable. I loved the concept of Mooltipass ever since I heard of it, and the reality is just as encouraging.
Yubikey here.
Moooltipass is not the best solution, just one with a different set of trade-offs. None I can deal with.
https://sd.keepcalm-o-matic.co.uk/i/keep-calm-and-i-have-the-solution-2.png
“Assume the hacker knows your formula” only makes sense if the formula only slightly modifies a low entropy base password.
The best REAL WORLD solution would:
A – Minimize the amount of information required to remember
B – Work equally good for one website as 10,000.
C – Automatically change passwords with time.
D – Generate unique passwords for each website
E – Not require hardware which can get lost or die.
F – A second password is difficult to reconstruct from one known password.
G – Anonymity and independance from a service
Here’s what I propose:
1. Start with a TRULY randomly selected ~13 character base ‘word’ (e.g. ‘6x#$5ksuI2DD)
2. A formula (could be randomly selected as well) changes characters in the base ‘word’. This could be something as simple as shifting every third digit right by the last digit of the year, or inserting character “&” after X digits (X being now many characters there are in the website URL), or add all numerical digits and place that number to the same digit number, etc.
3. The formula should be such that there is some level of recursion. For example, the order of the above three examples give different results.
This should tick all the boxes.
Well 1. fails B already.
How so?
The idea is that the formula changes the resulting password with a minimum of one time and one account/website factor. So regardless of how many websites need a password, you only need to remember the base word and formula. So it scales.
Doesn’t solve the dumb rule problem, can’t use $, cant use # etc.
Are you talking about each individual website’s rules regarding valid characters?
Why couldn’t you just eliminate the illegal characters of a generated password or replace them with a, b, c, etc?
If a large portion of the generated password was illegal characters, it would be an issue. Passwords like abcdef7gh3i45. Statistically speaking though, enough legal digits of the generated password would remain to ensure a secure password.
I guess you could also replace them with only the alphanumeric digits of your original password.
e.g. If the generated password was ‘6x#$5ksuI2DD, but the site only accepts letters and numbers… it becomes 66xx55ksuI2DD. Although there’s duplicate numbers, good luck writing a program which could reduce the entropy there.
In case it wasn’t clear, the base word and formula are the only things the person has to remember. The formula is applied to the base word in the user’s head at the time of password creation and login.
KeePassX in a ownCloud is what I do. Works even on my Phone.
I guess for the less paranoid Dropbox could substitute ownCloud.
Does nobody remember Megaupload? Sheesh.
There is also a keepass web app:
https://keeweb.info/
Ok Keepass on an USB stick (I’ve it always on me, of course).
How secure are the router passwords that use the “easy set up” where you click the button and it gives out a string that is difficult to remember?
I tell my neighbors to make up there own “random password” vs. the router’s.
Nevermind, there are plenty of websites that just answered my question.
Thanks for sharing……….
Write the passwords with a onetime pad hide 2 keys keep passwords in plain sight
I’m making a thing to help! https://hackaday.io/project/3555-zamek-the-offline-pocket-password-manager
Hardware is done; is there anyone experienced in plastic case design to help me get a couple molds off to china and start getting these things vetted by security researchers?
>>Good passwords are hard to memorize.
BS
That’s one of the biggest disservices you can tell anyone and perpetuate in articles. ‘Good’ passwords are more than just a random string of characters. As you pointed out ‘good’ passwords in the form of truly random characters are almost as dangerous as 123456 since people stick them under the keyboard. If you learn the common memorization trick of using a familiar building/room they become easier but a 15 character phrase isn’t hard to remember if you pick the right 15 characters. Whether its your favorite jingle or the names and numbers of favorite sports players, winning score of major sporting events, anyone can come up with a computationally difficult, but still memorable passphrase. Just don’t pick information tied to you (birthdays, anniversaries, your high school team / jersey) but even those will be hard for non-targeted attackers.
Far more dangerous is poor implementation on the server side or limitations in the characters used. Make encryption easy for the end user and everyone benefits.
last time i went to change my paypal password, i noticed that the max password length is very very short. i wanted to change it to a longer password, and apparently you cant. you would think a financial institution would let me have passwords of absurd length.
password rules are also kind of ludicrous, id prefer everyone just push for longer passwords rather than more character complexity. go to more of a pass phase type format. even considering dictionary attacks, you can think of every word in the password as a base length-of-dictionary number and if you have 10 words thats a lot of entropy. then you add on the human tendency to corrupt the english language or spam characters in wierd places and you got something that confuses the hell out of password hackers.
eBay are the same … and it was this reason I closed my account with them.
I came to the conclusion that they thought security was a joke. Now, on a site like this it’s annoying, but not a big issue if someone broke into my account, there is nothing personal there, worst they can do is compromise the files I have stored on projects here, and that will not compromise the copies I have here.
eBay/Paypal, that’s a different matter. You could do severe financial harm to someone by breaking into their account and playing around, which is why I left them out of principle.
Undoubtedly protecting their bottom line / brand name.
Longer passwords are obviously more secure but people can’t remember them so they get their account locked and either tie up tech support or complain on social media hurting their image. 20 Characters (paypals current max) is still pretty long. 10-12 is probably what your average script kiddie can reasonably crack (I’d love to hear if this is out dated) and with easy password resets not likely to be the weakest link in the chain.
Can’t imagine lost passwords cost companies anything.
Handling the process to revert all damage done would be much worse, right?
I think the truth is that the current system is more than tolerable.
10-12 characters are crackable? When they can do it off-line and the password starts with a low entropy word and only makes slight modifications, right?
They do when you have to spend man hours helping people recover them.
hackaday.io devs should take note of this.
When I first signed up, it rejected my usual fairly secure password which had various punctuation marks in it. I had to revert to an older, less secure alphanumeric-only password.
There’s an option to log in via Github, not sure if it is possible to retroactively log in that way and link it to my old account since Github uses the more secure newer password, but for now I always find muscle memory trying out the newer password, giving me a rejection, and me then “remembering” that I had to use the old password for this site.
(And before people have a go at me for re-using passwords; I re-use passwords on different “classes” of site/use. Admin accounts use a different password, my local user login is different again.)
I use same base part of the password for all (most) services, but it has partition that is taken from url or system name. Addition to this I also calculate kind of checksum with my own rules. This will generate individual password for all services and even the attacker would get several passwords and figure out base+url related parts he/she would not be able to crack my checksum. With several passwords and brute force for checksum would give access to all my accounts, but that is risk I can stand.
Checksum rules that I use are easy to calculate in few seconds and those could be something like numeric combination of position on certain letter in url (position of first C) and first hexa (A-F) letter in decimals. Like example checksum for hackaday.com would be 310 where 3 is position of C and 10 for A after hex to dec conversion. These are something that can be easily invented and no one cannot reverse calculate how I ended up to 310 even several passwords would be available in plain text.
When I change passwords I generate new base part, change url part and generate new checksumrules. I had same passwords since 2011, but thanks to Dropbox and LinkedIn I had to change my passwords. But it was about time.
Have tiers. Nobody can remember 100 passwords, so keep it to three or four.
Different websites have different rules, so try to come up with passwords that will work in most places. E.g. correcthorsebatterystaple wont work on lots of sites. Use around 8 to 12 chars, with letters and numbers and capitals and special chars.
Dont try to make it memorable. Thats too hard. Generate a random string. Make some adjustments to help it roll of the tongue a bit. Then write it on a piece of paper until you fill up the sheet. Destroy the sheet. Two days later, do it again. One week later, do it again. You will remember it just fine.
You’ll end up with just a few high-entropy reusable passwords committed to memory properly.
I think my password, 6969Wombatantidisestab|_ishmentarianismroDinia420, is pretty safe.
Indeed it may have been
instead of 12345678……2444666668888888
(1 two, 3 fours, 5 sixes and 7 eights)
Ditch the password. A solution exist that is more than 25 years old: X.509 client certificates.
The technology is already in place, but the UI is beyond miserable.
The main rule is: length. Jeff Atwood has a great post on this from both the user and server perspective. https://blog.codinghorror.com/password-rules-are-bullshit.
The XKCD “correct horse battery staple” method still looks useful for now if the string is made longer and with some transformations e.g. “leaflet nuggets rushing adequate breathing44 spiderdonkeytable 99##”.
XKCD’s four-word example only has 44bits IF they’re randomly pulled from a 2k word library.
Entropy is much much lower if the words are user-selected though. Entropy also tanks because people will not use words that are hard to spell or remember. i.e. fluorescentconscienceconvalesceCzechoslovakia
A password with seven random keyboard entries actually has 46bits of entropy without those exceptions.
Memorizing four or more RANDOMLY selected words and their order, for multiple websites is damn near impossible.
XKCD’s solution is not better than passw0rd1 if 90% of users instead select ThisIsMyPassword.
KnowwhatImean?
My “solution” is as follows. KeePass wallet, with a very strong, randomized password that I committed to memory. This is stored on a server at my house with dynamic dns and a lowprivileged scp account that can pull it down. I then use the winscp plugin for keepass to pull down and sync with this wallet. For Android I use the very excellent (and free) Keepass2Android that include scp functionality. Both the windows version and the Android version can use a local cached copy if my server goes down. The keepass wallet supports syncing if the wallet changes on another machine. For linux, I had a bash script that scp’s down the file and then I open it with keepass (syncing is not easily possible in this scenario). I also have a couple InputSticks so I can have my phone type a password to a computer via KeePass2Android.
The above is the technical stuff of the storage. This allows me to generate random, complex passwords for every website that are easy to change if they get compromised, with limited vectors for attack (at least, unlike Last Pass it isn’t prone to browser JS attacks, and I’m not stuck trusting Last Pass to not implement backdooring). To further muddy the water I have a Blur (dnt.abine.com) account that allows me to generate randomized, unique email accounts for every account, so even if my account is compromised the attack won’t be able to link that identity to anything else (sans other data related to the account). This constitutes a pretty secure setup in my opinion. I also use multi-factor whenever I can, though most implementations are critically flawed in that their forgotten password functionality completely bypasses multi-factor.
Couple other related notes. If you use a setup like above, make sure to randomize security questions. Also make sure to setup a proper backup solution to protect your wallet. I’ve had my wallet get corrupted once (in four years of use). Luckily I had a cloud backup from the night before. Make sure your backup solution also allows you to specify your own secure encryption key, so that it is harder for the back-up company (and government agents) to grab your wallet.
As a security professional, the best way to protect a password that you have to memorize, in my opinion, is to use the HorseBatteryStaple method, then make non-obvious substitutions. Providing the hashing algorithm that is stored is strong-ish, an attacker is going to resort to dictionary attacks and various dictionary munging rules. Any decent dictionary is going to try swapping characters for common “l33tspeak” alternatives, or nearby keys on the keyboard or transposing two letters near each other. Using “HorseBatteryStaple”, a dictionary attack will easily catch this phrase or “H0rs3Batt3rySt@ple23!”. What is is less likely to catch is something like: “HdrsdBdtt23!dryStdpld”. From my previous example, also note that your password will be much stronger if you put your numbers and symbols in the middle somewhere as opposed to appending or prepending them. Ultimately, do something that is unique to you and not something that is a common practice.
I just hate passwords. I wish there would be better way to authenticate the user. It’s just pain to remember all your random passwords. It’s just takes a lot of time to remember 16 char random alpha numerical passwords. Some would say use password manager. The problem is that what device I would use to store the passwords. Cloud syncing password managers are just dumb because what happens if they get hacked. Like if someone hacks in to my cloud account. It’s game over. Or if they have a warrant to let them in.. Fingerprint would solve it mostly but I don’t have fingerprint reader on every device I own. I just hate passwords.
Fingerprint readers are definitely not the answer. Even the Mythbusters could defeat several types.
Furthermore, you can’t replace your biometrics if they get stolen, and they provide no anonymity.
+1
we’d start seeing black markets for retinas, fingertips…..
What I’m finding particularly annoying in this online security theater environment of the present day…. is that it’s getting harder and harder to get accounts without other accounts, which send password resets back to those accounts… so you end up with a kind of domino chain of accounts that expose each other and can all be rolled up if a certain link in the chain proves weak.
I proceed on the basis that it’s about an annual 1 in 10 chance that my data will be compromised at a given site, online or theoretically “offline” like Target. Ergo I am very careful what I expose to who. I won’t belong to any store club or reward schemes nowadays. They end up aggregating it with your habits and payment info. It’s less about how honest and upstanding I perceive that company to be, and more about the mathematical certainty that they WILL get hacked.
I know what you’re thinking, “What can hackers possibly do with…..” Seriously,? Have you even been conscious the last 15 years? .. 2nd week in August every year you make a lot of camping related purchases, thus your residence is likely to be empty in the 3rd week. First week of may, you’re a male, but buy female related things, your wife’s birthday is in early May, and she’s between x and y years old…. Now if you’ve been stupid enough to set your password in some critical account as “C4mping12thMay” being your favorite leisure activity and wife’s bd, I don’t think it’s going to take them more than an hour to get into it. Anyway, any fragment of info gleaned about you, is a clue to be added to the “profile” that a targetted attack might use to roll up other accounts or social engineer their way into them, including “real life” utility and bank accounts.
I got dogpiled on one site for putting vague info in my profile, “We’re all friendly here” they said, but the whole internet can read it people. So yah, see my .io profile? That’s all yer getting.
You’re paranoid. Unless you’ve personally pissed off trump and got an intelligent competent human on your tail, no automated script is going to correlate all that crap to guess your password.
You know what I think would be the best way forward…
Challenge/Response public/private key authentication. You give websites your public key, they either send you a random string you paste in after you decrypt with your priv key, or to be “extra” they encrypt it with your pub and their priv, you use their known pub and your priv and decrypt and paste.
However, this would entail having trusted software on your computer or devices to help the process. You can have your priv key written out and put in a safe. You could maybe even figure offline methods, like have it on an offline device with camera and OCR which spits out the string you type.
Or we could just use the existing authentication methods that exist for DDH?
*SSH
Try PasswordWrench…
You still can use any VPN if you’re experiencing any troubles with privacy. I wouldn’t advertise any particular one, but you can choose a VPN service that will suit your needs; info on the comparison of different VPNs can be found here: https://cooltechzone.com/dot-vpn-review