To many, the Enigma machine is an enigma. But it’s really quite simple. The following is a step-by-step explanation of how it works, from the basics to the full machine.
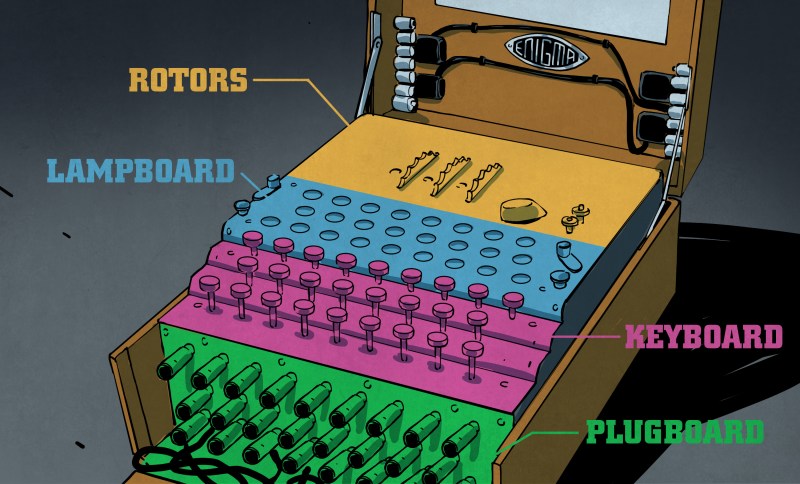
Possibly the greatest dedicated cipher machine in human history the Enigma machine is a typewriter-sized machine, with keyboard included, that the Germans used to encrypt and decrypt messages during World War II. It’s also one of the machines that the Polish Cipher Bureau and those at Britain’s Bletchley Park figured out how to decipher, or break. Most recently the story of how it was broken was the topic of the movie The Imitation Game.
Let’s start with the basics.
A Simple Substitution Cipher
Most have seen how to encrypt messages using a simple cipher like this.
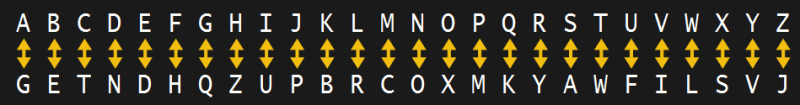
Let’s say we want to encrypt the word Hackaday. This is called the plaintext message. We’ll treat all letters as uppercase. Using the above cipher we look in the top line for the H and we substitute the letter below it, a Z. Similarly, looking for the A in the top line, we see we should substitute it with a G. The encrypted text becomes ZGTBGNGV. This is called the ciphertext. To decrypt it we do the reverse, look for each letter in the bottom row and substitute with the corresponding letter in the top row, getting HACKADAY.
That’s the very basics. Let’s take this further like the Enigma machine does.
Adding Rotors
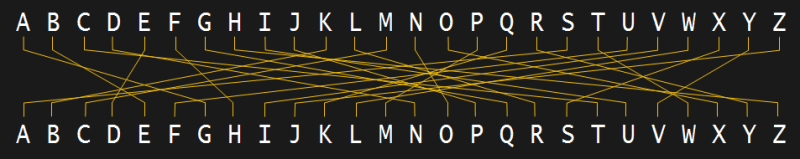
We could redraw the cipher as two alphabets with letters in alphabetical order, and draw lines between the paired letters. The effect is the same in this case. But those lines can be wires, electrically connecting each pair, which opens up the possibility of easily changing how the substitution is mapped through to the ciphertext.

The ability to change the mapping is important because once someone deduces that G is the substitution for A, they’ll know that’s true for every G in the ciphertext. An improvement would be for all those pairings to change. And even better, if they change each time a letter is encoded.
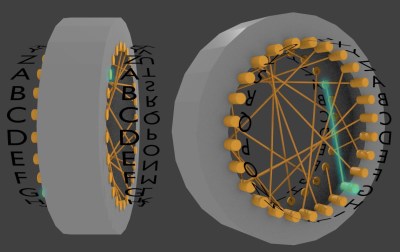
One way to easily implement that, and it’s the way it’s done in the Enigma, is to embed all that wiring in a wheel/rotor. By turning the rotor while leaving the letters stationary, the connections between letters change. After one turn, A would now be substituted with whatever Z formerly was, namely J. Repeating this step of substitution followed by turning the rotor for each letter, HACKADAY becomes ZJGZLVFA. Follow the diagram above and you notice that the first Z came from the H, but the Z in the fourth position came from the K.

In the rotor, each wire has external contact points on either end. That allows some multiple of these rotors to be put side-by-side, with adjacent contacts touching. And internally, each of the rotors are wired differently i.e. each rotor contains a different cipher. In some Enigma machines there were three rotors, and the most used was eight. As shown in the photo from inside an actual Enigma, each rotor also has an attached alphabet ring that turns with the rotor and is used to set the initial position of the rotor.
Staggering Possibilities

How many possible paths does that give us through three rotors for the letter A? Keep in mind that each rotor can be turned to any position. That means that for the first rotor there are 26 possible paths through it for A. But once we’ve followed the wire through the first rotor, there are now 26 possible paths through the second rotor. And then 26 more possible paths through the third one. The total possible number of paths for A to take through all three rotors is therefore 17,576.
26 x 26 x 26 = 17,576
As we said, each rotor is wired differently. They’re therefore given names using Roman numerals: I, II and III. But to further complicate things for anyone who might have such a machine and be trying to decrypt a message, the rotors are allowed to be moved around before use. Rotor II might be the left one, with rotor III in the middle and rotor I on the right. And to add even more possibilities, up to eight rotors were made altogether, each with their own wiring and Roman numerals: IV, V, VI, VII and VIII. The German Army and Air Force used five and the Navy used up to eight. Prior to use, for a three-rotor machine, three rotors would be selected from however many rotors were available to choose from.
Assuming we were trying to decrypt an army message, we’d have a choice out of five rotors to use for the left one, then a choice out of the four remaining rotors to use for the middle one, and then a choice out of three for the right one. That gives 60 possible ways to choose the three rotors being used for a message.
5 x 4 x 3 = 60
And since there were 17,576 possible paths a letter could take through the rotor, that gives 1,054,560 possibilities altogether.
17,576 x 60 = 1,054,560
Enigma Machines With Only Rotors
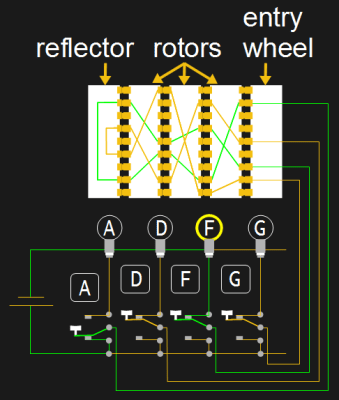
To make the Enigma easy to use, a circuit including a battery, keyboard, and light-up letters for a display were added. Shown in the illustration are just a few of the keys and lit letters, and only a few of the wires in the rotors.
One side of the battery is connected to all the lights for lighting up some letters. When the ‘A’ key is pressed, the key’s switch makes a connection with the other side of the battery. The other end of the switch goes up to connect to the entry wheel which makes electrical contact with one of the contacts on the first rotor. From there the circuit continues through the other two rotors, following the wire paths within those rotors. At the opposite end of the rotor is something called the reflector which causes the circuit to follow paths back through the rotors until it emerges back at one of contacts of the entry wheel. From there the circuit goes to the F key. Since the F key was not pressed, electrical contact is still made with the F light, completing the circuit with the battery and lighting it up. The lit F means that the key that was pressed, A, should be substituted with the letter F. The operator or someone else writes this down.
One mechanism not illustrated here is the one that causes one or more of the rotors to turn as a result of the keypress, called the turnover. The first wheel would turn one letter position for each keypress, as illustrated above with the ciphers. On some versions of the machine, the second rotor turns one position only after the first rotor has made a complete rotation. The third rotor then turns one position for every complete rotation of the second rotor. But all that varied from version to version, some rotors turning twice for each rotation of the one to the right of it.
Adding A Plug Board

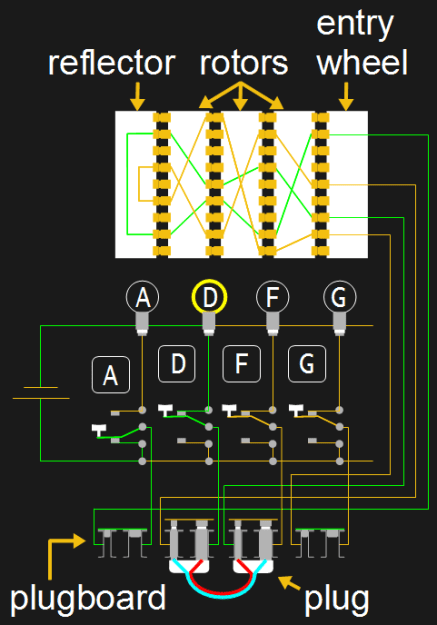
In 1930, German army versions added a plugboard, or steckerbrett. This allows letters to be swapped. In the circuit shown, D and F are swapped. When the A is pressed, as we saw above without the plugboard, the output would be F. But with the plugboard it’s D. If instead we’d swapped D with A, then the swap would have affected the circuit before going to the rotors and the rotors would have started with D. Following that wiring, the output would have been G.
Since there are 26 letters, up to 13 swaps could be done but typically only 10 were. The mathematics for figuring out the number of possible ways to connect the plugboard is a little complicated but the number is 150,738,274,937,250. Multiplying that by the other possible combinations we gave above, we get that the overall number of possible paths a letter can take to be substituted is 158,962,555,217,826,360,000.
Flaws
There were a few flaws with the way operators would use the machine, mostly failing to follow procedures. But in terms of flaws in the design of the machine, the main one had to do with the reflector.
The reflector makes the Enigma self-reciprocal. That means that, given the same starting conditions, the machine can both encrypt and decrypt. To use the example above with the plugboard, when you press A the D lights up, but press D and theA lights up. This meant that, ignoring the plugboard, a letter would never substitute itself. This fact helped codebreakers break the Enigma.
Variations
We’ve already mentioned a few variations above, such as the number of rotors, the presence of the plugboard, and the point at which rotors turn.
Another variation among different versions of machines was in the way the keyboard was connected to the entry wheel. In commercial machines they were connected as per the QWERTZ keyboard: Q-A, W-B, E-C, and so on. In military machines they were connected alphabetically: A-A, B-B, and so on.
In some versions, the reflector could also be rotated, in some cases only once before use and in other cases, automatically.
We’ve talked about setting the initial positions of the rotors. To do this, the rotors have an alphabet ring attached to them and they’d set a rotor by turning it until a desired letter appeared in a small window. However, in later versions of the machine, the alphabet ring itself could be turned separately from the wired rotor. This meant there were two things to set initially for the rotor, the alphabet ring, called the ring setting, and then the whole rotor.
Using The Enigma

With so many versions of the Enigma machine, there were plenty of different possible settings to configure before using it. Typically, both the people encrypting a message and the descryptors would have a list of settings, sometimes different ones for each day.
Some of the columns in the sample settings given here are:
- Wheel order (Walzenlage): which rotors to put in the machine. Remember, each rotor is named using a Roman numeral,
- Ring settings (Ringstellung): position of the alphabet rings with respect to the wired rotors for versions that had alphabet rings,
- Plug connections (Steckerverbindungen): which letters swap with which other letters,
The person doing the encrypting would choose random rotor positions themselves and include them at the start of the messages. During the latter part of world War II, the procedure for doing so was as follows. He’d first make up an initial start position, for example, ABC, and a message key, DEF. He’d set the rotors to ABC and type in DEF. Let’s say that encrypts to GHI. Next he’d set the rotors to the message key, DEF, and start typing the plaintext message. He’d record the output, which is the ciphertext. He’d then transmit the initial start position, ABC, the encrypted message key, GHI, and then the ciphertext.
On the receiving side, the person decrypting the message would set the rotors to the first three letters received, ABC, and type in the next three letters, GHI. That outputs DEF. Looking above you’ll see that results in the rotor settings used when encrypting the message. So he sets the rotors to DEF and starts typing the ciphertext. The output is the plaintext message.
As an interesting side note for those who’ve seen the movie, The Imitation Game, you may recall the pivotal bar scene where Alan Turing learns that one operator always transmits the same letters at the beginning of his message, rather than random ones as they were supposed to. He was referring to the randomly chosen rotor positions we talk about above.
A fun way to see all these settings being applied before use is to watch the video in our article about an amazing Enigma in a wristwatch.
ZGMMVXZGTBUOQ
Have you had any experience with Enigma machines, or done encrypting in other ways? One thing is clear, Hackaday readers and writers alike get a certain pleasure from the Enigma machine — perhaps because it’s a sort of intelligent electromechanical beast or perhaps due to the delight to be had in encrypting and decrypting messages. Maybe the why of it is one puzzle you can clear up for us in the comments below?
Here are just a few of the older creations to be found here, starting with a toy that was hacked into an Enigma machine. Then there’s this Arduino based Enigma with LEDs disguised as nixie tubes. And here again is the amazing Enigma in a wristwatch.















Thank you Poland for breaking it! https://en.wikipedia.org/wiki/Cryptanalysis_of_the_Enigma
And scant thanks they got. From the Wikipedia page on Rejewski:
“Enigma decryption, however, had become an exclusively British and American domain; the Polish mathematicians who had laid the foundations for Allied Enigma decryption were now excluded from making further contributions in this area.[88] By that time, at Bletchley Park, “very few even knew about the Polish contribution” because of the strict secrecy and the “need-to-know” principle.[85]”
My wife’s got Polish heritage and mom worked as a WAVE officer at OP-20-G.
Yes, good point. The Polish contribution was absolutely vital and paved the way for all the other work.
Emulator here : http://enigma.louisedade.co.uk/enigma.html
Honestly, the mechanics of this machine look too complicated. They should have used arduino instead.
LOL!
LOL
You are trolling me, right?
no, a 555
done on arduino several times, for example
https://meinenigma.com/meinenigma-electronic-enigma-replica/
https://www.tindie.com/products/ArduinoEnigma/arduino-enigma-i-m3-m4-machine-simulator-w-case/
http://www.stgeotronics.com/Enigma-Replica_c3.htm
:)
Maybe it looks complicated, but it’s actually really simple. I think it’s even simpler if you would use a real Enigma cause it’s pretty hard to code it on an arduino (i tried to do it but it’s very hard!).
As for how complicated the enigma models where this is just scraping the surface. During the war some sections used a reflector where the wiring could be changed. That’s what the column between ringstellung and steckerbrett shows above.
Then you have luftwaffe who used a UHR box – an external box that was in place of the plugboard and there you could turn a knob and change the plugboard to 40 different configurations so each message had one of 40 settings.
After the war enigmas where used by many governments until early 70s when it became public what Bletchley Park did during WWII.
Businesses were using Enigma-like machines even BEFORE the Nazis used them. The Americans were using them too before the Nazis, they only just kept that top secret until recently. The idea was actually envisioned by an American horse thief (Edward Hugh Hebern) while in jail back during the early 20th century. The Americans just tricked him into stealing his intellectual property and then wrapped it into national security. It’s just a natural evolution of the POTUS Jefferson Cipher Wheel (or the much earlier Alberti Cipher Disk) with the adjacent rotors changing each character in a very predictable way.
https://goo.gl/8zEQ28
I think the Enigma Machine was not as sophisticated as the Nazi’s LORENZ machines which worked in real-time and you didn’t have to copy code on paper and then type it into an Engima machine for decoding, and visa versa. But all of these machines pale to this secret communicator method which is still being used today: Lichtsprechgerät 80/80 or LiSpr80 didn’t even need encryption. But encryption could only enhance them. No one could hear it, detect it, see it, etc. U-Boat, Pill Box, and Panzer Commanders used them to talk to each other secretly from several KM’s away L.O.S. It was a Carl Zeiss evolution on Alexander Graham Bell’s Photo Phone.
Google URL Shortener screwed me on this. This is what I was trying to show:
https://image.slidesharecdn.com/day1-used-131006003623-phpapp01/95/engineering-cryptographic-applications-symmetric-encryption-27-638.jpg?cb=1381019933
One of the commercial machines was the Enigma Z30, a numbers only machine. Some were recently found in Sweden and their rotor wiring was traced.
They had ring settings for the rotors, some had lever stepping and suffered from the double stepping anomaly, others used gear stepping and did not skip numbers.
If you have a KIM Uno or another Kim 1 compatible machine, you can try a simulator I wrote in 6502 assembly
http://arduinoenigma.blogspot.com/2017/03/enigma-z30-machine-simulator-v20.html
Whilst a lot of people have heard of the Enigma system, the Tunny system (used by German high-command) is less well known for some reason, as is Tommy Flowers’ monumental work building the Collossus computer used to crack it. Collosus used vacuum valves/tubes and was orders of magnitude faster than the electromechanical Bombe used to crack Enigma. It is possibly the world’s first programmable electronic computer. Flowers actually had to buy a lot of the parts using his own money.
https://en.wikipedia.org/wiki/Tommy_Flowers
You left out the TRUE genius (and leader of hut 6) of the Bletchly Park group no one wants to talk about today. Not Tommy nor Alan either. He went on to work for our NSA’s beginnings after becoming a UK ex-pat. He went afoul of the US intel community by doing a pre-Edward Snowden kind of thing back in the 1980’s after writing an AUTHORIZED book about hut 6 and enigma machine. “THEY” made sure it only sold 900 copies – and other things. I’m trying to watch a YOUTUBE video about him called “The Codebreaker Who Hacked Hitler” it’s 46 minutes long and a excerpt from Smithsonian Channel. Alan and Tommy worked with him. He also consulted for USA’s super-secret MITRE group. I’m not mentioning his name so as to not piss off certain guys here… ;->
https://en.wikipedia.org/wiki/Mitre_Corporation
It’s not nearly as well-known, but during WWII the Swedes broke a German teleprinter encryption scheme to get warning of a possible German invasion. There’s a documentary about it linked below. If you don’t know Swedish, turn on the closed captions for English.
https://www.youtube.com/watch?v=P6Cgiz84Oys
The Polish not only played a major role in breaking Enigma, they provide the best fighter pilots of the Battle of Britain. They were shortchanged in the celebrations at the end of WWII because, as Allied leaders did nothing to prevent the brutal Soviet occupation of Poland, they did not want the extent of their perfidy to be obvious. Churchill wanted to assist them but was powerless, given how exhausted the UK was. If anything, FDR wanted the Soviet Union to grab Poland to ensure that his plan for world peace—the “three policeman” of the U.S., the U.S.S.R.—had sufficient power to impose their will on the world. He did not seem to grasp—or care—about how brutal Stalin was. It was the “peace” of a boot crushing all opposition. One of the twentieth history’s most fortuitous events was that FDR’s death in April of 1945 meant that Truman would be making decisions about a post-war world.
Here’s a documentary about those Polish pilots:
https://www.youtube.com/watch?v=ptijNcDanVw
https://www.youtube.com/watch?v=ptijNcDanVw
One of the most fortuitous events was that Truman was V.P. and not Henry A. Wallace who many suspect was working more for Stalin than FDR. (Gee this sure got off topic.)
“Possibly the greatest dedicated cipher machine in human history” – well, except for the glaring error that made it very breakable…
JohnU – +1
John please Google the American’s SIGSALY machine (aka GREEN HORNET). It was used against the Nazis and Japanese Empire successfully. Never was broken. It was devilishly encrypted speech only – used PCM. The Nazis did intercept the RF transmissions and recorded it on their new magnetic tape machines. However, they had no clue what was within this traffic. They knew it was new but didn’t have any intel on it. Turing helped the Americans develop it too. It’s amazing how well we Americans could keep secrets back then. But for some reason not so much today. :-(
https://en.wikipedia.org/wiki/File:SIGSALY.jpg
Great write up, and coincidentally I went to the museum last weekend. Luckily, the ticket can be used for free entry to the museum within the following year, as I did the same day (after lunch) and the next day.
The national museum of computing, which is next to Bletchley Park, but not officially part of it, is very recommended as well, as it holds a “almost 100% functional” replica of the Colussus, with 2500 valves.
I find it uncanny that Bletchley is home to both the Collosus and Marshall Amplification, two icons of thermonic valve wizardry.
Totally agree about the national museum of computing at Bletchley. Its a must-go.
Interesting, I didn’t know that!
I tried to find more info on Dudley Craven, the 17th year old who worked in Marshall’s shop and probably designed the first JTM45, but no luck so far.
http://www.mylespaul.com/threads/dudley-craven-ken-bran-lest-we-forget.193030/
Howdy.
Nice article, but it’s technically incorrect. There are not 26X26X26 rotor positions, due to the middle rotor “double stepping”.
Wikipedia states: “With three wheels and only single notches in the first and second wheels, the machine had a period of 26×25×26 = 16,900 (not 26×26×26, because of double-stepping).”
You can read about it here: https://web.archive.org/web/20110719081659/http://www.eclipse.net/~dhamer/downloads/rotorpdf.zip
So your entire calculation on total possible variations is wrong.
Hi, If the middle rotor steps twice in a full revolution of the rightmost rotor, it takes 13 full rigthmost rotor revolutions for the middle rotor to make a rotation. Therefore the period shoul be 26*13*26. Is it correct?
A very good Description how the ENIGMA worked. I’m german and I adore Alan Turing and Gordon Welchman. In a Period of more than two Years, I constructed an Electronic Turing-Welchman-Bombe. In a Presentation on YOUTUBE with the Title
“Turing Welchman Bombe Electronic Bombe” I explain Step by Step the whole Decryption Procedure. If you don’t speak german, let YOUTUBE translate it and look at the Subtitle.
A lot of Greetings from Germany
Gustav Vogels
Thou, the Enigma Machine has a flaw : A letter can never be itself, thanks to the keyboard. Alan Turing and his team built the Bombe Machine which uses this flaw and broke the Enigma Codes.
and…….. I made an Enigma Machine online …. just a bit crazier…. plus, a character can be encrypted as itself.
here:
https://memo2007ultra.wixsite.com/memo2007ultra/academic-2017-computer-enigma
hey everybody.
Does anybody know what is the logic of the rotors internal wirings mapping?
i mean there is a lots of wire mapping orders on the internet but i couldn’t find the logic of them in order to make one.
Hi, i am trying to make an Enigma essay for school, but i don’t know where to find information on how a printing Enigma (like Die Handelsmaschine, Schreibende Enigma and the Enigma H) works. Can someone send my a link? If you sended a link then i have to say: “Thank you!!!”, but even if you didn’t send a link thank you for reading this :).
Thou, the Original Enigma Machine has a flaw :
A letter can never be itself, thanks to the keyboard and the Pairing mechanism.
Alan Turing and his team built the Bombe Machine which uses this flaw and broke the Enigma Codes.
and…….. I made an Enigma Machine online …. just a bit crazier…. plus, a character can be encrypted as itself.
64 keys instead of 26 ? no prob~
here:
https://memo2007ultra.wixsite.com/m27u-l2016/cryptography-64keyenigmamachine3
have fun OwO