Over the last few years one thing has become abundantly clear: hackers love cramming the Raspberry Pi into stuff. From classic game systems to mirrors, there’s few places that haven’t been invaded by everyone’s favorite Linux SBC. From the inspired to the bizarre, we’ve brought such projects to your attention with minimal editorialization. As we’ve said before: it’s not the job of Hackaday to ask why, we’re here to examine how.
 That said, some builds do stand out from the crowd. One such project is the “Pentesting BBU Dropbox” which [b1tbang3r] has recently posted to Hackaday.io. Noticing the battery bay in a cheap Cyberpower 350VA battery backup was just about the same size as the Raspberry Pi, he decided to convert it into a covert penetration testing device. Of course the illusion isn’t perfect as the battery backup function itself doesn’t work anymore. But if you hid this thing in an office or server room, there’s very little chance anyone would ever suspect it didn’t belong.
That said, some builds do stand out from the crowd. One such project is the “Pentesting BBU Dropbox” which [b1tbang3r] has recently posted to Hackaday.io. Noticing the battery bay in a cheap Cyberpower 350VA battery backup was just about the same size as the Raspberry Pi, he decided to convert it into a covert penetration testing device. Of course the illusion isn’t perfect as the battery backup function itself doesn’t work anymore. But if you hid this thing in an office or server room, there’s very little chance anyone would ever suspect it didn’t belong.
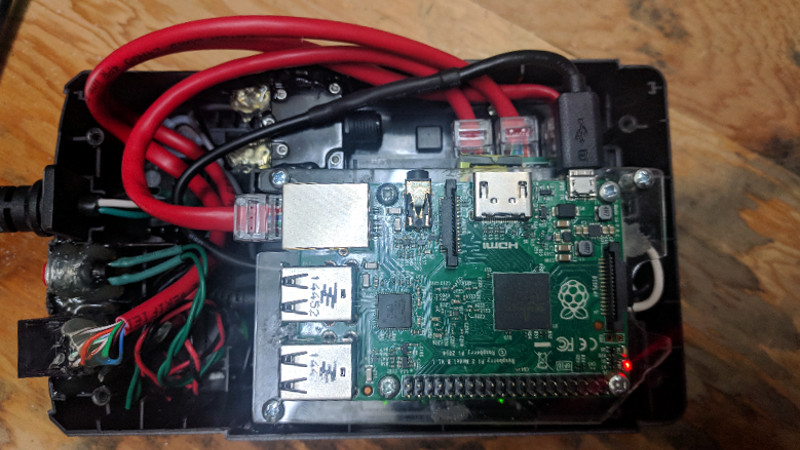
The key to the final device’s plausibility is that from stock it had dual RJ-11 jacks for analog modem surge protection. Swapping those jacks out for RJ-45 network connectors gives the BBU Dropbox an excuse to be plugged into the network. At a cursory glance, at least. Internally there is a TRENDnet Ethernet switch which allows the Pi to get on the network when an Ethernet cable is plugged into the battery backup.
We especially like the little details [b1tbang3r] put in to make the final device look as real as possible. The “Reset” button and “Wiring Fault” LED have been connected to the GPIO pins of the Pi, allowing for an exceptionally discrete user interface. For instance the LED could be setup to blink when a scan is complete, or the button could be used to wipe the device in an emergency.
This build reminds us of the Power Pwn released back in 2012 by Pwnie Express. That device was based around a relatively bulky power strip, and the only “feature” it looks like this DIY build is missing from the professional version is the $1,300 price.















Neat! With auto-ssh it can make a reverse ssh connection to your amazon server for remote access!
Pretty sure this all could’ve been done to be smaller. Cables aren’t really needed, and the full-size Pi could very well be a Zero. Unpack the switch, remove Ethernet connectors and power cables in favor of either FPCs (or some kind of smaller twisted pair), add a cheap USB-Ethernet (again, no connectors, and you might even omit Ethernet transformers on the Pi-switch path) and power the Pi from a 5V source on the board of the switch (there’s extremely likely to be one).
Alternatively, use something router-chipset-based, like Onion Omega or VoCore – router chips have built-in switches. Something like a Black Swift is both extremely small, low-power and has everything that’s needed – in fact, you should be able to preserve the battery this way.
This is a great setup for unsophisticated clients, but a good NAC setup or internal IDS could still see this. The RPi would still show up as a separate MAC on that switchport, and have its own IP that can be tracked down. How could a pentester make it even more stealthy on the wire?
Could someone get a small system powerful enough to do layer-2 bridging on the two GbE jacks, sniff the endpoint’s MAC/IP, and somehow siphon off one or more IP/port tuples to not forward to the EP but use for its own exfil channel? That way, NAC only ever detects the EP’s MAC, and an IDS thinks comms are coming from the endpoint, not some other mysterious MAC responding to ARP on the same port… “Huh. EP is powered down but the link is still up. Must be the UPS. Let’s open it up… Whaaa?”
Black Swift looks interesting, as it does have two 100Mbps Ethernet ports (less the magnetics), but that in itself would be a giveaway if the system is expecting a GbE connection to the endpoint. the MicroTik hEX might do if its not too bulky. https://mikrotik.com/product/RB750Gr3 RPis are out, even the 3B+, as they don’t have enough (or fast enough) gigabit ethernet.. Omega and VoCore are also only 10/100Mbps.
[Make it so, #1…]
Two things occur to me.
First; I haven’t seen any NAC or IDS paying much attention to speed or duplex (has anyone else?) I would think its a great way to get a buttload of false hits any time someone kinked a cable, used the wrong/old cat cable, booted to PXE, etc.
Second; Remember when people ran entire routers with hundreds of connections from commodity 486 hardware? Pepperidge Farm Remembers. You don’t need a lot of horse power if your not doing full stateful packet inspection. Just clone the MAC of the endpoint and NAT it from the device. No fancy filtering or intensive processing. The device is free to use the endpoint MAC on the wider network and traffic bound for the original endpoint is none the wiser.
Third; I’m terrible with off-by-one errors.
I’ve been searching really REALLY hard for a small SBC with dual GbE, for exactly this purpose. They are incredibly hard to come by. Probably the best I have found so far is the EspressoBin, FRDM-LS1012A, GrapeBoard (https://www.grapeboard.com/) which is currently unobtainium, or things like the Up Squared, which are pricey.
Somewhat larger would be the RMB33G (not yet available), which has expansion for WiFi cards and modems, etc.
And then as a final option, I also found a mini PCI-E to dual GbE adapter, which can be combined with the SBC of your choice (with mPCIE, obviously).
Anything I have missed?
Why not a board with a single NIC and a small switch with VLAN setup between ports?
SOHO routers are essentially this.
Mirror the LAN side ports and you’ve got no leakage of the SBC MAC.
I know I’m missing something as it is such an obvious solution, but don’t know what it is that I’m missing :)
That might work.
I had been thinking, to be really sneaky, you’d have to drop link on one port when the cable on the other is pulled. I suppose you could do that with physical switches that depower the switch hardware until both cables are plugged in..
you’ll probably find a dozen options starting from here… https://www.google.com/search?q=gigabit+ethernet+soc+evaluation+board
“But if you hid this thing in an office or server room, there’s very little chance anyone would ever suspect it didn’t belong.”
If I saw something like that in a server room I’d schedule some downtime for whatever was plugged into it and swap it out for a proper UPS solution. That thing would burn up in a minute.
that’s why they said “in an office”, not even your super duper powers of observation would notice this thing in cubicle #43 behind the filing cabinet with the “I don’t like mondays” poster on it, and can you please come back when you find the proper form to request temporary downtime on the little fan that’s plugged into it.
My coffee must be weak this morning. Why is an Ethernet switch needed to “allow the Pi to access the network”? Why not just connect the Pi directly to the network being tested?
The two RJ-45 ports on the UPS were originally a simple surge protector. The same computer that gets its power from the UPS would also route its ethernet through the UPS to the network jack on the wall. The design here is adding an additional endpoint to that, so the network wall jack would be serving both the unsuspecting endpoint (aka desktop) and the RPi running Kali. Hence, it needs a switch.
Get it now? Have another sip… :)
Totally did not think of that part of the illusion – thanks for waking me up!
“Of course the illusion isn’t perfect as the battery backup function itself doesn’t work anymore. ”
Cheap, work, don’t last. APC better.
Most UPS devices include a USB interface. This allows it to notify the connected PC when power is lost so that it can be shut down gracefully when power levels are critical. Seems like a logical next step for this already impressive build.
It would actually be kind of nice to be able to buy a computer with built in UPS and power strip. You’d never have to shut it down, you could transport it or even ship it while Linux runs the whole time.
That’s how google built out its server farm. Each motherboard had its own custom UPS to prevent hiccups.
I think it’s called a Laptop.
B^)
You can stream a *lot* of data out of an LED. Blink it fast enough and it looks solid on to the human eye. Last year Ben-Gurion University did a demo of hard drive light to drone out a window.
I’d be more surprised if the old UPS in the corner under Sharon’s desk actually still worked