Let’s not pretend we aren’t all guilty of it: at some point we’ve all connected to a public WiFi network to check our email or log into some site or service. We know the risks, we know better. But in a weak moment we can let the convenience of that public network get the better of us. What if you had a small secure router that you could use as an encrypted VPN endpoint, allowing you to connect to those enticing public networks while keeping your traffic secure? That’s precisely what [David] had in mind when he built this pint-sized solar-powered OpenWRT router.
 At the heart of this gadget is the TP-Link TL-MR3020, a tiny OpenWRT-compatible router that’s no stranger to the pages of Hackaday. Its small size and low cost have made it a natural choice for a wide array of projects, so it’s little surprise that [David] gravitated towards it. But simply getting OpenWRT installed on the MR3020 and configuring OpenVPN doesn’t exactly grant you entrance into the Hackaday Pantheon, so obviously there’s a bit more to the story.
At the heart of this gadget is the TP-Link TL-MR3020, a tiny OpenWRT-compatible router that’s no stranger to the pages of Hackaday. Its small size and low cost have made it a natural choice for a wide array of projects, so it’s little surprise that [David] gravitated towards it. But simply getting OpenWRT installed on the MR3020 and configuring OpenVPN doesn’t exactly grant you entrance into the Hackaday Pantheon, so obviously there’s a bit more to the story.
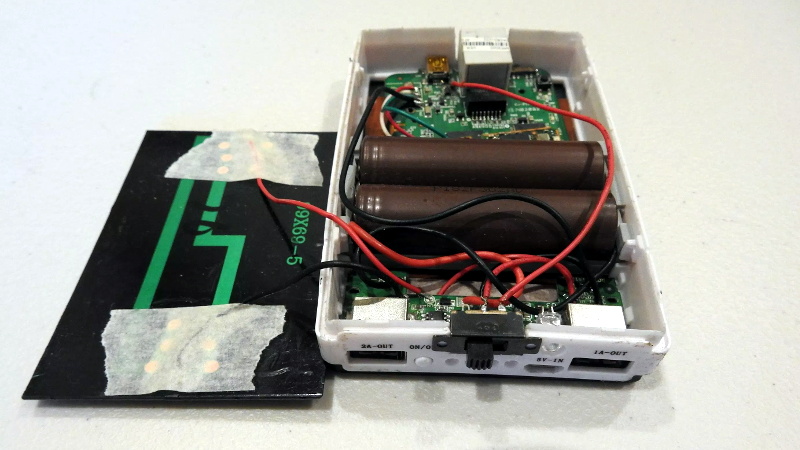
For one, [David] didn’t like the idea of a USB flash drive hanging out of the side of his router. Since the flash drive would essentially be a permanent part of the router, as it is being used to expand the rather meager internal storage of the MR3020 he decided to wack the USB end off the flash drive and solder it directly to the router’s PCB. This gave him a much cleaner looking package, but it still wasn’t as portable as he’d like.
He decided to order a solar-charged USB power bank to become the new home of his hacked MR3020. He kept the solar panel and charge controller from the original gadget, and after some researched settled on a pair of LG-HG2 3000 mAh batteries as the power source. [David] went through a few charge and discharge cycles making sure everything worked as expected before buttoning up the case. In the future he says he might transplant the electronics into a 3D printed case, but for now he’s pretty pleased with the results.
If you’d like to try your hand at hacking these popular micro routers, you’ll need to start with an OpenWRT firmware. After you’ve got a full blown Linux distro running on this little fellow, the only limitation is your own imagination.














“Let’s not pretend we aren’t all guilty of it: at some point we’ve all connected to a public WiFi network to check our email or log into some site or service. We know the risks, we know better. But in a weak moment we can let the convenience of that public network get the better of us.”
HTTPS
“For one, [David] didn’t like the idea of a USB flash drive hanging out of the side of his router.”
https://www.sandisk.com/content/dam/sandisk-main/en_us/assets/product/retail/cruzer_fit_angle_face_up.png
SSLstrip would like a word with you.
Ok, I wondered the same thing as Ostracus, even owning the LAN how can someone get my information if it is encrypted with ssl?
So, reading your reply of course I Googled SSLStrip.
I read a few of the pages I found but the explanations I am finding seem to be leaving a bit off. The graphic on this one seems to sum up what the text of this and other pages say pretty well and includes the reasons for my confusion. https://bit.ly/2UaIJom
I am left with two questions.
1) The MITM strips the ssl from the server’s responses resulting in plain text. How? Looks like magic black box explanations. Actually, I think I know how but nobody seems to say it.
2) The browser is requesting an https and receiving http. WTF?!?! It just displays it like everything is ok?!?! Why doesn’t it refuse to render the result and immediately throw up some sort of scary warning message?
Ok. I really don’t have any answer for #2. I’d love to hear one.
For #1 I am guessing that the MITM is impersonating the CA and substituting their own certificates. AMIRIGHT? If so then why not also re-encrypt the server’s output with the MITM’s certificate which the user’s browser should now believe IS the server’s own certificate thus negating my question #2?
This is why I hate dumbed down explanations of things!
Anyway.. If I am right. If this relies on the MITM being able to swap out the certificates then do we really need to send ALL our traffic through a VPN?
How about this? How about a browser plugin that talks back to my own server at home using a stored certificate that only ever gets updated when I am at home connected to my own LAN? Certificates requests or validations would be routed back to home through this plugin/server daemon combo. MITM would never have a chance to inject their own certificate. MITM can suck it!
Yah, I know. Either there is some complexity to how SSL works that means this isn’t good enough. Somebody needs to teach these protocol guys the value of KISS! Or, it will work but instead of a user-owned server it’s going to get implemented as a cloud app. I’m going to try to pretend as long as I can that the world and people in it don’t suck so badly and wouldn’t turn it into yet another way to donate one’s soul to the cloud though for as long as I can hold on to the delusion.
I recently discovered the mango: https://www.amazon.com/GL-iNet-GL-MT300N-V2-Repeater-Performance-Compatible/dp/B073TSK26W $10 cheaper, a second ethernet port, and bare openwrt firmware available right from the manufacturer!
I’m planning to get one of those low-profile sandisk flash drives for it
I used those awesomly tiny sandisk flash drives for the primary os disk on my DIY nas for years. However the recent usb3 versions of those sandisk drives get so hot that they literally fry themselves.
I’ve had a few of the USB 2.0 ones fry themselves as well. Switched to an SSD for my NAS boot drive.
22Wh battery pack and 0.7W solar panel … it will take a while to charge. Otherwise nice build of portable secure gateway.
Solar is utterly useless on this project. The panel itself doesn’t even provide enough output to power the router itself much less charge up the batteries. This panel would probably take a month to charge the batteries if there were no other load on them.
So?
As someone who would probably use such a device about once per month I’m not sure I see the problem. I think he still has the usb charging port on it if he needs it quicker too doesn’t he?
Anyone have experience to offer a tip to change this use case so that the wired connection is not required.
For example, sitting in hotspot-place this tp-link openwrt device acts as a client to the hotspot-place, establishes a vpn to vpn-provider, and broadcasts my-ssid for my client devices to tunnel vpn traffic through hotspot-place to vpn-provider and then on to the internet? Client devices connect to my-ssid and the vpn is bridged for them already by the tp-link
I’ve used a USB wifi adapter plugged in to a wifi router running OpenWRT. You can use one of the wifis as a client connection to the internet, and the others as usual for an access point. You could of course also do without the extra wifi adapter if you have a dual-band router and use one radio for the client. As far as VPN, I just set that up on my own clients, but I imagine you can do that in the router too. When choosing a wifi adapter, you need to make sure it uses a chipset that is supported by OpenWRT.
thank you、will research this path. great suggestion.
one other area that i will need to research is halving the bandwidth and using some kind of time sharing of the radio to antenna path. the posted product suppprts it on native firmware in both repeater and wisp client modes.
Have a look at the ‘travelmate’ package for openwrt. Might not be what you want exactly. I find it invaluable when travelling.
It will cut into your battery life of course.
Great idea!
Can You show test power 24h
and meybe one year test?
What is this for, when phones, laptops etc. already have VPN clients?
“Let’s not pretend we aren’t all guilty of it: at some point we’ve all connected to a public WiFi network to check our email or log into some site or service.” — Actually, no, we aren’t. Since I don’t live in the backwaters, 3rd world country they call the United States, I can have a mobile broadband with no dacaps on it and therefore don’t have any need, whatsoever, to connect to random WiFi-networks.
I live in the US and have a mobile data connection with no caps and no throttling. I’ll skip that word broadband since it has not well-defined meaning but I will say that downloads are comparable on my cellular connection to what they are on my home cable modem and Netflix works great.
Of course I only have that b/c I am grandfathered in. If the rest of the nation wants such a thing they are going to stop voting for the Rs and Ds as both are filled to the brim with utterly corrupt telecom shills and form some new parties since all our current third party options are batshit insane anyway.
Do you establish the VPN over the typical ports?
Fall back to DNS/SMTP/random other if they too are blocked?
Fall back to 80/443 if they are also blocked?
If VPN still fails, do you sign up to the portal to get the free wifi?
When does it know you’ve done that and kick in the VPN?
On which port once more?
Anyone automated all of that yet? :)
Since my home router is always on I connect to it using OpenVPN (it’s build in) and connect to the outside world from there, didn’t cost me a penny.
Same, and can even connect to my paid VPN for outbound. I imagine all this VPNining will come in handy when citizens start being treated as dissidents.
Wrong: OpenWRT
Right: OpenWrt
That’s true, but it looks stupid lowercase so…
Ahem, any thoughts of running LibreMesh https://libremesh.org on it? Veeeery interested in starting open source based wifi mesh as the widely available base transport.
The more devices running LibreMesh or equivalent, the more mesh points become available until such time as the mesh becomes so widespread it can transport traffic between the end points without the corporate pay for access internet. Imagine that, anywhere you go you just need to join the mesh and if your destination is on the mesh you dont need any 3/4G at all. We should all put up something like this high up on our houses as mesh points with a decent omni antenna.