The TP-Link TL-WR841N isn’t a particularly impressive piece of hardware, but since it works decently well and sells for under $20 USD, it’s one of the most popular consumer routers on Amazon. Now, thanks to [TrendyTofu] of the Zero Day Initiative, we now have a concise step-by-step guide on how to hack your way into the newer versions of the hardware and take full control over this bargain WiFi device. This work was initially done to help test out reported vulnerabilities in the router’s firmware, but we’re sure the readers of Hackaday can come up with all sorts of potential uses for this information.
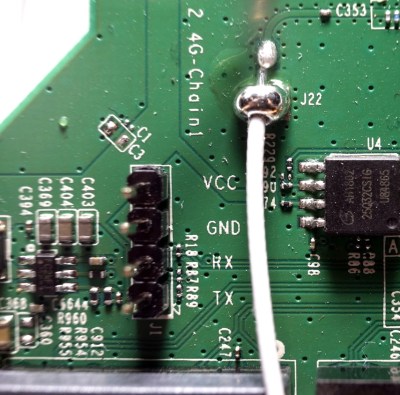
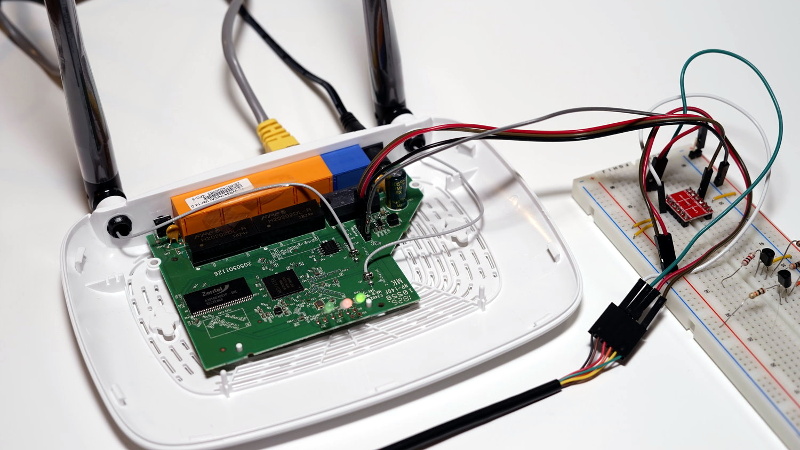
The story starts, as so many before it have, with a serial port. Finding the UART pads on the PCB and wiring up a level shifter was no problem, but [TrendyTofu] found it was only working one-way. Some troubleshooting and an oscilloscope later, the culprit was found to be a 1kΩ pull down resistor connected to the RX line that was keeping the voltage from peaking high enough to be recognized.
Once two-way communication was established, proper poking around inside the router’s Linux operating system could begin. It wasn’t a huge surprise to find the kernel was ancient (version 2.6.36, from 2010) and that the system utilities had been stripped to the absolute bare minimum to save space. Replacing the firmware entirely would of course be ideal, but unfortunately OpenWRT has dropped support for the newer hardware revisions of the TL-WR841N.
To teach this barebones build of Linux some new tricks, [TrendyTofu] used the mount command to find a partition on the system that actually had write-access, and used that to stash a pre-compiled build of BusyBox for MIPS. With a more complete set of tools, the real fun could begin: using GDB to debug TP-Link’s binaries and look for chinks in the armor. But feel free to insert your own brand of mayhem here.
You might think that in the era of the Raspberry Pi, abusing cheap routers to turn them into general purpose Linux boxes would be somewhat out of style. Frankly, you’d be right. But while the days of strapping Linksys WRT54Gs to remote controlled cars might be long be gone, there are still some routers out there interesting enough to make it worth dusting off this time-honored hardware hacker tradition.















I think this part counts as the hack . . .
“With a more complete set of tools, the real fun could begin: using GDB to debug TP-Link’s binaries and look for chinks in the armor”
agree!
Agree, but … well… there is the source code at TPLink´s site if one wants fo search for bugs.
From the article title, I thought it was to be something about understanding and repurposing the hardware …
theres some older articles around based on broadcom h/w that covers bare metal+gpio hacks, most of the info is transferable to newer devices if those are your kinda hacks. But alas in the esp glory days I dont reach for a wrt54g anymore but a espxx but i do still have my old blue 54g connected to my solar chargers UART to give me uart over IP and a relay trigger.
Are you sure you actually read the post? They are running GDB on the stock firmware to debug TP binaries in place. That’s not an inconsiderable accomplishment considering how limited the build of Linux on it is.
The repurposing is the easy part. The hard part is getting access and starting to build the base to port Open WRT or whatever to it so it can be repurposed.
“However, the number of tutorials on newer iterations has tapered because OpenWRT has dropped support for later revisions of this device.”
https://github.com/openwrt/openwrt/pull/1577
:)
They’re dropping support for all 4/32 devices, including the ultra-cheap ($17) router I’m using – which does at least have USB too.
https://openwrt.org/toh/zbt/wr8305rt
Yes, that’s 4 antennas – two of which are just connected to ground :-)
They are not dropping support yet, but require you to self build however so you can chose the wanted features
Is there a quota to the number of daily posts to be made?
One hack per day, the rest is just icing on the cake.
Our job is to work out which one is the true hack :)
As hackers, we don’t want to be obvious.
B^)
i think the issue they had with 3.3v not triggering is because that board has 5v safe uart, at least all the ones i’ve flashed in the past have been(mediatek/broadcom etc) , only ones i’ve seen from them that are not 5v uart are the wall wart models, some are 1.8v uart . Sadly it seems we are moving away from cheap AP’s that run openwrt as they wont fit the new features/firmware into ram/rom . Other factors have popped up like incomplete support from OEM and closed blobs, this means features that were easy to do (AP+repeater) can no longer be supported or are buggy as a proverbial Win10 update.
“Sadly”??? So millions of people should pay too much money for their routers because you want to play? Personally I find that less waste and lower costs are a good thing. Don’t you have any other toys to play with?
You get what you pay for. Usually cheap in these kinds of products means, but not limited to:
* underpowered (don’t expect nat to work well with more then a few users for example)
* poor hardware (cheap housing, badly design end electronics, poor range etc)
* shity software (yes it runs Linux, but usually some ancient insecure/unpatched version, that is to be said for all components, badly written in house software, shitty bug ridden blobs for drivers mostly)
* 4/32 seems to be the point for vendors where they manage to stuff software into while making it appear to work, by they make a lot of compromises/cuting corners to get there. I guest that this point is related to 1 and 3.
* no real updates. Don’t expect bugs or security issues to get resolved often
For slightly more expensive ones at least, if it has more flash/ram, we can solve the software problem with the likes of openwrt.
So please don’t say its just about toys, it really is not. But if you enjoy resetting your device every few days and don’t mind being frustrated by the above, by all means ;)
I have a Linksys EA2700 which I bought at a yard sale for 75 cents. Flashed whatever was then the latest DDWRT build for it. Configured it to login to my WiFi AP then connect that to its LAN ports and be a second WiFi AP.
It works, it’s solid. Hooray.
There are plenty of various brands and models of WiFi routers not supported by DDWRT for the sole reason of having about half the RAM and/or flash ROM required for a full DDWRT.
So why doesn’t anyone do stripped down, single purpose builds? A version that only does wired to wireless bridge, without WiFi repeater or AP, would be very popular. Just like stringing a virtual Ethernet cable to a router or DSL modem.
Could also lose the GUI and have configuration only via Telnet. What’s difficult about that? I’ve configured many network printers, print servers and various other devices by Telnet from a command prompt or a terminal program. The GUI is pretty and lets you use a mouse to point and click. Pttthhht. I’m from the era of having to use debug, edlin, and copy con to setup MFM hard drives and write autoexec.bat and config.sys files. One wrong keystroke and you get to start over from the beginning.
True, I also like to use the CLI instead of the mostly over-crowded GUI.
However, there is one problem: as lots of people don’t use telnet anymore, Microsoft removed the telnet command from Windows (if you are not modifying anything).
If somebody would like to use telnet, one would have to install something to do telnet instead of just going to http://192.168.0.1 to configure the home router.
As most of the people know how to navigate a web page, configuring by web page is just easier for most.
is it not the case though that commercial products are now mandated by the FCC to be less easy to hack?
https://www.socallinuxexpo.org/sites/default/files/presentations/Yes%2C%20the%20FCC%20might%20ban%20your%20operating.pdf
Maybe it is for safety ( for different definitions of safety ) , but this condition with a resistor in the TX/Rx paths has been common in many tplink ( and others, like Thomson, for example ) . Some just need a resistor to be added, instead, to complete the uart circuit.
Openwrt could still fit in the new devices, it just was their preference/decision to not support them based on some kind of software//interfaces/systemd/whatever they chose to use. Older versions of openwrt can still be configured to used in these abandoned devices, and there are other distributions that still support these devices. Closed blobs have existed since the times of the wrt54 and will be with us for a good time yet.
Cutting out the GUI and having configuration only by Telnet or a terminal program should shave a good chunk off. So would doing single purpose builds. A WiFi repeater doesn’t need code for an Access Point or a Bridge. Likewise a wireless to wired bridge doesn’t need wireless repeater or AP code.
Of course it’s neat to be able to combine a WiFi to wired bridge and a WiFi AP in the same device, but then there’s all the unused functionality bundled in.
The days of the 4MB flash / 32 MB RAM devices are over.
https://openwrt.org/supported_devices/432_warning
Alternative devices with 16MB/128MB for $20 do exist.
Can you give a couple examples? I am in the market for one and I love cheap Linux devices.
https://www.amazon.com/GL-iNET-GL-MT300N-V2-Repeater-300Mbps-Performance/dp/B073TSK26W 128MB Ram and 16MB Flash.
Has anyone created a spectrum/signal analyzer and/or signal generator app for these routers for use more for tuning antennas or parts and/or pushing the chipsets bandwidth or frequency range?
Was wondering if a 2.4/5.8 system could be hacked to be pushed beyond the ISM frequency range and for other uses.
Maybe the OpenWRT or related apps can do that already and I didn’t notice.
Bought a new TV and hacked it by plugging this black wire hanging off the back into a strange plate on the wall. Unlocked all kinds of capabilities like watching videos… WITH SOUND! I’m totally a H@CK3R!
IMac was the original hacked computer. Just plug it in and it’s ready to go.
I think it’s interesting they [and *many* others] are still using such an old kernel. The 2.x series was what I started on back in the 486SX-25 days, with 4M RAM… even ran X-windows. Wonder if there’d be any benefit to using it on newer [desktop/phone/etc.] systems… seems like if it’s still being developed 20yr later, it’d be darn-near rock-solid and extremely well-documented, among other things.
[I don’t recall /proc/ being a thing back then, hmmm. Prb didn’t have the RAM for it?]
But 20 years later, it’s not the kernel that is unstable, it is the newer platforms it would run on!
B^)
I doubt they bothered to fix CVE-2019-11477 in that kernel version. The oldest LTS kernel still listed on kernel.org is 3.16.
/proc very much was a thing back the the 2.x kernel days I’ve always used/examined /proc/cpuinfo and /proc /kernel from at least the late 90s.
https://en.m.wikipedia.org/wiki/Procfs#Linux
Tweeks
Some of us unfortunately were not endowed with this knowledge since birth. One of the great things about HaD is that there are people willing to impart knowledge, both in the project creators and the writing staff presenting them. How do beginners become experts unless they learn?
If this post was below you, perhaps you should have skipped it. Undoubtedly you have more important things to do.
Expertly said Dave :)
I couldn’t do it so yes, yes it is hacking.
And certainly far more hacking than the article about gorillas.
How about soldering individual wires to the BGA pads of the chip and exposing unconnected GPIO pins or an undocumented interface to the world?
If I wanted this level of “hack” I would have bought an Onion Omega 2 and complained that the Wi-Fi signals were weak because I forgot to attach an antenna.