There are some incredibly cheap WiFi smart bulbs on the market these days, but as is often the case, you tend to get what you pay for. When [Viktor] took delivery of his latest bargain basement bulb, the thing didn’t even work. So much for Quality Assurance. On the plus side, it was a great excuse to pop it open and replace the firmware.
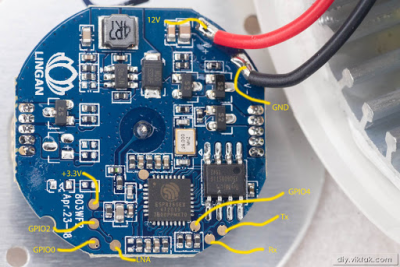 For anyone wondering, [Viktor] never actually figured out why the bulb didn’t work. Its ESP8266-based control board was getting power, and data was getting spit out of the serial port when he connected it to the computer (although he never got the communications settings right to actually see what it was saying). But he also didn’t care much; once he confirmed that the hardware was good, he just uploaded the custom firmware he’d previously developed for another ESP8266 bulb.
For anyone wondering, [Viktor] never actually figured out why the bulb didn’t work. Its ESP8266-based control board was getting power, and data was getting spit out of the serial port when he connected it to the computer (although he never got the communications settings right to actually see what it was saying). But he also didn’t care much; once he confirmed that the hardware was good, he just uploaded the custom firmware he’d previously developed for another ESP8266 bulb.
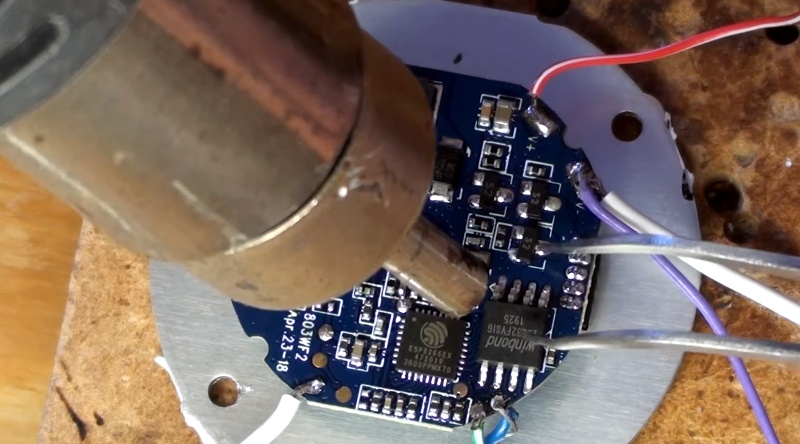
Of course, it wasn’t quite that easy. The chances that both bulbs would have used the same GPIO pins to control the red, green, blue, and white LEDs were pretty slim. But after some testing and modifications to the code, he was able to fire them up. The other issue was a bit trickier, as it turned out the bulb’s flash chip was too small to hold his firmware’s web configuration pages. So he had to break out the hot air gun and replace the SPI flash chip with something a bit roomier. We suppose he could have just made smaller web pages… but where’s the fun in that?
Even with the chip swap, this looks a lot easier than building your own smart bulbs from scratch. With so many cheap ESP8266 bulbs on the market, it seems there’s never been a better time to code your own home lighting solution.















Beyond color preference and a bit of lifestyle due to hours and time on, perhaps illumination levels used, what more sinister stuff can spyware tell you, esp given the small memory? Or is this just china-hating rhetoric for its own sake? (Maybe we should behave nicer to those without whom we’d be barefoot.😏)
Wifi password and ip address. With that it’s easy enough to get into a person’s network and then cause all sorts of trouble. Yes they may have to be physically close to you, but with the amount of zombies out there that may more likely than one thinks.
Once a device is on the network, it can start looking for other devices and create opportunities for external parties to gain access to things like cameras, smart locks, and even sensitive information on computers connected to the same network. The bulb may “look” innocent, but remote control and some sketchy custom api’s can give attackers a backdoor into your home.
>We suppose he could have just made smaller web pages… but where’s the fun in that?
Just like in Hackaday..
Or simply just flash Tasmota. No need for code anything.
Glad someone is keeping up.. Tasmota has ready built templates for a massive number of esp8266 based bulbs.
Or just flash https://github.com/arendst/Tasmota. No need to code anything.
Haha. This is really awesome. He was able to get the pin-outs, create a custom firmware, flashed it, then replaced the chip.. Wow.. Nice one!
I wonder if Viktor never heard of Tasmota/Esphome/espeasy etc ? He could have saved tons of trouble. But then again in true hacker spirit, what is the fun in walking a well travelled path :-)
He already _had_ his own firmware. Why complicate things by bringing in another system? :)
I also got an SP111(?) that was DOA, from pack of four. I just started flashing it with Tasmota and it stopped responding. After taking it apart, I saw that the issue was the vertical board had been cut too short: they use a 3D design with a few boards stacked and joined at right angles. The contacts were at the edge of the board and they were mostly lost during depanelization – i.e. the board was cut too short and the cut went into the edge contacts.
On the plus side, board shorts are back in this year.
I reckon that the manufacturer just copy their firmware directly to the flash memory (not from esp itself), but this one is skipped haha.
Haha. This is really awesome. Reball the IC and create a custom firmware and flash it.