Computer memory is a problem that has been solved for many years. But early on, it was more than just a small problem. We’ve many of the different kinds at Hackaday over the years, and we’ll link to some of them later on. But one of the original types of memory was called Delay Line memory, which worked by waiting for a signal to propagate slow enough through a device that it was essentially stored in the device. This was highly inefficient, but still a neat concept- one that [Tom7] has taken to entirely new levels of amazing and impractical as seen in the video below the break.
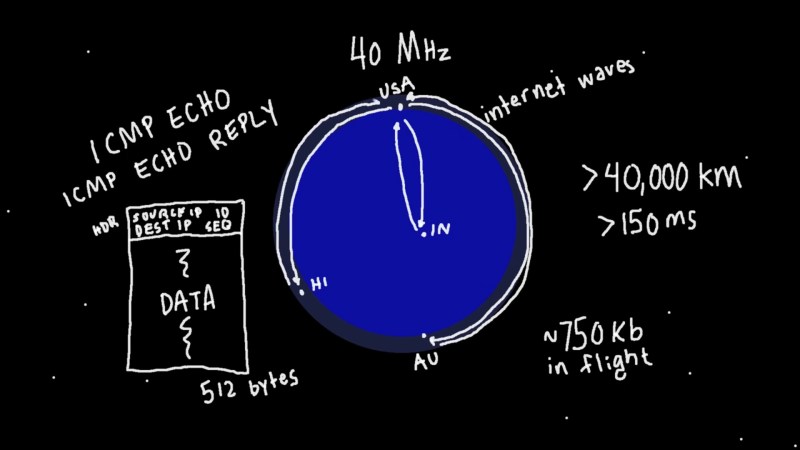
Starting with a demonstration of orbiting chainsaws, he then moves on to explaining how radio propagation waves could be used to temporarily store data while it’s in transit. He missed the opportunity to call it cloud storage, but we’ll forgive him. Extrapolating that further, he decided to use the Entire Internet to store data without its permission, utilizing large ICMP packets and even making it available as block storage in Linux.
Not content to use the entire Internet to store a few kb of data, he moved on to several thousand virtualized NES game systems which are all playing “an inventory management survival horror game” commonly known as Tetris. [Tom7] deconstructs Tetris, analyzing its Random Number Generator, gaming the system to store data in virtual NES consoles by the thousands. What data did he store? The source code to Tetris for the NES. And what did he do with it? Well, he mounted it and ran the program, of course!
The last Harder Drive we’ll leave for those who want to watch the video, because it’s a bit on the “ewww gross!” side of things but is also a bit less successful due to some magic smoke being released.
If none of these things we’ve mentioned were enough, then watch the video for an excellent breakdown of the cost, efficiency, and even the harm to society. For fun, he also tosses blockchain into the mix to see how it fares against the Harder Drives. There’s also at least one easter egg in the video, and the whimsical discussion of engineering is both entertaining and inspiring. How would you implement a Harder Drive?
[Tom7] also gives you the opportunity to follow along with the fun and mayhem by making much of the code available for your perusal. For more fun reading, check out this walk down computer memory lane that we covered last year, as well as a look into Acoustic Delay Line memory.















Why am I only now learning about SIGBOVIK? I know what I’ll be binging on this weekend.
this video was the perfect mix of insanity and brilliance. i clicked on it in my youtube feed expecting nothing, and was quickly proven wrong.
i wonder what he would think of my idea to use cats as an internet backbone. give a cat an esp32 router and a motion charger (think the automatic winders on a wristwatch). enough to keep the router online at least while the cat isnt in sleep mode. cats are quasi-social and territorial, this means the little fuzzy routers will disperse for even coverage yet still interact with eachother enough to maintain a functional mesh network. outdoor and feral cats constitute the back bone and housecats become the endpoint nodes. just be sure to give your router noms and scritches. i suppose you could used the ping storage on this network or include an sd card on the collar mounted router, i suppose you could call it clowder storage.
.
That was a lot of build up and thought to make a pun. Bravo.
didn’t really plan it going in but i couldn’t figure out how to end my post.
Your CAT can also act as a firewall (fiery beast?) on top of RFC 1149 and RFC2549.
It could also give a new meaning to “deep packet inspection”.
before i upgraded and cat proofed my router. the cats would sleep on it until it overheated and shut down. effectively a very indiscriminate firewall.
There was a classic BOFH post about convincing management to use the network as storage.
I remember that one! Floating the idea of buying miles of network cable for “in-network storage”, staging a mock argument of pros and cons to convince the boss it was for real, then watching the boss present the idea as his own to *his* boss and watching the fireworks.
Storing data in internet ping packets reminds me of the clacks semaphore system in Tarry Pratchett’s Discworld novels. The operators repeatedly inserted the names of deceased clacks operators into the message queue as a way to ‘keep them alive’.
RIP GNU Sir Terry Pratchett
If you use IPoAC you can store about 8 Terabytes in the same transmission unit as ping nowadays.
“Computer memory is a problem that has been solved for many years. But early on, it was more than just a small problem.”
Why, I can remember when three megabytes of hot RAM was worth killing for!
I wonder what Julius Deane is up to nowadays.
They kill for 3mb, but 640kb is all you really need.
Re: Using bitcoin’s blockchain to store data has one good use case – storing memorials to people who are then later rumore to be Satoshi, as Dan Kaminsky (https://cirosantilli.com/cool-data-embedded-in-the-bitcoin-blockchain/len-sassaman-tribute#video-black-ops-of-tcp-ip-by-dan-kaminsky-2011)
Wayyy more important than that: piss off the Chinese Government: https://cirosantilli.com/cool-data-embedded-in-the-bitcoin-blockchain#image-tank-man
Harmful to society are graphs without fully annotated axes.
Should look up the Cambridge Ring form of LAN networking from before the internet as we know it became a thing.
It was basically a hardware ring buffer over a massive scale, and too add your data you just changed an already existing (but blank) packet to contain it as it already had all the packets it needed, they were just blank and passed around in a continuous stream.
Packets only really existed “on the wire”, only being stored for the brief moment that they were being modified or had to be buffered/monitored.
That explains why we’ve been getting a bunch of trash ICMP packets recently…