Artificial satellites have transformed the world in many ways, not only in terms of relaying communication and for observing the planet in ways previously inconceivable, but also to enable incredibly accurate navigation. A so-called global navigation satellite system (GNSS), or satnav for short, uses the data provided by satellites to pin-point a position on the surface to within a few centimeters.
The US Global Positioning System (GPS) was the first GNSS, with satellites launched in 1978, albeit only available to civilians in a degraded accuracy mode. When full accuracy GPS was released to the public under the 1990s Clinton administration, it caused a surge in the uptake of satnav by the public, from fishing boats and merchant ships, to today’s navigation using nothing but a smartphone with its built-in GPS receiver.
Even so, there is a dark side to GNSS that expands beyond its military usage of guiding cruise missiles and kin to their target. This comes in the form of jamming and spoofing GNSS signals, which can hide illicit activities from monitoring systems and disrupt or disable an enemy’s systems during a war. Along with other forms of electronic warfare (EW), disrupting GNSS signals form a potent weapon that can render the most modern avionics and drone technology useless.
With this in mind, how significant is the threat from GNSS spoofing in particular, and what are the ways that this can be detected or counteracted?
Ephemeral Positioning
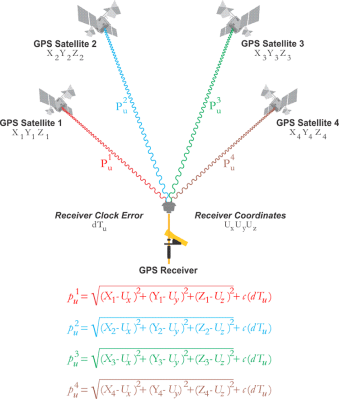
The basic concept of a GNSS is fairly straight-forward: ground-based receivers listen for the signals from the satellites that are part of the specific GNSS constellation. Each GNSS satellite encodes a collection of information into this signal, which includes the position (ephemeris) of the satellite at a given time, as well as the local time on the satellite when the signal was sent.
By taking the signals from at least four of these satellites and applying the satellite navigation solution, the absolute position of the receiver can thus be determined. This uses the principle of trilateration (distance to a known point) rather than triangulation (using angles). As can be surmised, a potential issue here involves clock drift on the side of the receiver and the satellites. Perhaps less expected is that the travel speed of the signal is also heavily affected by the atmosphere, specifically the ionosphere.
This part of the atmosphere changes in thickness and composition over the course of a day, and is heavily affected by exposure to the Sun’s radiation. As a result, part of the GNSS satellite’s message contains the required atmospheric correction parameters. Because of clock-drift and the constant changes to the Earth’s atmospheric composition, each GNSS constellation has its own augmentation system. These generally consist out of a combination of ground- and satellite-based systems that provide additional information that a receiver can use to adjust the GNSS information it has received.
For use with airplane navigation, for example, it is very common to have a ground-based augmentation system (GBAS) installed using fixed receivers. These GNSS receivers then broadcast correction parameters via the airport’s VHF communication system to the airplane, helping them navigate when they approach or depart the airport.
In addition to the GNSS satellites themselves, each GNSS constellation also has its own ground-based master controller station, from which updated information on atmospheric conditions is regularly uploaded to the satellites, along with time adjustments to compensate for the satellite’s onboard clock drift. This demonstrates that a GNSS constellation is a highly dynamic system which requires constant updates in order to function properly.
Where things get interesting, however, is when attempts are made to circumvent this system, either by jamming or actively spoofing the GNSS signals.
Jam Warfare
The concept of jamming radio frequency communications is quite straight-forward: simply broadcast on the frequencies you wish to jam with more power than the original transmitter is capable of. Since the GNSS signal is relatively faint, this makes it easy for a ground-based system to jam this signal. Of course, since loss of a GNSS satellite fix is a known issue, backup strategies for this scenario are common, and it’s also very noticeable due to the loss of communication from a satellite.
Spoofing is a lot more subtle than jamming, as well as more versatile. Instead of merely blasting the airwaves with raw power, GNSS spoofing still involves overpowering the original signal, but instead of a denial of service (DoS) attack, spoofing is closer to a man-in-the-middle (MitM) attack, where fake satellite signals are presented to the receiver as being the genuine signals, with of course spoofed parameters that will cause the receiver to calculate a position that’s far away from where it actually is.
In a 2019 report by C4ADS (Center for Advanced Defense Studies) titled Above Us Only Stars – Exposing GPS spoofing in Russia and Syria, a number of observations are reported on where Russia has used GNSS spoofing, for a variety of reasons. An interesting and common use appears to be the spoofing of GNSS signals so that receivers think that they are located at a nearby airport. Presumably this would trigger the geofencing limitations in drones and similar, which would then refuse to take off. This could be useful during VIP visits as an anti-drone strategy, for example.
Less harmless is the military use, where during recent Russian and NATO exercises Norway and Finland reported severe GPS outages. This affected the public by limiting the navigation capacity of commercial airliners, and also disrupted the use of cellphone networks. Supposedly, in 2011 Iran used GPS spoofing to trick a Lockheed Martin RQ-170 drone to land on one of its airfields, where it was subsequently captured. Similarly, there have been multiple occasions now where marine traffic has been disrupted due to faulty GPS data being fed to the automatic identification system (AIS).
As the 2019 C4ADS report notes, this has been reported by ships in the Black Sea on multiple occasions, and also in 2019 it was reported that an American container ship – the MV Manukai – noticed very strange behavior while at the port in Shanghai, China. According to its AIS screen, one ship was shown as moving in the same channel as the Manukai, before vanishing from the screen, then appearing at the dock, before appearing in the channel and so on. When the mystified captain picked up the binoculars and scanned for this ship, it was clearly stationary at the dock that entire time.
GNSS Hunting
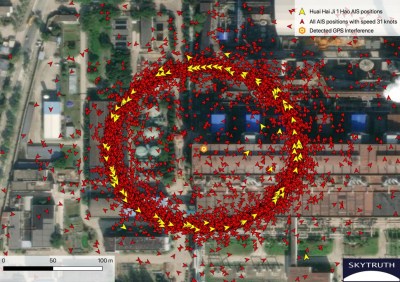
What’s mystifying about the GNSS spoofing as detected in Shanghai is that instead of it merely moving the calculated position to a nearby fixed point, what we see when we collate the wrong AIS data onto a map is that they form near-perfect circles. This is noted by both the MIT Technology Review article, as well as a later article by SkyTruth.
What is interesting is that when using the anonymized route information from Strava in Shanghai, this same ‘circle spoofing’ could be observed, independent from the AIS information. Somehow it would seem that the spoofed data is constantly updated, to make it appear that the affected receiver is in motion, and travelling in this large circle.
Exactly how this is done, or why, is still unknown, with no major updates since the initial reporting in 2019. Whether the intent is to hide illicit activity, or whether it’s due to some kind of cyberhacks or a glitch, nobody is entirely sure. Even independent from Iran, China and Russia, GPS-related location glitches keep happening.
Yet as a team from the University of Texas at Austin demonstrated in 2013 already using $2,000 worth of equipment and an $80 million yacht, spoofing GPS signals is relatively easy and straightforward. It doesn’t take a lot of imagination to picture what is possible today, since since that demonstration nine years ago using a university-budget, especially when upgraded to a nation-sized budget.
According to current reports, Russia is actively spoofing GPS data during the war in Ukraine, which would affect mostly private and commercial users. Whether the US military has additional backups in the case of spoofing and jamming attempts is naturally unknown, due to national security reasons. Even so, with the importance of GNSS today with navigation and so much more, it would seem pertinent to wonder whether spoofing can be detected or circumvented.
Knowing Is Half The Battle
In an analysis by Guy Buesnel, he notes that there are quite a few risks in the GNSS chain, not the least of which is faulty equipment, and sources of interference. Perhaps the most important lesson of the past years has been that solely relying on GNSS is risky, and that adding additional ways to determine one’s position is essential, as well as the ability to detect the act of spoofing.
This aspect of detecting and possibly circumventing spoofing is currently the topic of active research, as noted by e.g. Mark L. Psiaki, et al. in a recent paper. While there’s unlikely to be a silver bullet that will fix all ills and return GNSS to the infallible system that was promised to us by glossy flyers years ago, what we are likely to see the coming time are better, more robust GNSS receivers. We’re already seeing that GNSS receivers built into smartphones can use multiple GNSS constellations, with the ability to use local WiFi networks and so on as augmentation.
Using fairly low-tech improvements it would be easy to detect many spoofing attacks, such as when one’s calculated location suddenly and dramatically changes, or when one’s calculated course does not match with the data provided by the augmentation system, cell towers, or other sources of location information.
Even if GNSS isn’t the effortless panacea that many had assumed it to be, it is still a major navigational marvel, and a cornerstone of modern civilization that will continue to see improvements as it has since the first GPS satellite was launched. It just takes staying one step ahead of the meddling hackers.

















I’ve seen the GPS put me a few hundred meters from where I actually am a handful of times, but usually those resolved quickly so might have been signal obstruction or reflection in the local environment. One that is more weird was doing a journey I had done frequently but on a highway prone to blockages by accidents, so I had the GPS “hot” so I could detour easily if required. Not really paying attention to it, volume on min. However, went the normal straight route, but when I got there, it seemed to have thought I went the wrong way around the planet at a speed of several thousand MPH.
Those are quirky, but one persistently occuring problem, is a GPS “briar patch” between two small towns here, “on the backroads”. Mostly you don’t go that way unless you want to go from bottom of one to top of other, rather than middle to middle that the main arterials take you. I “sorta know” the area and in daylight it’s easy, at night there’s not enough unique large features close to the road to help landmark it, and there’s a bunch of turns. I’ve been through there a few times with the “assistance” of various GPS devices and I always end up way off course, usually resolving when I meet the 9 o’clock or 12 o’clock arterials, when I was trying to come in on the approx 10:30 backroad. One time it got me on the other side of the town I don’t know how. This is with the route set in advance…. but then you’d be driving and it would be like “Continue for 3 miles…” then about a mile down the road “turn around when possible” whaaat? One time I did this trip at night with two passengers, I had the Garmin on the dash, and one passenger had google maps on a Samsung, another had Apple Maps on an iPhone (and this is while it was still apple mapping) and some points we had 3 different opinions of where we were. This area is not very hilly or anything, the only thing I can think of is that there is a pipeline station where it comes up above ground for valves and monitoring or something, which is near that area, and might be “sensitive infrastructure” but is closer to one of the major routes, and things don’t go funky going that way.
One thought is that back in early GPS days, Canadian authorities had the co-ords they wanted protected on the old datum, and “converted” it by subtracting instead of adding the difference to the GPS datum, so the dead spot is off where it should be from the pipeline facility.
GPS jamming is used on occasion within the US. Or at least the NOTAMs for GPS may not be reliable near places like White Sands Missile Range would suggest that. How else are you going to test how your system works in the presence of jamming?
Military systems usually have anti-jam features like directional antennas so they can ignore stuff like ground based jammers.
You can bias the antennas to only receive signals from above. Helps more in the air, and if the signals aren’t from an airborne source.
They should, if not already, use encrypted location data.
GPS doesn’t provide “location data”, it provides a signal that can be used to determine your location. There is an encrypted channel for military purposes, but those receivers have been in limited availability at times. (So much so that military has used civilian units extensively).
Why don’t the satellites just sign each transmission with a public key? Whilst some kind of replay attack might be possible, this would make spoofing immensely harder.
The packets are actually really size-constrained. There is not room for a large key. Also the replay issue. See here: https://berthub.eu/articles/posts/galileos-authentication-algorithm-part-1/
GBAS is rather rare. SBAS is common.
Interesting!
Surely crucial military equipment doesn’t just rely on GPS ?
I mean some basic sanity check in form of an IMU and a known starting position shouldn’t be that hard?!
The Russians have been duct-taping commercial GPS to jet dashboards.
Probably because their Glonass kit is unreliable.
So to some extent, jamming GPS in Ukraine might be counter-productive….
That’s either some good duct tape, or the Russian jets aren’t all they’re made out to be at air shows.
How do you think they’re held together?
ublox doesn’t allow supersonic tracking.
In my experience glonass is very reliable. What is not reliable are the military electronics that interpret the signal and overlay your position on a civilian road map.
Mapping has been one of the great intractable problems of the 21st century. When considering the entire world and all of it’s roads there are literally trillions of data points need to be available to be drawn.
A road is simply a line drawn along thousands of points. If you want reasonable resolution that might be hundreds of points per km.
*laughs in drift*
Military GPS is on multiple channels on different frequencies, so it’s a lot more work to spoof accurately.
The last data I know for sure was from talking to a Raytheon anti-ballistic-missile missile designer in the late 2000’s, and his expectation was that GPS would not be available, so they had GPS if it was possible but also had star ephemera where they matched real-time video with saved starmaps. (This was for high or out of atmosphere operation.) Plus IMU.
> hide illicit activities from monitoring systems
You misspelled “hide activities from illicit monitoring systems”.
It is an easy problem to solve, just shoot radio seeking missiles at the apparent location of the GPS satellites, any of the ones that were in range and thus hit were clearly fakes.
Except the fakes aren’t where they claim to be, so they’ll miss.
So if someone you are chasing, flashes you with a flashlight in morse, from atop an office building, “Haha, I’m at St Rudolphs Church now.” you would only know that he’s not at St Rudolphs Church?
You don’t aim for where the signal says it is – you aim for the origin of the strongest signal.
AGM-88 HARM
“This demonstrates that a GNSS constellation is a highly dynamic system which requires constant updates in order to function properly.”
So no GNSS after an apocalypse.
“Yet as a team from the University of Texas at Austin demonstrated in 2013 already using $2,000 worth of equipment and an $80 million yacht, spoofing GPS signals is relatively easy and straightforward.”
The secret ingredient to easy and straightforward. Anyone have a $80 million yacht I can borrow?
Previously, you could write up a whackass research proposal to send to Paul Allen and prior to his death in 2018, he may have lent you one of his fleet. Don’t know if his successor does it.
This feels like a problem just begging for a specialized anti radiation missile.
It’s a problem calling for a catastrophe. When a floating production, storage, offloading vessel (FPSO : giant offshore oil rig) offloads to a tanker it uses a gimongous flexible hose and GPS on the tanker to make sure the two don’t collide or pull the hose apart. As only the tanker is navigable, GPS errors could lead the tankers into a disaster.
BTW: it’s very easy to spoof AIS. AIS isn’t GPS. AIS transmits the decoded coordinate results of a GPS receiver on a marine radio channel or on a satellite link. You could feed an AIS transmitter any kind of fake data.
Same for ADS-B. Simple RF scheme. No encryption.
A good HackRF board should do the job:
https://github.com/B44D3R/SDR-GPS-SPOOF
I studied GPS at university, there was a girl that was in the same class who did a PhD on problems using GPS to land planes. Will try to find her research.