A self-destructing storage device that vaporizes its contents at the first sign of trouble would be an invaluable tool for many people, but good luck getting your hands on such a thing if you don’t work for a three-letter agency. Or at least, that’s what we would have said before [Walker] got on the case. He’s working on an open source self-destructing USB flash drive for journalists, security researchers, whistleblowers, or anyone else who really values their privacy.
When we previously covered this project in July, [Walker] had only planned to make the flash drive hide its contents unless you knew to wet your fingers before plugging it in. We admit it sounds a little weird, but as far as clandestine methods of activating something goes, it’s pretty clever. But based on the feedback he received, he decided to go all-in and make the USB drive literally trash itself should it be accessed by somebody who doesn’t know the secret.
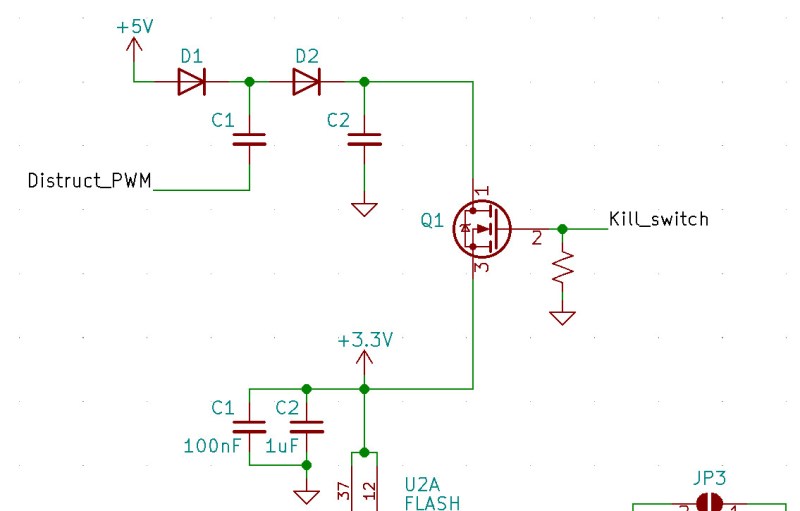
But how exactly do you pull that off? Sure we’d love to see a small thermite charge or vial of acid packed in there, but obviously that’s not very practical. It needs to be safe to carry around, and just as importantly, unlikely to get you into even more trouble with whoever is searching through your belongings. To that end, [Walker] thinks he’s come up with an elegant solution.
The datasheet for his flash memory chip says the maximum voltage it can handle before releasing the Magic Smoke is a meager 4.6 V. So he figures running a voltage doubler on the nominal 5 V coming from a USB port should disable the chip nicely with a minimum of external drama. Will it be enough to prevent the data from being recovered forensically? We don’t know, but we’re eager to find out.
In the write-up, [Walker] takes readers through the circuit designs he’s come up so far, and shows off the source code that will run on the ATtiny25 to determine when it’s time to toast the flash. He says by the next post he should have the entire flash drive built and documented, so stay tuned.
















an easy an reliable way to release the magic smoke is reversing polarity most CMOS and other ICs cant handle much reverse voltage.
So in a few weeks we will have a follow-up post on “recovering data from an overvolted flash drive” :)
Despite the hazards and obvious nature of the approach…
Thermite is reliable data destruction.
Really has me thinking how well one could design an enclosure to mitigate risks.
I figure you center a microsd card in a full size exHDD enclosure, you’ll have enough room for tamper detection, pyrotechnics, and enough refractory cement to keep things contained…
It could be done in a regular usb stick. It would require some very small bags of thermite (you don’t need much) and placing one below the flash chip in a cut out on the pcb. Ideally you would use a a flash chip with pins on the sides rather than a BGA chip. The bag would be easy to make. Setup the bag with a strip of magnesium along the length of the opening, both exposed to the air and touching the thermite. On top of the magnesium you place a bit of nichrome wire and seal the plastic bag down over this to close the bag with the nichrome wire ends poking out, with the magnesium and nichrome sandwiched in between. On the other side of the PCB opposite the flash chip and over the other side of the thermite bag, solder on a metal cap like the ones used to block EM interference on wifi dongles. This will direct most of the heat back towards the flash chip since the metal can will take longer to burn than the plastic covered chip will. Then you just need to build up some circuitry to get the nichrome wire hot and your off to the self destruction races. Probably a good idea to put this circuit under the can as well to make it hard to access.
Another though, set up your USB drive as a micro SD reader and hide the micro SD card inside the USB stick directly wired up to the USB/flash interface controller. The micro SD is embedded/buried in the plastic baggy of thermite, so when it goes off you know for certain the SD card is completely destroyed.
Clever setup there Jack!
Since there’s already a ATtiny25 in there, why doesn’t he launch a sequence of erases on the flash chip already ? So the key appears empty and doesn’t disclose it’s non functional (which is a very troublesome outcome in case of investigations). In fast, it can be made in two steps: 1. erase the first block and flash an empty “FAT32” header in there. 2. proceed to erasing the following sectors, so even if interrupted here, the flash drive will look like a legitimate USB (empty) drive.
This. Replace the contents with a bunch of legit looking Excel files and a picture of some kids.
Whose kids?
Or just a gig of XKCD comics.
Also, the computer where the key is plugged will likely have its USB port be killed too when this happens, they don’t like to have 10V on the data and/or VBUS lines. Not really safe if you want to hide something
The voltage doubler circuitry blocks current backflow into the usb 5V rail (notice the direction of the diodes) so vbus will never see the 10v across it.
If you’re unlucky, the 10V can pass through the flash chip being fried via some signal lines to the USB interface chip and with even more bad luck, on to the D+/D- signal lines.
Crowbar clamping on the differential usb lines along with the low power of the voltage doubler limits chances of permanent damage
But does it work?
When reading Ryan’s web page I see no mention of this thing actually tested yet.
There is also an mis-interpretation of the “absolute maximum ratings”. It means the device won’t be immediately destroyed with a power supply voltage of 4.6V. It does NOT mean that it will be damaged from 4.7V.
If I were to design this my first idea would be to generate some 50V in an inductor, store it in a capacitor for high peak current and discharge it in an important I/O pin, such as for example chip enable.
If you want to be thorough, then decap the IC after testing to examine what part of the IC gets damaged.
Yeah, our chips can handle 1v above absmax, they just draw a lot of current and have enough ion migration that they won’t last for days of that kind of operation.
Whereas if you dump 50V into a pin with an absmax of 4.7V, that’ll activate the ESD structure, and if you blow out the ESD you’ve managed to kill the chip (with the proviso that the flash circuitry is still holding the values you stored.) If you want to trash it up thoroughly you’d apply about 8V, well above absmax but not high enough to involve the ESD, and THEN pop up to 50V to blow the ESD too. (This may not be applicable for the process used for memory: I work with state machines on silicon rated to about 50V.)
“Sure we’d love to see a small thermite charge”
So, it would be a flash flash drive!
B^)
More like a flash bang drive.
One flash and it’s ash!
That voltage doubler will not be able to supply enough current to damage that flash-chip i’ll bet. You need a boost converter with some low-ESR caps on the output and i’ll think you need 400% of Max for the chip to ensure it dies.
Yah, definitely an “it’s complicated” Vmax is only usually the voltage that it’s guaranteed to for long term operation. On a cold day it might run long enough to dump the contents at double or triple that. May handle quite high transients when it’s not doing anything, or tolerate brief bursts of voltages that seem like overkill, only they don’t last long enough and the chip is not heat soaked from use. Then are you really really killing it, or just making it unusable in current package as you fuse protection diodes. Cutting it off from the outside world apparently, but leaving adversaries willing to spend a few thousand with the option of decapsulating the silicon and reading it with probes that connect inside the fried peripheral circuit components. Then half the time you think you’ve fried something it will still work at hugely reduced clock and kept cold.
So really, it’s about pushing it way past the TDP and specific heat capacity. Blips of voltage may not do that. IMO if you don’t popcorn or melt the package you can’t be sure you’ve done much. To do that, you may have to ramp voltage while it is loaded, actually doing something, switching juice to many parts of circuit.
Personally, for this type of device, I’d look into thermally wiping it. Get a nand flash cell warm enough and it blanks itself. Small coil of nichrome on it just waiting to cook it off given power. Then you know you have affected the important part of the device, not just the things that make it easy to read.
Given that many of the HaD community regularly run ESP chips beyond vmax, I agree. This doesn’t seem reliable, especially as it depends on our-of-spec behaviour which may vary between individual drives.
The normal way to do security (e.g. on an iPhone or encrypted HD) is to encrypt the drive, and store the keys somewhere they can be very quickly wiped.
> many of the HaD community regularly run ESP chips beyond vmax
wait, who? I’d like to read more! are you talking about like, one or two people running ESP8266 directly from 5V with variable results? If so, darn – I just was trying to find information on ESP32 over-3.6V powering and is sure it hard to find!
Not a bad idea. Doing the math 1″ of 40 gauge Nichrome wire has a resistance of 5.63 ohm in order to reach a temper of 1000 degrees you need 430 mA. Which comes out to roughly 2.5 volts. Maybe incorporate some type of coin cell or small battery and If you make a small coil near the IC it’s definitely will smoke. Completely simple. Of course you’re going to need some type of activation. Circuitry but that could be easily worked out depending on the circumstances predict you may find yourself in
I have a device to put 230V direct just to burn all components. Make smoke and a sound that looks like a mobile phone hit the floor
The way some “people” with petabytes of data to secure from their enemies is to use an encryption key stored on a few read only solid state drives with shaped explosives (The reason for multiple SSD’s is for speed via interleaving and redundancy) usually accessed inside a bomb proof safe. And then use that key to encrypt/decrypt everything, once the keys are gone the data is inaccessible (In theory the key could be recovered with brute forced with traditional techniques or known quantum algorithms, but to do that with current and predicted future technology on the encryption/decryption algorithms selected would take longer than the universe will exist).
Now if I was designing a secure SSD and wanted the solution to be cheap I’d do something different. I’d used OTP (One Time Pad).
I’d fill the entire SSD with 100% cryptographic quality random data (Sourcing that is a problem).
I’d keep one exact copy of this at a secure location, where decryption can take place.
Then inside the enemies “danger zone” every time data is written would require 4 steps:
1 read the existing (next) block of random data
2 XOR this with the data to be written
3 erase the existing block of random data
4 write the new block.
You are effective destroying the One Time Pad key material as you are using it.
Some erased block may survive due to wear leveling, which provides a method for distributing program and erase cycles uniformly throughout all of the memory blocks within the SSD. Unfortunately some may be flagged as bad block and then the CPU inside the SSD will transparently re-maped bad blocks and exchange them with the spare flash blocks. And some OTP key material for individual blocks may survive. Running the device 100% full to help slightly to minimise this, but the reality is that some blocks could potentially be decrypted. It is not a 100% secure solution, but depending on that data, in most use cases it will probably be good enough. Of course if a full copy of the OTP key material was taken at the border when entering the enemies “danger zone”, that would mitigate all security. A filesystem similar to the original Compact Disc File System (CDFS) – read-only and write-once CD-ROMs could be used. (ref: https://simson.net/clips/academic/1986.CDFS.pdf ) A WOFS (Write-once File System).
That’s an interesting take, but no. That’s not at all how it’s done.
I could say where and when, but I will not.
Anyone who cares that much about their data is not going to be using flash drives as primary storage
Your entire overblown scheme is easily defeated with plain old malware, hook into the decryption calls and you get all the data.
There are no local decryption calls, not until you return to the physically secure location which contains the decryption key.
“A self-destructing storage device that vaporizes its contents at the first sign of trouble would be an invaluable tool for many people, but good luck getting your hands on such a thing if you don’t work for a three-letter agency.”
or, y’know, buy it from Kingston. It’s great to have someone working on an open-source version, but IronKey has been for sale to the general public for 15+ years. Disingenuous for HaD to pretend there isn’t a COTS product, even if it is pricey. https://www.techrepublic.com/article/ironkey-flash-drive-self-destructs-on-too-many-failed-password-attempts/
You’re aware this is a 15 year old post you linked to, right? Plus the device it describes just erases itself, rather than literally destroying the flash?
What was the point of making this comment?
Do you trust Kingston more than say RIM to not have the viewpoint of, “We’ll help any governments/police at the expense of our customers if they just ask….”?
I’m with @sweethack above; if you can’t ensure destruction, a malfunctioning drive will just be a dead giveaway that there’s something hidden. My idea was to just have a way to switch to an empty/innocuous version of the drive, perhaps by blowing a fuse, so that getting at the true contents would require special knowledge and simple hardware repair. It also seems like the circuitry would be easier to hide from casual examination.
Better way to do something like this would be to use RAM instead of FLASH and then supply power from a battery. Self destruct would be as simple as cutting power to the RAM and waiting a couple of seconds. Second method would be to encrypt the drive and store master key in the EEPROM. Self destruct overwrites EEPROM with random data and key should be gone for good. Small EEPROM ICs do not have any kind of wear leveling so erasure would be more reliable.
That would be an interesting design, as you would use any of the above “detection methods” just to remove the battery from the memory.
Battery backed ram would most likely work, but I recall reading that at very low sub zero temps ram can preserve its contents. Realistically would work, pretty much no one would think of checking if it was ram or eeprom, just pointing out one potential way around that
If that doesn’t work then maybe you could do it with a 555.
No seriously, I think I remember there being a way to “mis”-wire a 555 that pretty reliably causes it to blow it’s top hard. Maybe a 555 could be mounted dead-bug upside down right over the flash chip to provide some percussive erasure.
Encrypt content (AES 256 or smth), store key in battery backed memory, kill power to memory when something fishy happens (whatever you consider fishy).
You might even be able to get some plausible deniability going by having a second smaller section of the flash reserved for the wrong password and just filling it with mundane files.
Hardest part is finding a freely programmable flash drive controller…
I was going to suggest this, best path would be to leave all the data in flask encrypted and program a controller to encrypt/decrypt on demand
I would go even further, I would not store the key (or seed for the key) in the driver, but make the user supply it every time he wants to access it
Imagine a USB thumb drive with an 8GB flash chip but that exposes itself on the USB as a 4GB thumb drive, and once you “create” a new text file on it with the correct name (the password) it would then mount a second volume where the other half of the flash is decrypted/encrypted on demand, once the drive is unplugged from USB the key is lost and the auth needs to be done again
It ticks every item, security, plausible deniability, easy of usage
Of course, access speed would not be the best, as we would need to program a microcontroller to interface it (perhaps using a small FPGA??), but it would be definitely secure
RAM + battery + usb -> simple destruct
If evidence of physical destruction is not an issue just use micro SD card, it’s easy to snap it in half with your fingers and destroy it. Or use USB stick with deniable encryption, two keys, one opens decoy volume, one opens secret one, VeraCrypt has this feature.
There’s a way to make hidden partitions on a USB stick by loading a different driver. Go back to the original driver and only 1 partition is visible. Make this one the same size as a smaller stick, and switch the plastic case to reflect that size.
If use use a different driver you can make partitions on the USB stick. Going back to the original driver, only the first partition is visible. Make the visible partition the same size as the next size down, and switch the plastic case to reflect that size.
3rd try commenting…..
Good morning Mr. Phelps. Your mission should you decide to accept it ……
Put a small LiPo battery in it so that even after the security method is triggered, yanking it out of the port can’t stop it.
The easiest way to secure it would be to go back to how early PCMCIA memory cards worked using SRAM and a coin cell. When the coin cell died the data went buh-bye. IIRC when plugged into a slot in a running laptop the SRAM was kept powered by the slot power so the battery could be changed without having to backup the data then copy it back to the card.
With a small LiPo all it would need to do to securely and instantly wipe is have the circuit disconnect the SRAM from both the port and battery power. That would have the benefit of making the thing reusable. The downside is it would have to be frequently used or plugged into a charger to keep the battery charged so the data won’t go poof.
A lot of people have run into this with PayPal’s previous model of card reader with the keypad, RFID, mag stripe reader, and OLED screen. It has a security key in RAM, a rechargeable battery, and a non-rechargeable, non-replaceable battery. The rechargeable is what normally keeps the security key alive along with all the other functionality. When the rechargeable power gets too low, it’s the non-rechargeable one that maintains the security key. For people who only used the device infrequently, like once a year for sales at a craft show, it would die and become a brick, or a very clunky 32 meg flash drive. Could be it also lost the updateable part of the software in it.
IIRC it was stated nowhere that one had to ensure it was kept charged or the $149 spent on it would be wasted. It should have been made with the non-rechargeable battery made to be replaceable and clearly stated in the instructions and on PayPal’s website to keep it charged, and to charge it before the periodic replacements of the non-rechargeable battery.
What was *super annoying* about it is that any change in its USB power state *turned it on*. Plug it in to charge and it’d turn on. If it was plugged in and off, unplugging it would also turn it on. It was SLOW, taking quite a while to boot up to the point where it could be turned off.
I assume that “feature” is what led to many early deaths of the device. Someone would charge it up with it turned off (so it’d charge faster) then when done they’d unplug it and put it away without turning it off again.
Turning a thing on when power is connected or disconnected is among the most annoying and dumb things any electronic device can do. I just want to be able to plug my phone in, or unplug it, without having to hit a button to shut the screen off. I don’t care that it’ll go off again in the time I set in display settings I want to have it only on when *I want it on*. But there’s nowhere in any Android setting to enable that, because someone at Google thinks because they want their phone constantly turning its screen on by itself that everyone else also wants that.
The trigger vircuit is not shown, I don’t understand hiw he is going to get the gate of then nfet to above the 10 volts to really apply the voltage…?
It looks like the USB Flash controller actually has an integrated 8051 with a few GPIO. This means that you could get the same functionality without the ATTINY, but more importantly, it looks like the 8051 can write to the RAM buffer, meaning instead of trying to over-volt the flash, which would likely leave data recoverable to determined seekers, you could continuously write some pseudorandom 1s and 0s to the flash for as long as it’s powered on after seeing an insecure state. You could even use the first byte as status, and save that you’ve seen an insecure state and keep doing this whenever it’s powered on, even if the “trick” is discovered. After a couple write cycles the data would be nigh impossible to recover by my understanding.
Would be better to have 2 sets of chips inside the flash drive, one which gets destroyed when the drive is connected by an undesired user, the other which then shows up post-destruction to show some non-secret files. An enemy might well think a dead flash drive is worth closer inspection, they’d be a lot less likely to get out the screwdrivers and soldering irons for what looked like a perfectly working flash drive. Nobody tries any advanced data recovery methods on a drive which looks like it is working, any well resourced opponent might on a drive which looks dead.
I’ve always wanted to find an off label use for this component.
https://www.vishay.com/en/igniters/
Estes ignitor, small tube full of picric acid
No flash, no controller, no problem
Put the flash drive in the microwave and cook it for 1 minute
As low power capacitor will explode when you overpower. We use for pyro as ignition. Small enough.
Given how the Trudeau regime has acted recently (horse trampling protesters, freezing bank accounts…), it looks like Canada, where the designer of this cunning device is to be found, may well be a country where these would be needed. It must be a depressing day when you realise the thing you’ve been developing to help journalists in oppressive countries abroad is suddenyl needed at home too.
The horse trampling where police charged into a crowd with horses, and one woman died; Or the one not made up by a Fox contributor, where police horses slowly moved between a row of riot police and a row of protesters, lightly injuring a woman? ‘Trudeau regime’? You might consider crossing the US/Canada border wearing a hijab to test which border guards will want to take a look at your thumbdrives…
I can’t help but think this is more likely to give the user a warm feeling of false security than any actual security – blowing the front end / ESD protection on a flash chip does not erase any data and we’ve seen enough projects right here on HaD where people have recovered data from dead chips, SD cards, EEPROMs etc. by various means.
I kinda feel like any determined attacker is not going to be stopped by this, and for less serious threats this is just overkill compared to a decent grown-up encrypted volume using trusted crypto.
I came across this post when looking for esp32 encryption options.
Most heat based destruction could be defeated with liquid nitrogen or even a can of air turned over. And the cold would have added benefit in glitching.