Despite some companies making strides with ARM, for the most part, the desktop and laptop space is still dominated by x86 machines. For all their advantages, they have a glaring flaw for anyone concerned with privacy or security in the form of a hardware backdoor that can access virtually any part of the computer even with the power off. AMD calls their system the Platform Security Processor (PSP) and Intel’s is known as the Intel Management Engine (IME).
To fully disable these co-processors a computer from before 2008 is required, but if you need more modern hardware than that which still respects your privacy and security concerns you’ll need to either buy an ARM device, or disable the IME like NovaCustom has managed to do with their NS51 series laptop.
NovaCustom specializes in building custom laptops with customizations for various components and specifications to fit their needs, including options for the CPU, GPU, RAM, storage, keyboard layout, and other considerations. They favor Coreboot as a bootloader which already goes a long way to eliminating proprietary closed-source software at a fundamental level, but not all Coreboot machines have the IME completely disabled. There are two ways to do this, the HECI method which is better than nothing but not fully trusted, and the HAP bit, which completely disables the IME. NovaCustom is using the HAP bit approach to disable the IME, meaning that although it’s not completely eliminated from the computer, it is turned off in a way that’s at least good enough for computers that the NSA uses.
There are a lot of new computer manufacturers building conscientious hardware nowadays, but (with the notable exception of System76) the IME and PSP seem to be largely ignored by most computing companies we’d otherwise expect to care about an option like this. It’s certainly still an area of concern considering how much power the IME and PSP are given over their host computers, and we have seen even mainline manufacturers sometimes offer systems with the IME disabled. The only other options to solve this problem are based around specific motherboards for 8th and 9th generation Intel desktops, or you can go way back to hardware from 2008 and install libreboot to eliminate, rather than disable, the IME.
Thanks to [Maik] for the tip!

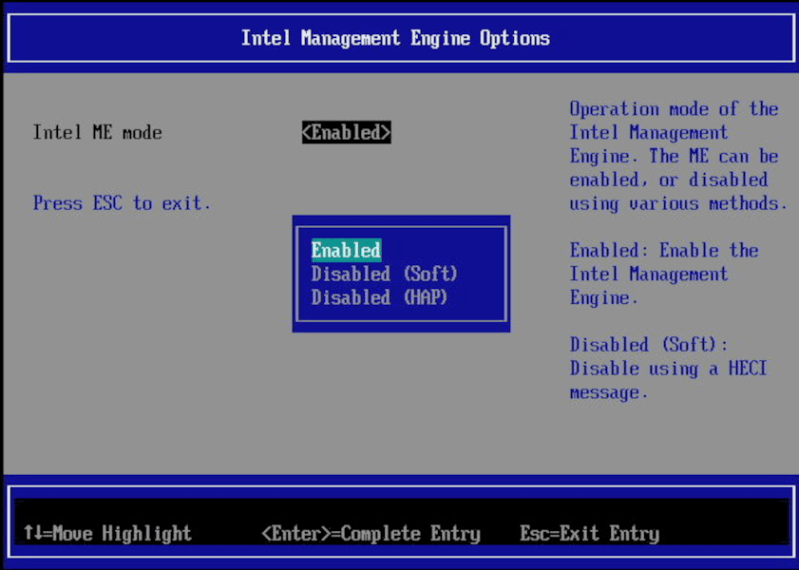














> (with the notable exception of System76)
And Purism.
Came here to say exactly this but you beat me to it
And StarLabs.
These pair of backdoors boot before the BIOS and OS. You have to have AMD and Nvidia hardware w/o it.
And LinuxCertified, Inc ( https://linuxcertified.com/linux_laptops.html)
These pair of backdoors boot before the BIOS and OS. You have to have AMD and Nvidia hardware w/o it.
“For all their advantages, they have a glaring flaw for anyone concerned with privacy or security in the form of a hardware backdoor that can access virtually any part of the computer even with the power off.”
Yes, now does anyone else have access to these beyond one’s local network?
Considering all the bugs that have already been found in routers and the bugs yet to be found i would say this is not a problem, especially for TLA and stuff like this. There might even be intentional backdoors, who knows…
Has anyone yet found a way of activating the HAP bit purely from software? All the guides I’ve seen require stripping down a PC and wiring in i2c/spi/uart style connectors to reflash various eeprom chips. What we really need is a way to disable IME on ay machine, which is reliable and doesn’t risk destroying everything if something gets cirrupted during that hardware based reflashing.
We had filed a support ticket with Gigabyte for the AORUS 5 SE4 (i7-12700H Alder Lake architecture) sample we purchased. Asking two questions:
1. How to disable Intel ME on mobile workstations like Lenovo
2. How to change/disable the Windows 11 Home key embedded in the BIOS to a Pro version license I’d purchased specifically for virtualization support
The response was they “don’t hand out the supplier utility to end uses”. This confirmed the Gigabyte factory and partners do have access to software to modify the locked-down BIOS in a higher privileged mode, but consumers never get a copy of the alluded to utility.
There are other methods to enter this privileged BIOS area, but it involves reverse engineering the calls in the signed firmware images. Also, probing these features randomly could lead to bricked hardware.
Thus, we just blacklisted their lines, as no matter how “good” their Marketers think it is for business… it is against the law to install a RAT on some machines. .. even if it is Intel branded.
Disappointed to say the least. NVIDIA shouldn’t allow these guys near their brand =)
How to change/disable the Windows 11 Home key embedded in the BIOS to a Pro version license I’d purchased specifically for virtualization support
^ I had this issue.
Use this https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/windows-setup-edition-configuration-and-product-id-files–eicfg-and-pidtxt?view=windows-11
If you have Ivybridge Lenovo laptop (t430 for example) you can flash 1vyrain bios and then you get many more options in BIOS including disabling of IME. Doesn’t require disassembly, but as any BIOS flash presents minor risk that you will brick computer.
But that’s pretty specific, I didn’t see any OS level software that can disable IME, as it’s activated prior to boot.
Seems regional or corporate model specific. On tab 3 of the Lenovo factory bios on the older i7 machines we have options to disable ME and iSCSI if the asset recovery feature was never activated.
The 2022 Gigabyte retail version has very few options in the crippled consumer bios. Even changing the key led color scheme requires their special driver/application. So if you installed any other OS before setting the theme, than you are still sporting gloriously rainbow key colors. =)
Please, check this.
https://github.com/Dasharo/dasharo-issues/issues/111#issuecomment-1500976958
I’ve discovered one year ago that sometimes FPT have a hidden argument to do the same thing as HAP and some more things.
FPTs are usually provided by your OEM in BIOS downloads and such; of course these tools are not meant for the end users, but they sometimes provide it and forget (intentionally or unintentionally) to remove these tools.
Inside some of them, they contain the -MEALTDISABLE argument which makes it generally safe to use it. The only thing is that the Intel ME version must match your FPT version.
Given the reports of vulnerabilities able to take over IME and make it actively malicious (as opposed to the passive potential for malice it usually has), couldn’t someone write a piece of software that people can deliberately install, then have this software exploit the IME vulnerabilities and use them to turn IME off? If a hacker can take over IME for malicious purposes, surely a good hacker can use the same method to take over IME to shut it down.
I’m asking out of genuine curiosity here and trying to ask these questions in good faith. Why aren’t BMCs also discussed in articles like this? Is it simply because they are generally server and workstation tech? Is it because many systems (though not all) with BMCs generally access them via a dedicated network port? Is it that many use firmware based on Linux?Is it the idea that there are standards bodies behind interfaces like IPMI and Redfish?
Is there something more inherently trustworthy about BMCs, or is it that they are far less common outside of the datacenter?
I do not think that I’ve ever seen a IPMI(Intelligent Platform Management Interface)/IMC(Integrated Management Controller)/BMC(Baseboard management controller)/iLO(Integrated Lights-Out management)/… or older Serial concentrators (Terminal Server) outside of server rooms/datacenters. And anytime I have seen them they were considered such a high security risk that they were on one or more isolated secure network dedicated to management.
I was very disappointed to find that many (excepting Dell, Lenovo not tested) vendors either didn’t provide an option not to fail over the IPMI to a (potentially Internet connected) NIC when link was lost on the dedicated IPMI NIC, or provided the option and didn’t honour it. I would not be surprised if there were exploits in the wild for the BMCs because they are rarely to never patched for vulnerabilities.
Yea, while they often run Linux, it’s like any other embedded Linux project and at the mercy of the OEM. and on top of poorly maintained Linux firmware from different vendors, I seem to recall the Emulex Pilot 4 being the dominant BMC SOC and with just one dominant chip, I’d expect potential attackers to have worked to determine any silicon level vulnerabilities.
But then this gets me back to why when we are discussing these ‘hardware backdoors’ no ink is spent on BMCs with either positive or negative comments. With the amount of services consumers consume and the general power of data center equipment over consumer level stuff, these would seem to be a more attractive target.
Does it really all come down to data center IT workers and architects’ ability to set up VLANs?
They can be had in some workstations. And now there is an increasing niche with ‘home lab’ hobbyists.
In general, what I’ve seen aligns with what you say, they will often use a dedicated physical port on a specific management plane. This could be a separate physical network, or a dedicated VLAN. But there are cases where the BMC can present itself on a LAN port pulling double duty a bit like what we see with an ME. In that case, the data and management planes must be separated through the use of VLANs. And where VLANs are in use, I’d not like to be the one in charge of infrastructure config.
If I want to build a router/firewall box using an older intel box I’ll add an additional network card to it and not expose the main NIC to risk.
Very crude post 9/11 tech/requirements. Probably not worth it, seeing how much “computing” has shifted to mobile, showing how much can be done with zero days instead of an official backdoor.
What is the risk of using such a backdoor? Possibly leaking a payload that can be exploited by other parties, as was the case with Stuxnet.
I remove IME on all computers I use just as a precaution since it already had some serious bugs. And it’s basically a backdoor you can’t control.
You need CH341a programmer (modified for 3.3V preferably), VSOP8 pogo pin jig (available on Ali), some recent live Linux distro and steady hand. You can also use SOIC8/VSOP8 clip instead of pogo pins, for me pins work better.
Boot into live Linux on your service computer, connect programmer and (using flashrom) read flash chip on the computer or a board you’re removing IME from. Do it three times and compare or md5 dumps to make sure you got the same every time.
Then run this python script on a flash dump to produce new one with IME cleaned or disabled : https://github.com/corna/me_cleaner . Flash new cleaned dump back into chip and boot target computer. If boot fails try running python script with “-s” parameter on a original dump, that means soft disable, works every time unlike complete cleanup.
You can later use this program to check if IME is disabled : https://github.com/mjg59/mei-amt-check
Using ch341a programmer with Windows mostly produces inconsistent results, so I recommend Linux and flashrom utility for reading and writing flash. There is possibility flashing won’t work without removing chip from the board, but for me it worked on multiple boards.
I use ASProgrammer in windows, I never use linux for flashing. I don’t have a problem with it. It is updated and works great with CH341a
you should also keep in mind that IME is combined with soft TPM. if you plan to plan windows 11 + you’ll have some problems
Nah, TPM is not needed for Win11, just use SHIFT + F10 and regedit on plain install media. Or better use Rufus utility to make install USB from the ISO and there is a checkbox to turn off TPM requirement.
Don’t forget to use ThisIsWin11 utility to get 11 debloated and configured into a usable state.
3 feet of cement renders a laptop secure…. not a fraction less.
IME should be one of those “enabled by only those who actually need it” features. Consumers and the majority of SMB users will never use it, and yet it’s enabled by default. Bad business there Intel.
I use it on my remote computer running VMs. Something goes fubar I don’t have to go all the way to the machine.
I disabled the Intel Management Engine from msconfig on my pavilion x360. Did it to use the thing as a keyboard connected to an external monitor, as the x360 in tablet mode disables the keyboard.
All that does is stop using microsoft software from using the backdoor engine. The backdoor is still there and can be accessed from the net even when the computer is turned off, and cannot be detected by the OS when it is happening.
It’s worth noting that the HAP bit is an intel-provided software measure and it’s uncertain what or how much it really does.
In older versions of the IME you could strip its firmware out completely.
In the next version, you had to leave in the BUP or “bring up” module in place.
In modern versions, you have to leave the BUP modules (plural) as well as the IME’s kernel and many of it’s operating system components in place.
Otherwise, you don’t get a functioning computer.