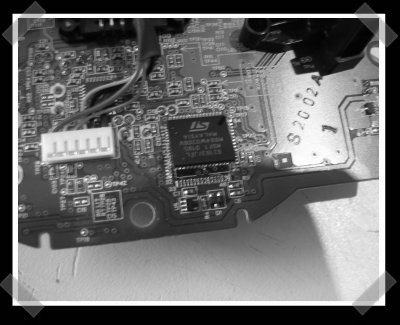
[sprite_tm]’s back with one of his excellent Atmel projects. This time he decided to turn an original XBox controller (cause he likes ’em) into a standard USB HID device. He gutted the custom USB chip that Microsoft installed and replaced it with an Atmel ATMega88. The ATMega required a few changes to the board, but nothing too off the wall.
computer hacks1427 Articles
computer hacks
SenseSurface: Custom Inputs On Your Lcd Screen

[Lindsay Williams] has come up a novel way of constructing custom physical inputs for your programs. SenseSurface is a viable alternative to building a new interface for each application. Simply place the dials, buttons, and sliders on your screen wherever you want them.
A sensor board, placed behind the display, picks up the signals from the inputs. The only limitation to the number of inputs available is the size of your screen. Inputs are held on magnetically, and have a low friction backing to avoid scratching or gouging your screen.
Continue reading “SenseSurface: Custom Inputs On Your Lcd Screen”
DIY Joystick Glove

[Elf] sent in this interesting DIY joystick glove. There aren’t many details on the actual glove switch design, but from the schematic on the site, it seems to mostly consist of micro-switches with some pot adjusted transistors to calibrate the X-Y signals.
Related: Data glove USB interface and Clove 2 one handed input
Render Your Next Render Farm

You might remember [Janne]’s IKEA cluster. Now he’s got a couple of dream rigs in mind, so he started doing 3D renderings of them. Helmer 2 is designed to contain 24 video cards attached to six motherboards with quad core CPUs. (AMD has even taken enough interest to send him some cpus to get started) The rendering really comes in handy for designing the custom copper heat pipes and the aluminum cooling fin enclosure. Still bored, he put together a rendering of a 4 PetaFLOP machine using 2160 video cards.
Update: The Helmer 2 link is fixed.
Turn Your Old Hard Drive Into A Sander/grinder

[Jipa] over at MetkuMods put up an original re-use for old hard drives: make em into power tools. The tiny servo motor that drives the spindle doesn’t generate much torque, but once the drive is spinning fast enough, the inertial force of the platter is enough to make it usable for small grinding/sanding projects. The platters are re-stacked directly on top of each other to increase strength – we’d suggest a few dabs of epoxy to make em even stronger. Once stacked, a piece of sand paper is cut to size and held on by the center platter washer. [Via hacknmod]
Open Source Data Recovery Tools
InformationWeek has great article on open source data recovery tools. What type of tools you use will depend on the severity of the situation. You can use live Linux distros designed for recovery like SystemRescueCD or Partedmagic (the latter being more user friendly). Security tools distrubutions like BackTrack can also be helpful; Helix in particular was designed for forensics work. dd is a standard *nix tool for imaging drives, but something like TestDisk can help you repair partition tables for whole disk recovery. Most deletion operations don’t overwrite the data which means you can use file carving to capture the lost files. PhotoRec is able to find files in a number of common formats. Finally, if you’ve got some serious forensic work ahead of you there’s The Sleuth Kit and many other command line tools.
As an addendum, OStatic put together a list of 5 freeware tools for protecting your system.
Eee PC 1000H Dissected

The people at TweakTown completely disassembled a new Eee PC 1000H and documented the entire process. Aside from showing you the side effects of too much tech fetish and not enough regular fetish, the article reveals all the parts of the new Eee, with a few surprises inside. Although it’s an Eee PC, it’s very different from all of its predecessors.
One of the things the teardown shows is that several parts are far more modular than previous Eee PC models. The hard drive, for example, is a standard Seagate Momentus which is made for desktop systems; it can easily be swapped out. Another easily swapped component is the 1GB SIMM from ASint.
Although their (ahem) stripping process was a bit unconventional, a lot of interesting information was yielded from this teardown. Keep ’em coming, TweakTown, just be sure to clean off your tool when you’re done.
[via Gizmodo]










