Over on YouTube, [The Modern Rogue] created an interesting video showing a slide-rule-like encryption device called the Réglette. This was a hardware implementation of a Vigenère-like Cipher, technically referred to as a manual polyalphabetic substitution cipher. The device requires no batteries, is fully waterproof, daylight readable and easy to pack, making it really useful if you find yourself in a muddy trench in the middle of winter during a world war. Obviously, because it’s a slide rule.
Anyway, so how does this cipher work? Well, the ‘polyalphabetic’ bit infers the need for a key phrase, which is indeed the first thing all parties need to agree upon. Secondly, a number is required as a reference point. As you can see from the video, the sliding part of the device has letters of the alphabet, as well as numbers and a special symbol. The body has two series of numbers, with the same spacing as the central, sliding part. A second copy of the sliding part is also needed to slide in behind the first unit. This second copy is neatly stowed below the body during storage.
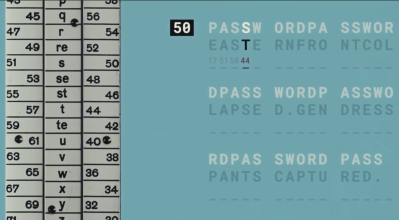
The cipher works by first aligning the starting letter of the (variable-length) key phrase with the reference number. Next, encode the first symbol from the cleartext message (the thing you want to encrypt). You simply look up the letter on the slide and read off either of the numbers next to it. Randomly selecting the left or right set adds an extra bit of strength to the code due to increased entropy. The number is the first symbol for your ciphertext (the thing you want to transmit to the receiver). Next, you move on to the next symbol in the cleartext message. Align the following letter of the key phrase with the reference number, look up the corresponding letter in the message, and transmit the following number onwards. When you run out of key phrase letters, you loop back to the start, and the cycle repeats.
The special symbol we mentioned earlier is not really a ‘blank’; it is a control symbol used to retransmit a new reference number with the existing setup. To change the reference number, the blank character is encoded and sent, followed by the latest reference number. When the blank symbol is received at the other end, the following code is used as the reference number, and the key phrase position is reset to point back to the first letter, restarting the cycle anew. Simple, yes. Effective? Well, not really by modern standards, but at the time of limited computing power (i.e. pen and paper, perhaps a mechanical calculator at best), it would have been sufficient for some uses for a couple of decades.
Why is this Vigenère-like? Well, an actual Vigenère cipher maps letters to other letters, but the Réglette uses numbers, randomly selected, adding entropy, as well as the control code to allow changing the cypher parameter mid-message. This makes it harder to attack; the original Vigenère was considered first-rate cryptography for centuries.
If you’d like to play along at home and learn some other simple ciphers, check this out. Kings and Queens of old frequently used cryptography, including the famous Queen Mary of Scots. Of course, we simply can’t close out an article on cryptography without mentioning the Enigma machine. Here’s one built out of Meccano!
Continue reading “Batteries Not Included: Meet The Swiss Réglette!”