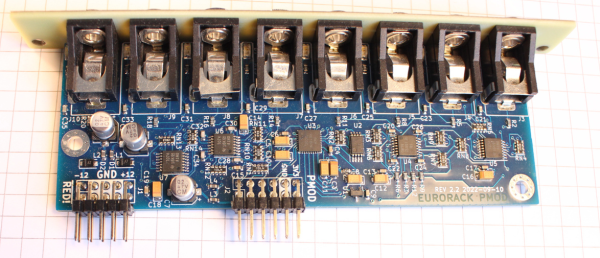
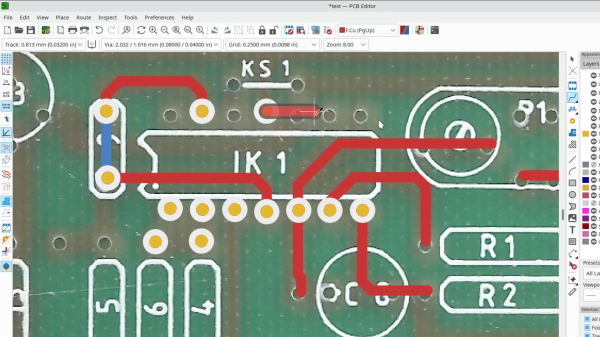
[Sebastian Holzapfel] has designed an audio frontend (eurorack-pmod) for FPGA-based audio applications, which is designed to fit into a standard Eurorack enclosure. The project, released under CERN Open-Hardware License V2, is designed in KiCAD using the AK4619VN four-channel audio codec by Asahi Kasei microdevices. (And guess what folks, there’s plenty of those in stock!) Continue reading “An Open Hardware Eurorack Compatible Audio FPGA Front End”
Day: February 13, 2023
KiCad 7.0.0 Is Here, Brings Trove Of Improvements
Yesterday, the KiCad team has released KiCad 7.0.0 – a surprise for those of us who have only gotten used to the wonders of KiCad 6, and it’s undoubtedly a welcome one! Some of these features, you might’ve seen mentioned in the KiCad 2022 end-of-year recap, and now, we get to play with them in a more stable configuration. There’s a trove of features and fixes for all levels of KiCad users, beginners, hobbyists and professionals alike – let’s start with some that everyone can appreciate! Continue reading “KiCad 7.0.0 Is Here, Brings Trove Of Improvements”
How To Roll Your Own Custom Object Detection Neural Network
Real-time object detection, which uses neural networks and deep learning to rapidly identify and tag objects of interest in a video feed, is a handy feature with great hacker potential. Happily, it’s also possible to make customized CNNs (convolutional neural networks) tailored for one’s own needs, and that process just got easier thanks to some new documentation for the Vizy “AI camera” by Charmed Labs.

Charmed Labs has been making hacker-friendly machine vision devices for a long time, and the Vizy camera impressed us mightily when we checked it out last year. Out of the box, Vizy has a perfectly functional object detector application that runs locally on the device, and can detect and tag many common everyday objects in real time. But what if that default application doesn’t quite meet one’s project needs? Good news, because it’s possible to create a custom-trained CNN, and that process got a lot more accessible thanks to step-by-step examples of training a model to recognize hands doing rock-paper-scissors.
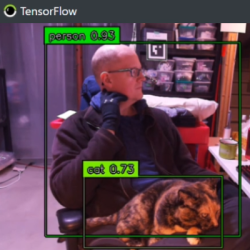
The basic process is this: Start with a variety of images that show the item of interest. Then identify and label the item of interest in each photo. These photos (a “training set”) are then sent to Google Colab, which will be used to generate a neural network. The resulting CNN model can then be downloaded and used, to see how well it performs.
Of course things rarely work perfectly the first time around, so at this point it’s pretty common for some refinement to be needed to increase accuracy. Luckily there are a number of tools to help do this without creating a new model from scratch, so it’s just a matter of tweaking until things perform acceptably.
Google Colab is free and the resulting CNNs are implemented in the TensorFlow Lite framework, meaning it’s possible to use them elsewhere. So if custom object detection has been holding up a project idea of yours, this might be what gets you over that hump.
Stadia Controller’s Two Extra Buttons Get Seen With WebHID
The Google Stadia game streaming service relied on a proprietary controller. It was a pretty neat piece of hardware that unfortunately looked destined for landfills when Google announced that Stadia would discontinue. Thankfully it’s possible to use them as normal gamepads, and related to that, [Thomas Steiner] has a developer blog post about how to talk to the Stadia controller via WebHID. Continue reading “Stadia Controller’s Two Extra Buttons Get Seen With WebHID”
Ban On Physical Mail Slated For NYC Jails, Which Could Go Digital Instead
Prison is a scary place, very much by design. It’s a place you end up when convicted of crimes by the judicial system, or in some cases, if you’re merely awaiting trial. Once you go in as a prisoner, general freedom and a laundry list of other rights are denied to you. New York City is the latest in a long list of municipalities looking to expand that list to include a ban on inmates receiving physical mail.
To achieve this, prisons across the US are instead switching to digital-only systems, which would be run by a private entity. Let’s look at the how, what, and why of this contentious new idea.
Continue reading “Ban On Physical Mail Slated For NYC Jails, Which Could Go Digital Instead”
Methane Pyrolysis: Producing Green Hydrogen Without Carbon Emissions
Generally, when we talk about the production of hydrogen, the discussion is about either electrolysis of water into oxygen and hydrogen, or steam methane reforming (SMR). Although electrolysis is often mentioned – as it can create hydrogen using nothing but water and electricity – SMR is by far the most common source of hydrogen. Much of this is due to the low cost and high efficiency of SMR, but a major disadvantage of SMR is that large amounts of carbon dioxide are released, which offsets some of the benefits of using hydrogen as a fuel in the first place.
Although capturing this CO2 can be considered as a potential solution here, methane pyrolysis is a newer method that promises to offer the same benefits as SMR while also producing hydrogen and carbon, rather than CO2. With the many uses for hydrogen in industrial applications and other fields, such as the manufacturing of fertilizer, a direct replacement for SMR that produces green hydrogen would seem almost too good to be true.
What precisely is this methane pyrolysis, and what can be expect from it the coming years?
Continue reading “Methane Pyrolysis: Producing Green Hydrogen Without Carbon Emissions”