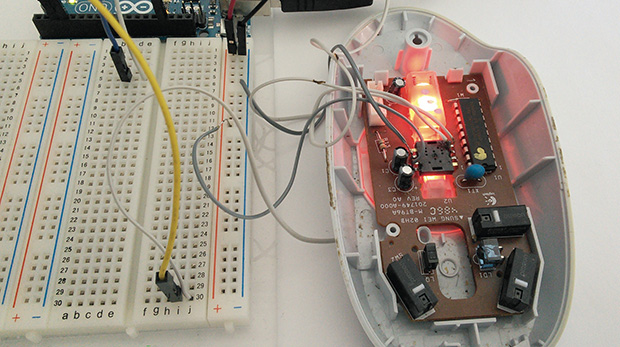
Keyloggers, in both hardware and software forms, have been around for a long, long time. More devious keyloggers are smart enough to ‘type’ commands into a computer and install Trojans, back doors, and other really nasty stuff. What about mice, though? Surely there’s no way the humble USB mouse could become an avenue of attack for some crazy security shenanigans, right?
As it turns out, yes, breaking into a computer with nothing but a USB mouse is possible. The folks over at CT Magazine, the preeminent German computer rag, have made the Trojan mouse (German, terrible Google translation)
The only input a mouse receives are button presses, scroll wheel ticks, and the view from a tiny, crappy camera embedded in the base. The build reads this camera with an Arduino, and when a certain pattern of gray and grayer pixels appear, it triggers a command to download a file from the Internet. From there, and from a security standpoint, Bob’s your uncle.
Looking through the camera inside a mouse is nothing new; it’s been done over the Internet and turned into the worst scanner ever made. Still, being able to process that image data and do something with it is very cool. Just don’t accept mouse pads from strangers.
Danke [Ianmcmill] for the tip.
















I would like to know the keystrokes it uses to invisibly download and install malware.
There are ne keystrokes, this is the magazine’s annual April Fools’ joke.
I agree with you, and for the same reasons. However I must note that some pentesting organizations have managed to stuff a tiny usb hub and an autorun backdoor into mice. They often use it as ‘swag’ for the companies they are testing. Theory goes that the proud manager that handles RFCs will use it and maybe, just maybe, somebody will have misconfigured autorun settings. Of course it isn’t a real attack. That sort of thing has not worked reliably in over a decade.
It isnt that hard to do on a windows machine with a HID device. Press the Windows and R key, then enter in whatever command you want. if you dont know the drive letter, then just loop through them all.
Environment Variables are your friend ;-)
I didn’t read the article (I don’t own the magazine), but my guess is that the mouse behaves harmlessly to stay undiscovered until the pattern triggers the malware to also register as a keyboard and use keystrokes to do its evil business.
Also, from the first excerpt it seems like they discovered this behaviour in an old mouse of theirs while playing around with it and an arduino. They did NOT build the malware mouse, it is already in the wild.
That was published in the last edition, which is the one still on sale next Tuesday (hint hint…) ;-)
The c’t magazine is known for its april fools jokes. They had a couple of really good ones that seemed very plausible, even after a second read.
I am pretty sure this one of them. Having worked with opgtical mice sensors and interfacing with them directly, there’s a lot of things that don’t work as described. Try getting raw image data from the sensor in a usable framerate for doing your own optical flow afterwards…
Uhm. This seems to be their aprils fools joke, because the full article actually appeared in print in the April issue. Note the lack of any information in the article…
true, i bought the magazine yesterday and i’m reading it right now. this is their 2014 aprils fools joke
Hack-a-day and german humor don’t seem to mix well :) Also see the ping-pong robot.
I hope you guys know that the c’t magazine has an annual April fool hidden as an article… And now look at the date.
I’m not saying it’s not an April fools joke (and I haven’t read the original article in the interest of full disclosure), but couldn’t this be done with something like an atmega32u2 and lufa. Starts as a mouse, pattern triggers keyboard mode then revert.
Yes. I’ve actually seen this a number of times and it would surprise me if I was the only one: set up a dev board (uC or uP) to spew out lots of debug over serial on USB and there’s a very good chance that windows flips and starts interpreting it as data from some other peripheral (mouse in my case).
But what’s the point of triggering on a pattern of the user’s mouse pad?
Looks like I missed the point of the article as well. Now I understand the joke. :)
Reading this article a week ago (release date of the current issue for subscribers), I shortly wondered how this “hack” could work actually but then concluded that it had to be an april fools joke.
As well there are some hints in the article, e.g. the picture of a sample malware activation code is ridiculous [huge frame, tiny content], as is the instruction of what to observe in case of malware “activation” – the article tells to observe for *any* HID device showing up; current computer setups can be expected to show some, or does anybody out there still use PS/2 keyboards ?
And eventually there is a “typo” in the article which I strongly doubt would happen to the magazines authors but on purpose: they expand HID to “human *interception* device” … this was the final cue that eventually convinced me it had to be april’s fool.
You all know this is meant to be an april fool, dont you?
ITS AN APRIL FOOL!
c’t is actually well known for doing these in the issue that is the current one on april first.
There is no fix yet so better disconnect your mouse and keyboard. To avoid negative impact you can set your iTunes to repeat eternally, you can only read facebook though.
“The build reads this camera with an Arduino, and when a certain pattern of gray and grayer pixels appear, it triggers a command to download a file from the Internet”
that requires major modifications to the mouse and i doubt there is enough room inside the mouse to get even one of them Arduino minis inside unless you unsoldered the chip from the stamp and dead bugged it inside the mouse.
using the mouse as a scanner if your intent is to sneak the means to copy a book into a library then making a scanner for the blind would work better with one of them hanging book cameras and some software that can capture the image and read the book as speech and the library will be none the wiser if they see the setup and hear it reading the book.
You better disconnect your iput devices until a permanent solusion s found. To avoid negative impact on your computing set iTunes to repeat eternally. There is no fix for facebook though.
I have read the article. It was definitely the April joke. Pwnd ;)
This is an april Fools joke.
As pointed out by a many previous posts, it’s an april joke.
Also the summary of the article here is a bit off.
In fact the article is not about adding an arduino to the mouse.
Instead it warned that there a mice out there, which have the malware integrated inside the optical sensor and the usb controller firmware.
The article states that they’ve been given free mousepads at the CeBIT which had tiny QR-Codes on them to activate the malware.
The ardiuno stuff is only a side story on how they found the codes.
So next time you fall for a German April fool, try at least to get the summary right.
Even though this is obviously an April fools joke, the concept of a malicious attack delivered via a trojanized mouse isn’t new and has been used successfully. These attacks often use the HID emulation function of the Teensy 2 and similar AVR boards to type out the vbscript attack bootstrap code into notepad extremely quickly, which then reach out to staging servers to pull down a metasploit payload, etc… These attacks require some technical naiviety on the part of the user, and a fair bit of luck in timing and setup in my experience.
Such an attack using a Logitech mouse was covered by Hackaday in 2011: http://hackaday.com/2011/06/28/teensy-avrs-used-in-penetration-testing/
Here’s the original article from Netrasoft: http://pentest.snosoft.com/2011/06/24/netragards-hacker-interface-device-hid/
Even though this is obviously an April fools joke, the concept of a malicious attack delivered via a trojanized mouse isn’t new and has been used successfully. These attacks often use the HID emulation function of the Teensy 2 and similar AVR boards to type out the vbscript attack bootstrap code into notepad extremely quickly, which then reach out to staging servers to pull down a metasploit payload, etc… These attacks require some technical naiviety on the part of the user, and a fair bit of luck in timing and setup in my experience.
Such an attack using a Logitech mouse was covered by Hackaday in 2011: http://hackaday.com/2011/06/28/teensy-avrs-used-in-penetration-testing/
Here’s the original article from Netrasoft: http://pentest.snosoft.com/2011/06/24/netragards-hacker-interface-device-hid/
Whoops, commented twice – please delete this one Mods! Thanks.
Doh. Anyways cool story.
Close enough.
http://cdn.arstechnica.net/wp-content/uploads/2013/12/nsa-ant-cottonmouth-i.jpg
I got inspired by this post today and made my own version of a infiltrary mouse device
MouseHack: https://imgur.com/a/uOhyn
Check out the Video of the device working.
nice !
That ain’t a mouse, it’s a RAT!
What ever if you’re using the Uno to do this it’s cheating if you’ve hacked the controller firmware on the mouse then this would be cool but from the picture looks crap.
Pretty obvious joke, and wouldn’t be very good anyway…but it wouldn’t be too hard to load malware from a hacked mouse or keyboard.
Picture this:
1.) Microsoft disabled autorun on external drives and flash drives, but not on optical drives.
2.) Make a USB device that simulates a USB CD-ROM drive with a virus on the “disk”.
3.) Put a 2-port USB switch chip in the mouse.
4.) The first port is normally connected (the mouse signal)
5.) The second port is on a timer; it only connects after 3 hours of inactivity from the mouse…and then only connects for 30 seconds
So, your target plugs in the mouse, uses it all day, and loves it (because if you went through all this trouble then obviously you started with a nice mouse). The target goes home for the day…three hours later a CD-ROM drive shows up, malware installs, and then the virtual drive disappears. Malware installed, even on a stand-alone system. While you were at it, you might even incorporate a WiFi module with a unique ID…so every night when it switches on your malware can transmit data to someone outside of the sealed room containing the stand-alone system…and it only happens at night so it is really hard to sweep for the signal.
All mice shipped to Iraq are in fact enhanced by the CIA and NSA… think about it.. what a good way to get the infected stuff into a system, the mouse sits in stealth mode for months, then does R and off we go, random system reboot and you never see it…