Just over a year ago, [Bunnie Huang] announced he was working on a very ambitious personal project: a completely open source laptop. Now, with help from his hardware hacker compatriot [xobs], this laptop named Novena is nearly complete.
Before setting out on this project, [Bunnie] had some must-have requirements for the design. Most importantly, all the components should be free of NDA encumbrances. This isn’t an easy task; an SoC vendor with documentation sitting around on their servers is rare as hen’s teeth, and Freescale was the only vendor that fit the bill. Secondly, the entire laptop should be entirely open source. [Bunnie] wasn’t able to find an open source GPU, so using hardware video decoding on his laptop requires a binary blob. Software decoding works just fine, though.
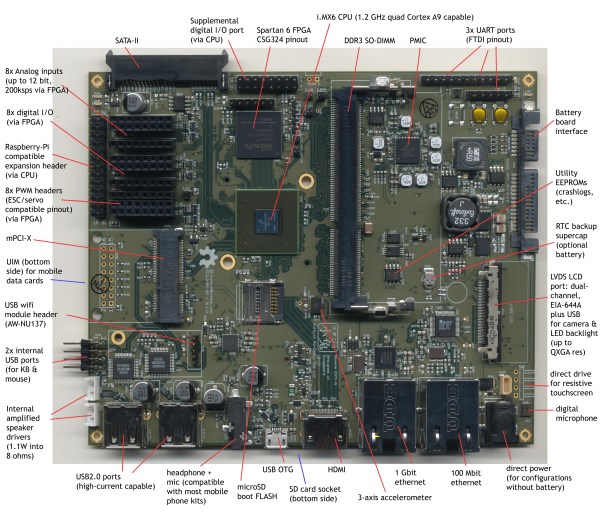
Furthermore, this laptop is designed for both security and hardware hacking. Two Ethernet ports (one 1Gbit and the second 100Mbit), a USB OTG port, and a Spartan 6 FPGA put this laptop in a class all by itself. The main board includes 8x analog inputs, 8x digital I/O ports, 8 PWM pins, and a Raspberry Pi-compatible header for some real hardware hackery.
As for the specs of the laptop, they’re respectable for a high-end tablet. The CPU is a Freescale iMX6, a quad-core ARM Cortex-A9 running at 1.2 GHz. The RAM is upgradeable to 4GB, an internal SATA-II port will easily accommodate a huge SSD, the ability to use an LCD adapter board to run the 13-inch 2560×1700 LED panel [Bunnie] is using. The power system is intended to be modular, with batteries provided by run-of-the-mill RC Lipo packs. For complete specs, check out the wiki.
Despite the high price and relatively low performance (compared to i7 laptop) of [Bunnie]’s laptop, there has been a lot of interest in spinning a few thousand boards and sending them off to be pick and placed. There’s going to be a crowd funding campaign for Novena sometime in late February or March based around an “all-in-one PC with a battery” form factor. There’s no exact figure on what the price of a Novena will be, but it goes without saying a lot will be sold regardless.
If you want the latest updates, the best place to go would be the official Novena twitter: @novenakosagi