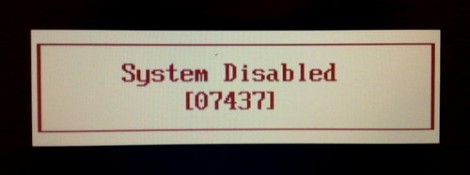
[Dogbert] took a look at the security that goes into BIOS passwords on many laptops. He starts off with a little background about how the systems work. People are bound to forget their passwords, so when you enter a wrong one three times in a row you get a message similar to the one above that locks you out until all power is removed from the system (then you get three more tries). But check out that five-digit number in the picture. That’s a checksum of the password. Some BIOS versions display it automatically, some require you to hold down a certain key during POST, but it’s the pivotal data needed to crack the password.
[Dogbert’s] post doesn’t go into verbose detail about the algorithms he uses to brute force the passwords. But he has posted the Python scripts he uses to do so. Learning how to generate the passwords based on the checksum is as simple as studying the code, which is often the best way to learn.















I always just flash the bios works using a jumper setting and takes just a minute or 2.
hey i have recently come across a connections academy probook 6560b ive had a hard time trying to reset the bios password. i reset the TMP password and stuff so its not going into lockdown anymore but i cant seem to get the bios password off. i tried taking the batteries out i tried default passwords and i even tried some of the tools on heirens boot. theres a bunch of flash tools and password finding tools. i reset the CMOS that didnt help. i really dont know what to do at this point there was someone called mazzif i saw on a bunch of forums/blog sites his tools are specifically for hp pro and elite books but he wants money and i havent found his tools on any freeware sites or torrent sites. it would be great if you or someone on this site could give me some info on what to do from here.
i have the same exact laptop i did the same thing i even used hirens boot tools to flash the checksum n cmos after the reset it still has the password idk how to find it hirens boot also has various brute force methods to find the bios password i let it search for hours with no luck dont bother with the mazzif stuff its junk i got a free copy from a torrent site its not even worth looking into. my guess is besides the cmos theres a secondary memory device of some sort that keeps the password. if you have any info for me or come accross a way around it please email me
we have the same pc its got the i5 2.5gh dual with HT
its a nice laptop im just having a hard time getting the battery to detect n it was brand new when i found it i just gotta update the bios since i flashed everything n installed win7 on it
im pretty good with this kinda stuff but this has me stumped idk where to go from here
were you ever able to figure this out?
please get back to me if u find out anything. the reason i say not to bother with mazzif is cuz all those tools are for hp laptops for consumers what you have is a commercial laptop the 6560b you would find in the store to buy is different than this one slightly different bios n a few other hardware changes the consumer version in stores runs about $450 bucks this commercial one runs at about $1400 its not that the hardware is any better
its just commercial businesses have a higher price for tax purposes not exactly sure how that all works but this pc is not the same as the regular 6560b
Not sure about laptop but I have an HP desktop pro desk from said academy. Had same bios password issue and upon investigation I found a password jumper installed. Mobo two pin jumper printed “PSWD” is now remove – no jumper. Jackpot! now I can boot from USB with WIN7 master (all version) with/without serial needed. I suggest researching your Mobo # and bet you will find success!!!
When you have a Thinkpad with that damn 24RF04 EEProm you’re fucked. Or you pay some shithead to decode things for you or to get a completely new eeprom file with working checksums…
looking at the code is easier said than done..most vendors use obfuscation on their .ROM and flashers now days, and in some cases even in the EEPROM itself. A lot of EEPROM makers even have instruction for acceleration and libs for devs.
If you have a lot of experience in RCE it’s a piece of cake though. I’ve done some ACPI stuff before doing custom ROM flashing, but they didn’t have security.
I think it’s stupid to present RCE like it consists of skill sets easy to acquire..
I think the idea was to look at the code that dogbert provided, rather than at the manufacturers rom code. Dogbert already has an algorithm for taking these checksums and generating possible valid passwords, but his original post didn’t explain that algorithm. Instead, he gave us source code to study from which we could learn his algorithm.
It was nice to learn that the phoenix implementation of the CRC-16 contains a rather severe bug… Who knew?
He reveresed the algo from shadowed ROM..it is looking at the manufacturer’s code..
on most systems bios boot block pushes the bulk of bios code into RAM, decompresses it and runs it in a in-between addressing mode. There is no way you’ll reverse these algos off frequency analysis or blind factoring on this many digits..
Now days though the systems have crypto even in bios, so it is easier said than done. Also I’m not talking about checksums, I’m talking about encrypted code under compression with stub in boot block.
I used to just invalidate the checksum by changing the hashed password on the eeprom, causing it to prompt for a new password. It worked on my old 386/486 computers, probably works now.
i have the same pc i completely flashed the checksum that was the first place i went these connections academy laptops are like fort knox
i wish it was that easy i did that for another computer for a friend he rented it n the rental place locked it down when he missed a payment
Why?? simply open the laptop, connect to the chip and blank the password.
I’ve done this dozens of times. It’s not hard on HP or Dell laptops, and Desktops are a complete breeze.
no you havent this not to this laptop its not a regular bios
I think I don’t have a fuckng clue what the hell you guys are talking about hahaha! XD
Don’t ever lose your code on a Toshiba, they are hell x.x
My wife did this exact thing-set a bios password and forgot it. 95% of my business tax information is on the computer- three unpaid years! The IRS doesn’t care one bit so interest and penalties are running.
Can you tell me which direction to run screaming? I’ve tried almost all of them. :-(
@Marvin: try a tweezer attack?
Cool, this is useful. BIOS recovery programs have failed on the Compaqs I’ve tried, now for some fancy button pressing to recover the checksum instead.
hm. i looked at the page and my computer is a hp dv5 and my hash had 8 characters… none of his files fit that even though it says he has an HP one.
I just used this about 2 weeks ago to crack the password stored on a Compaq N610c laptop.
Worked perfectly!
There are times where removing the CMOS battery doesn’t work, or worse yet, requires nearly complete disassembly of the laptop.
This will save you a LOT of time.
For Marvin’ Thinkpad above – depending on the model, you may be able to do this yourself.
Otherwise, you’re best off buying a pre-flashed BIOS chip for your machine.
If you have a machine with a TPM chip… Good luck… Some can be read (read: $$$), others can’t…
@ NishaKitty : Have you tried making a toshiba password dongle (hint : Google is your friend).
That blanks a lot of passwords on Toshibers…
@junkman:
That’s not flashing… not even close.
I actually had somebody sell me a dell d610 because it had a password on the BIOS and the EU couldn’t remember or figure it out. After a night of googling I found a guy who hooked me up with some info and I ended up taking a paper clip to short two spots the motherboard while I powered it on. The laptop restarted and the password was gone. That was in the summer of 2006 so sorry for the vague details.
I used to just take the lithium battery out and wait a second, replace the battery, and voila! Password gone.
ur dumb go away
A friend of mine did it the hard way: Identify the eeprom on the mainboard, dump, modify and then rewrite it… Though it seems the IBM/Lenovo Laptops don’t show the checksum to the user.
Here’s the Project:
http://das-labor.org/wiki/Thinkpad-EEPROM-Reset
This link has data which is not in english. Do you know the english version of this website
Most of this stuff is bob the local PC tech level stuff. The RCE is obviously over most peoples heads..
He didn’t figure out the algo by analyzing the displayed code..
@marvin can you not jsut do a BIOS update with the IBM utility and reload the default BIOS? It will probably require a USB floppy drive or boot from USB if that option is possible. May save you some time and money. If IBM doesn’t have a utility, try going to the manufacturer’s website (Award, AMI, etc and get their utility :)
doesn’t go […] to brute force the passwords. But he has posted the Python scripts.
If he is stupid enough to use python scripts to brute force a password, Id rather not want to know his algorithm…
Crypto is actually extremely rare in BIOS. But much of it is compressed. OEMs want to use the smallest possible flash parts they can, so compression helps with that.
You won’t get all the BIOS, but you can usually dump the 0xF000 segment and get the the ‘runtime’ code at the very least, certainly the password routines are.
At least in the BIOS world, there are not standards used for the password system. The details of how it is stored and handled are entirely up to both the ODM and IBV. It is even possible for a separate microcontroller to handle the entire process so even the hash is never stored where it could be dumped.
As for the old pull the battery trick, this depends on the BIOS using the batter backed up ‘CMOS’ that, IIRC is part of the RTC. It has become increasingly common dedicate a block or two on the flash part to store nonvolatile data rather than using the battery backed up RTC CMOS. So pulling the battery won’t accomplish much. But it is not that uncommon to have a jumper to clear a system’s passwords.
Regarding thinkpad: They have a boot block procedure too. If you cant find the recovery procedure you order a new chip for like 10 bucks.
Actually IBM isn’t the worse..HP/Compaq is, and their accessible support(forums etc) are beyond useless. Ive never seen a x86 BIOS that didnt have a boot block restore procedure, but they usually work on a IDE or SATA link only.
I just pull out the cmos battery and in like 14 minutes with the cord and everything out everything’s at default
GOD
http://lmgtfy.com/?q=bios+master+password
I did something similar years ago. The BIOS password hash is often stored in the 128/256-byte CMOS RAM. I read the password hash from there (/dev/nvram) and disassembled / reverse engineered a couple of BIOS to crack the hash and show a list of possible passwords:
http://www.zorinaq.com/bpwd/
its not the same with this pc though its not like i put the password in. its a different bios completely than your regular consumer pc. if you would buy this same model the bios would be tottally different cuz its a commercial pc with alot of security n lockdown features i did everything possible its gotta have a secondary device to save the password other than the cmos i flashed it renumbered it to come up invalid n i flashed the checksum evertything ive used various brute force password finders its crazy this is my bios version n date if you look it up n have any info itd be great
Hewlett-Packard 68SCE Ver. F.22, 12/22/2011
SMBIOS 2.6
The best way to recover is to just dissemble the whole laptop and de-solder the cmos battery and again solder it… and assemble the laptop, now u can go on.. its a little technical related but the easy method without going for the above method…
Awesome! Worked like a charm, Acer, Phoenix BIOS.
doesnt work for gateway fx p-172x generating 5 digit code 07340, very disapointed guess i gotta fork up 130 usd to the manufacturer just for a password, cant believe no on has cracked this thing yet.
worst thing is i can use the comp just fine but i wanna change some clock settings and i cannot.
so it isnt even protecting anything just blocking me from my damn clock settings
I have a Toshiba Satellite A210 – 169, with a bios password when i enter 3 times a wrong password i don’t get a hash code back, do you now what the solution is thx
not all pc give a hash code after failed passwords it sucks.
If this does not work try my tutorial: http://youtu.be/9rNsUeI3kHQ
@CNEWMAN402
Hey, great idea, but what if the Notebook is locked (Sysadmin PW, HDD Pw) and there’s no way to get in? In case of newer notebooks (>2013) there’s no possible way to open the case without damaging it – and killing the warranty.
BTW: The algorithm of Dogbert is not working anymore; they changed (Phoenix BIOS) the salt, added some lines to it (add eax, xxx) so there should be an update