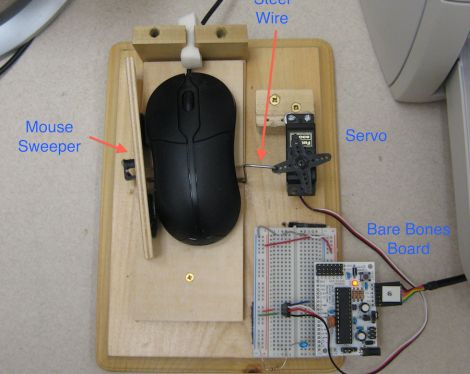
[Jerry] wrote in to share a little device he built to solve a problem he was having at work. You see, every computer in his office has a policy-enforced idle timeout, requiring the user to enter a password in order to regain access to their desktop.
This is a huge pain, since he sporadically uses an old computer for the sole purpose of monitoring some applications running in his data center. With the computer timing out every 10 minutes, he is constantly required to enter his password in order to take a 10 second glance at the screen to ensure everything is OK.
Rather than circumvent the screen saver using a local security policy or by implementing a microcontroller-based signal generator, he opted to create a mechanical solution instead. His computer’s optical mouse resides inside a wooden frame, and is periodically swept from side to side by an ATmega-controlled servo, keeping the screensaver permanently at bay.
Call it a hack, call it a kludge, call it what you will. All we know is that while we might have done it a little differently, it works just fine for [Jerry], and it generates all sorts of interesting conversation to boot.
Stick around for a quick video demonstration of his mouse wiggler box.
[youtube=http://www.youtube.com/watch?v=GxcZMUxAHzc&w=470]















Sorry for this being the first post, but all I can say is it’s pointless. You’re defeating the purpose of your company’s IT policy to ensure unattended workstations are locked. Not only are you putting your own workstation at risk, but you could be breaching company policy which could result in disciplinary action.
There’s a reason why it locks out and you’re dismissing it without asking the question.
This article inspired me to look for a way to do this a little simpler. I found “Screen Saver Killer” on the iOS app store. It does a similar job by projecting a pattern the mouse “sees” and “keeps the screen saver at bay”!!! It even has a timer. Great for working at home!
hehe the mouse i made for darkfall would do the same thing, only with out all the hardware, but who doesnt like some over engineering.
Putting optical mouse on a watch also works.
^^ genius! But what if your IT department forces you to use gear that has not been upgraded in a decade?
It’s missing something… perhaps an arduino-powered web-enabled wifi PIR laser device to tweet the fact that you’ve moved the mouse again.
also pressing win key(opening Start menu) prevents from screensaver
I had the same issue at work. I just made a small executable that sent a double “Scroll-lock” key every five minutes. My boss loves my fix, my IT security guy hates it.
Heh I can think of at least 5 different ways to accomplish the same thing, but this is not one of them. Kudos for originality!
This is pretty stupid. Why not set up a microcontroller with a usb hid device to pretend to be a mouse or keyboard and send a movement or keystroke every so often? Or hell, open an old ball mouse up and stick a 555 timer on one of the axis to send a pulse train. Get a 556 and you can have one timer with a long period which activates another one to send the pulses every once in awhile. Build it on veroboard and put the output on a pair of IC clips and it doesn’t even have to be permanent if you’re lucky.
I just run windows media player on repeat.
Wait, he is in IT and in a data center and finds it harder to adjust the ONE small thing to change the local security policy than it is to spend a weekend designing a rube goldberg device to move the mouse once in a while? He claims it’s a monitoring PC that should already have this change, and if he really is in IT and doing monitoring, then he has the local admin password to get in to do this..
If he was intentionally trying to do it a silly way, then kudos. Silly has a place.
Or, write some software to let you know if something is broken, rather than having to go check every 10 minutes to see if it’s still ok. That’s like the worst IT job ever.
But, kudos for making the automated mouse mover.
Hi Mike Nathan,
I suggest a change to your post. Take the sentance – “Rather than circumvent the screen saver using a local security policy or by implementing a microcontroller-based signal generator, he opted to create a mechanical solution instead.”
And make it say “instead of doing it the easy way, he decided to go down the difficult route instead.”
or just use killsaver…
I wish I had that much time to screw around at work.
this reminds me of this:
http://thedailywtf.com/Articles/Fisher_Price_Technology_Integration.aspx
wow, what a way to completely over-engineer a solution.
i had a similar problem at my work and it was easily resolve by software (http://www.zhornsoftware.co.uk/caffeine/)
I’m guessing where he works the security policy is so anal, unplugging the mouse himself would need a ream of paperwork. (Government department perhaps?) I’ve been on a site where the usb plugs were simply glued in and any spares epoxied over. And having a flash drive on your person would likely earn you castration followed by polite dismissal. Then again if it were that bad, how does he program the Arduino?
Moving apart from the security measures and reasons behind this hack, it is still funny.
It’s not as ingenious as the mouse over the clock, but still works.
If it were me, i would just load the atmega with an USB ASP and make it act like a mouse that moves a bit every few minutes. Put everything disguised in an old flash drive and the system is much better.
Why is it not made of LEGO?? -1
I’ve got the same issue here, a machine hooked up to a 6′ x 12′ projector for displaying the current health of of the datacenter/network. I just dropped it off the domain, and run manual updates, BUT wouldn’t an easier solution be this: http://www.thinkgeek.com/computing/usb-gadgets/ae83/ ?
There are several bits of MOUSE JIGGLER software out there, many can run off a memory stick…much easier and less obvious than this contraption.
I really hope this was made just to fool around.
Otherwise that’s a lot of time in which you could flip the mouse, point it towards a fluorescent light and go have some beer.
My solution to this problem:
Create an application in Visual Basic .NET which uses the built in SendKeys method to generate a key press event every time a timer expires.
This takes one line of code and less than a minute to produce.
Maybe there is a restriction on the software the guy can run on his machine though? You did say he worked in IT didn’t you?
There’s a commercial product that does this – they took a microcontroller from a mouse, added movement code, then stuck it in a flash drive case (like more than one person said above)
http://www.wiebetech.com/products/MouseJiggler.php
This is why application monitoring services usually do things like..send emails, and text messages… Or you could just stick the mouse on top of a clock with the cover removed so the hands move the mouse ball.
“With the computer timing out every 10 minutes, he is constantly required to enter his password in order to take a 10 second glance”
Well there’s your problem right there. A 10 second glance should’t make your 10 minute screen saver turn on. But yea, probably easier to build that device than getting IT to fix the screen saver. I just hope your device shuts off after 10 minutes ;-)
Awesome.
LOL, funniest hack I’ve seen in a while. I think that most of the comments missed Jerry’s point that “it generates all sorts of interesting conversation to boot” which was probably the real design goal. That goal and doing something just because he could do it is what made it fun. Which is why we do this kind of stuff anyway.
I use this:
http://mousejiggler.codeplex.com/
@smoker_dave, .Net is a bit of overkill when vbscript works fine.
Moving the mouse pointer and then putting it back works better than SendKeys.
nothing beats the “optical mouse on a watch” method. it’s that baterry powered / easy to hide / excuse-proof workaround which always works.
get a SH one for – what? – 2-3 bucks?
then again, if one can bring such a machine at work without getting fired, why not bring a cat and tape the mouse on its tale? just saying…
If silly has a place, and so does biology – why not bring in a *real* mouse and have it run around over a flipped optical mouse? Okay, there’s the poo problem but you’d get a pet out of the deal…
Or you could have just bought this
http://www.cdw.com/shop/products/WiebeTech-Mouse-Jiggler-Fast-Version/1712991.aspx
Being in IT, I must agree with Xb0xGuru.
Disregarding or circumventing your companies security policies could well get you fired. Even if it doesn’t get you fired it could result in the company losing clients.
Where I work we have a client that requires regular audits. Among the many things that are checked is what our security policy is (they frequently add requirements, many of which are ‘silly’), they then verify that the policies are implemented and not compromised.
In this scenario, I could see the auditor walking through the office (already secured with card key access and many other protections) and seeing a device not locked down causing us to fail the audit and lose the client. Which incidentally in this case would cost about 30 – 40 people there jobs.
What a way to stop the inconvenience of entering a password. Potentially cost you and 30 – 40 of your co-workers their job, so you don’t have to type a password. Brilliant!
I am all for hacking together a solution for a problem, but when it comes to work, you probably should not be circumventing your companies policies, it could impact a lot more than just you and your job.
In this case, I would ask IT to set up a restricted workstation that is exempt from the policies. That is how it is here, the Phone Operators station and my Nagios Station are exempt from the policies, but restricted to accessing their specific systems.
Solution – Write a screensaver to show the information he needs to monitor..
This would keep the system locked and he could see what he needs with no fuss..
@Doc Oct=Oh no hgow dare someone do something in a way I would not. Only my solutions to others problems must be implimented!
Awesome!
For all of you NON Admins out there:
1. a REAL sysadmin won;t use his admin creds as his normal login creds.
2. a REAL sysadmin will have GPO in place to prevent the installation of unmanaged and unauthorized software.
3. Yes we have 1 AND 2 in effect at my work.
So what he did was a Rube Goldberg way around his screensaver but it would violate our security policy as well since an unattended pc needs to be locked.
I applaud the effort.
If any HaD story deserved the “Arduino hacks” tag…
Good call jm!
Cool hack, I guess…but way over-engineered.
I had a similar issue, and found a simple solution. I monitor a live feed of statistics for a call center, and needed a secondary PC to stay awake despite forced policies from the domain. I used a nice little scripting program called AutoIT to simulate a mouse movement every 5 minutes for 8 hours, then used Task Scheduler to run it at the start of business during the weekdays.
I also don’t leave my equipment unattended. If I’m away from my desk, everything is locked up.
Over, Under, poor, what ever engineered. I can see the reason for such a cumbersum system is to be simply that. Something thats going to be next to impossible to be left on by accident (like a program). I will not argue the idiocy behind the idea being it is a safty measure being surcumvented, but such a delightfuly, refreshing way to do it.
“a-something” was All advantage. LOL
Optical mouse + watch = brilliant. I would have just written a program to send keystrokes every so often.
looks like my other comment was blown away. oh well
I would have built a small treadmill for the mouse, and put the mouse on a wire so it stayed in place while the treadmill ran underneath it.
In my scenario, the domain controlled computer doesn’t allow any software to be installed, including any new device drivers; Anything that looks like or (heaven forbid) actually has memory on it plugged into the computer results in immediate firing. And it has the same lockout screen saver policy.
So all the suggestions for writing a program, script, etc or building a HID usb dongle would not work.
I’d argue the system would not reasonably violate the spirit of the security policy if it externally monitored my presence in front of the computer. IE, a PIR motion sensor or simple contact switch on my desk chair, etc. But that depends on the insanity of your local domain security controller.
But just continuous random movements from a wrist watch or similar does seem like a bad idea.
Not many of you seemed to have actually read his article. First thing he says is:
“Ok, I’ll admit it. It’s excessive and more than a bit Rube Goldberg-ian. But it does work and it beats the heck out of typing in my password twenty times a day.”
He already knows it’s a silly solution. He also doesn’t care. I’m pretty sure he was using this as a learning experience too.
Also, it doesn’t say anywhere that this computer is in some lone cubicle far away from him. I might be wrong, but I get the impression that it’s within sight, and thus never truly unattended.
We don’t know if he was allowed to run his own software stuff. We don’t know if he could plug in something to pretend to be a mouse/keyboard. But it doesn’t matter.
Why do I even read HaD comments :\ It’s a hack. It doesn’t have to be a beautiful solution to the problem.
Anyway, clever hack Jerry :)
There’s a little program called Caffeine that can accomplish this with much less tom-foolery.
Erm, seems like a much better solution would be to find a way to access the data presented on this computer from his main computer. Then virtualize this thing. And… oh whatever. But seriously, that’s pretty well over-engineered.
why not use a teensy as a usb dongle and just send a “click” message every 8 minutes.