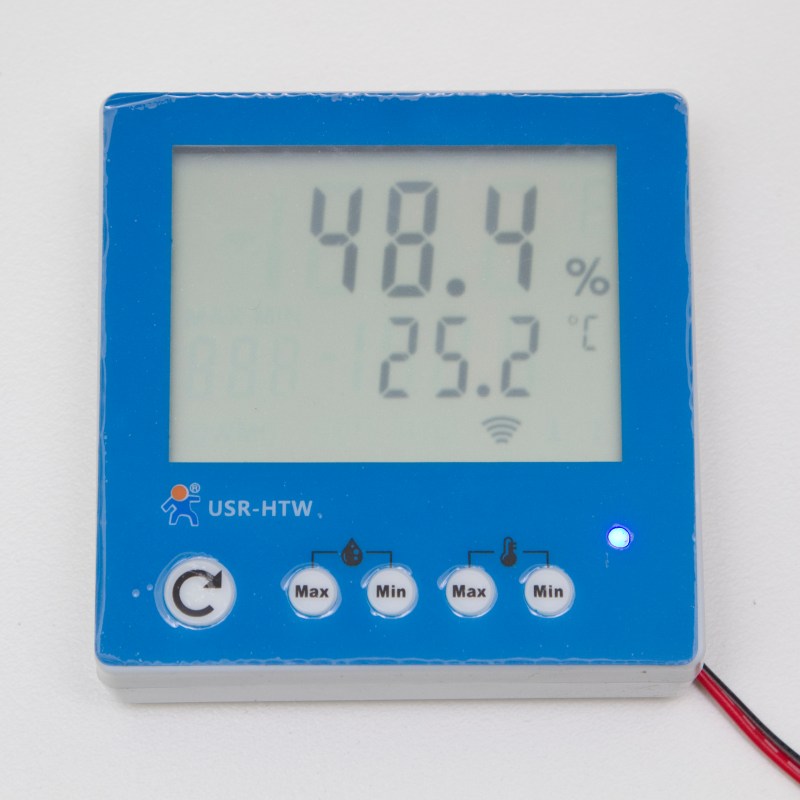
There’s a new piece of electronics from China on the market now: the USR-HTW Wireless Temperature and Humidity Sensor. The device connects over Wi-Fi and serves up a webpage where the user can view various climate statistics. [Tristan] obtained one of these devices and cracked open the data stream, revealing that this sensor is easily manipulated to do his bidding.
Once the device is connected, it sends an 11-byte data stream a few times a minute on port 8899 which can be easily intercepted. [Tristan] likes the device due to the relative ease at which he could decode information, and his project log is very detailed about how he went about doing this. He notes that the antenna could easily be replaced as well, just in case the device needs increased range.
There are many great reasons a device like this would be useful, such as using it as a remote sensor (or in an array of sensors) for a homemade thermostat, or a greenhouse, or in any number of other applications. The sky’s the limit!















While this is a quite lovely idea, it should be noted that you can also go for a 433MHz transciever and a much cheaper 433MHz humidity/temperature sensor. For instance the telldus stuff:
http://telldus.se/products/compability
I still might want to go for one of these since my wifi has a much better reach than the 433MHz (or the z-wave), so it’s very interesting.
Woo hoooo! cheap sh*t from china that connects to my network!
now I can pwn myself! Yay!
That’s what a dmz is for.
You know the communication protocol because the friendly hacker documented it in TFA. If you’re concerned about the wireless humidity and temperature sensor being a source or point of ingress for an attack, feel free to Isolate it on your untrusted wifi network and just allow conforming traffic through your firewall. Where was your wifi kit manufactured btw?
Came across this while looking for documentation for this device.
Actually you know the protocol because it is clearly described in the product documentation. It is one of the oldest if not the oldest protocols used by PLCs and RTUs called Modbus (circa 1979). Took me all of about 30 seconds to connect to a SCADA system like any other industrial controller but a damn lot cheaper.
As for concerns about it being a weak point. As long as the AP feature is disabled or at least secured with a password there should be no concern.
Nobody’s forcing you to put those devices onto the *same* network as your important stuff, you know?
Yeah I always put unknown/untrusted devices on a ‘DMZ’ network that’s walled off from everything else until I’m extra sure it’s not gonna fuck something up. It’s just routed for internet access and nothing else. This includes devices brought by friends and family. Especially family.
Do you use a 2nd router for that DMZ network? Do you have an howto link by any chance?
Easiest to buy a wireless router that has that functionality (guest network) built in – Airport Extremes have had it for a while. Pretty sure there are non-Apple wireless routers that do as well.
While a DMZ is isolated from the rest of your device on the LAN, a device in there has full unrestricted access to the internet with all ports opened. It is not a good place for a potential device that like to phone home or one that have bad security. http://en.wikipedia.org/wiki/DMZ_%28computing%29
May be a VLAN or a walled garden would be a better alternative.
No kidding?
What percentage of people worry about that?
Probably about same percentage of people that wont mount a usb thumb drive they found in the parking lot.
I’d mount such a thumb drive, on my Win98/Ubuntu PC that isn’t networked.
Interesting, but I’d say it’s too expensive. It uses a costly serial Wifi module, which costs ~$20 in single pieces.
Wait till the Chinese develpers switch to ESP8266, that should drop the price significantly.
ESP8266 plus some one-wire interface should be a great hack in the making.
This looks like it’ll work, based on existing DHT/ESP8266 code; works with a DS18B20: https://github.com/mathew-hall/esp8266-dht
This is awesome. I’ve been wishing for a low cost WiFi thermometer. Now it’s time to get cracking on an Android app. I’d love to have the temperature outside my house in the notification area on my phone and TVs.
I want to peel off that protection film SO BAD.
heathen!!!! :-D
+1 lol
I know, right? And that stuff is *everywhere* now. Used to be you had to get a sunburn and wait a few days to have that much fun peeling.
Even more fun when calls you to diagnose their webcam, which is producing blurry images… and you just peel off the film. (Must. Stifle. Laughter.)
ahem, when *someone* calls you
The product also supports LonHand and Modbus.
Well.. this device, when connected in STA mode (client), without anyone accessing it, tries to perform a dns lookup about once every two seconds (208.67.222.222:53) and once every minute a UDP packet is sent to 61.164.36.105:123
So the device appears to be updating time via NTP. What is the DNS lookup it is doing? What is in the UDP stream? Anything to suggest that this is malicious and not just an NTP update?
Here’s a screenshot from CISCO ASA logs…
https://www.dropbox.com/s/9yr84ht7nfv4c2q/Screen%20Shot%202015-03-27%20at%208.03.18%20PM.png?dl=0