Yik Yak is growing in popularity lately. If you are unfamiliar with Yik Yak, here’s the run down. It’s kind of like Twitter, but your messages are only shared with people who are currently within a few miles of you. Also, your account is supposed to be totally anonymous. When you combine anonymity and location, you get some interesting results. The app seems to be most popular in schools. The anonymity allows users to post their honest thoughts without fear of scrutiny.
[Sanford Moskowitz] decided to do some digging into Yik Yak’s authentication system. He wanted to see just how secure this “anonymous” app really is. As it turns out, not as much as one would hope. The primary vulnerability is that Yik Yak authenticates users based solely on a user ID. There are no passwords. If you know the user’s ID number, it’s game over.
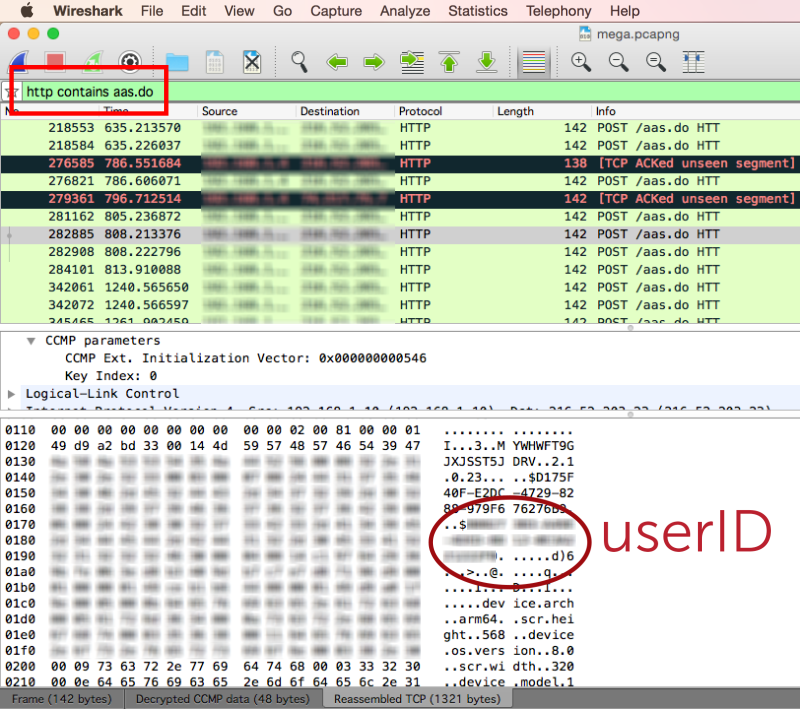
The first thing [Sanford] looked for was an encrypted connection to try to sniff out User ID’s. It turned out that Yik Yak does actually encrypt the connection to its own servers, at least for the iPhone app. Not to worry, mobile apps always connect to other services for things like ad networks, user tracking, etc. Yik Yak happens to make a call to an analytics tool called Flurry every time the app is fired. Flurry needs a way to track the users for Yik Yak, so of course the Yik Yak App tells Flurry the user’s ID. What other information would the anonymous app have to send?
Unfortunately, Flurry disables HTTPS by default, so this initial communication is in plain text. That means that even though Yik Yak’s own communications are protected, the User ID is still exposed and vulnerable. [Sanford] has published a shell script to make it easy to sniff out these user ID’s if you are on the same network as the user.
Once you have the user ID, you can take complete control over the account. [Sanford] has also published scripts to make this part simple. The scripts will allow you to print out every single message a user has posted. He also describes a method to alter the Yik Yak installation on a rooted iPhone so that the app runs under the victim’s user ID. This gives you full access as if you owned the account yourself.
Oh, there’s another problem too. The Android app is programmed to ignore bad SSL certificates. This means that any script kiddie can perform a simple man in the middle attack with a fake SSL certificate and the app will still function. It doesn’t even throw a warning to the user. This just allows for another method to steal a user ID.
So now you have control over some poor user’s account but at least they are still anonymous, right? That depends. The Yik Yak app itself appears to keep anonymity, but by analyzing the traffic coming from the client IP address can make it trivial to identify a person. First of all, [Sanford] mentions that a host name can be a dead giveaway. A host named “Joe’s iPhone” might be a pretty big clue. Other than that, looking out for user names and information from other unencrypted sites is easy enough, and that would likely give you everything you need to identify someone. Keep this in mind the next time you post something “anonymously” to the Internet.
[via Reddit]
















Thanks for the info! As a person who has shot off his “mouth” too many times on the Internet, thinking he was “safely anonymous”. It’s good to know this should I ever decide to Yik. (I haven’t bothered to Twit, and haven’t successfully Skyped.)
Probably should just forget about anonymity on the internet, I don’t think it will ever happen. There are too many factors to account for.
Anonymity on the internet does not exist. Anything you post becomes a permanent and public record.
Post accordingly.
I agree, with the qualification that you can be anonymous *from certain people.* The problems start when either you have a high enough profile that your privacy is threatened by the monkeys on a typewriter effect, or you catch the attention of the figurative eye of Sauron (NSA, FBI, et al).
In other words, you can be effectively anonymous if you’re really, really boring and don’t break any rules not also broken by millions of other people in your country. And don’t have the same name as a terrorist. And don’t associate yourself with any political movements. And are white. And…
*shoots self*
> *shoots self*
Or that is what the NSA tells the public. Brings back the days of Prison Break.
+1 for the Lord of the Rings reference. You might have just made my day with that.
Of course it exists.
every time you click a link or connect to anything the ISP keeps track of all kinds of data, from who owns the account being used down to mac address of the computer, where it’s connecting to, how long it is, etc. so even if you post something to some where that keeps no records of anything, going through the ISP, some one (fbi nsa etc) can fairly easily track down who posted what. or at the very least prove what user on the computer was connected/sending info to there at a very specific time.
The MAC address is pretty easy to spoof. And then there’s public Wifi. Add a LiveDVD or whatever to avoid accidentally giving up an identity.
Though more realistically, a better way to impede attempts to track would be to generate a lot of garbage activity so the real activity is harder to find, as long as it’s difficult to distinguish between the two.
Sounds like a lot of thought went into this system.
Thank for not linking to Yik Yak you fucks.
with every app out there, nealy all of them not just the malicious ones, that require full access to all your data, sensors etc to allow installation, this looks a minor problem to me. The day you start using a smartphone is the day you give away your privacy and security.
You’d think with all the hubub in recent months that developers would know disabling https and ignoring bad certs -by default- is a horrible practice.
hehe, not been a single yak in my area
hacking is so old-school,
new school is making a free app that will transmit (andor store andor sell) information you would NEVER ever give to a company specificaly asking for this information. people sign up by the thousands.
if you cant guess the rest of my opingion(the long rant part i left out), then its very sad
Replacing the X509TrustManager sounds like something they did to make the trust manager work on their dev servers. I did that while testing SNI (Server Name Indication, multiple SSL certs per IP) but I set the trust manager back to normal right after. Definitely not something you do for a release.
Yik yak is really insecure. I reverse engineered most of it in a weekend. With the help of a couple others, we have taken over the whole thing. I wrote a desktop client which allows me to send unlimited upvotes, downvotes, delete other users messages, post to anywhere, etc.
We also figured out how to generate thousands of accounts, automate posting, and even did some fun analysis of different area’s yak feeds.
They used to store their key in plaintext too. Now they fixed it, but it’s still easy to get.
No I won’t give out the code. We’re using it to clean spam and remove bullying posts in our areas. If the code were public, it’d be a mess.
At least you’re doing something positive with it (read: moderation). It does seem to be a much needed service nowadays. Has anyone, who may have discovered what you were doing, really complained about it?
No one who knows about it has complained. Some people wanted me to make the code public, though, or give them the application. I haven’t done so for obvious reasons.
Name your price, We need it for our local school for the same reasons. We want to pay you for your code!
You won’t give out the code, sure, but would you be willing to help me track someone who stole a jacket from me? The post is right there on the yak board. I screenshotted it and can post to it as OP as proof. They bragged about it after I requested that the thief return it.
A few friends and I recently built a tool to help detect and attribute these vulnerabilites, particularly on Android but also on other platforms. Source here.
god forbid someone finds a list of random posts you made in a public message board? Is security really necessary or expected?
@Rick Osgood, the reddit link is pointing to the wrong site.