If you have a wireless controlled garage door, a child’s toy can wirelessly open it in a few seconds. [Samy Kamkar] is a security researcher who likes to”think bad, do good”. He’s built OpenSesame, a device that can wirelessly open virtually any fixed-code garage door in seconds, exploiting a new attack he’s discovered in wireless fixed-pin devices, using the Mattel IM-ME toy.
The exploit works only on a gate or garage which uses “fixed codes”. To prevent this type of attack, all you need to do is to upgrade to a system which uses rolling codes, hopping codes, Security+ or Intellicode. These are not foolproof from attack, but do prevent the OpenSesame attack along with other traditional brute forcing attacks. It seems there are at least a couple of vendors who still have such vulnerable products, as well as several more whose older versions are affected too.
Before you read further, a caveat – the code released by [Samy] is intentionally bricked to prevent it from being abused. It might work, but just not quite. If you are an expert in RF and microcontrollers, you could fix it, but then you wouldn’t need his help in the first place, would you?
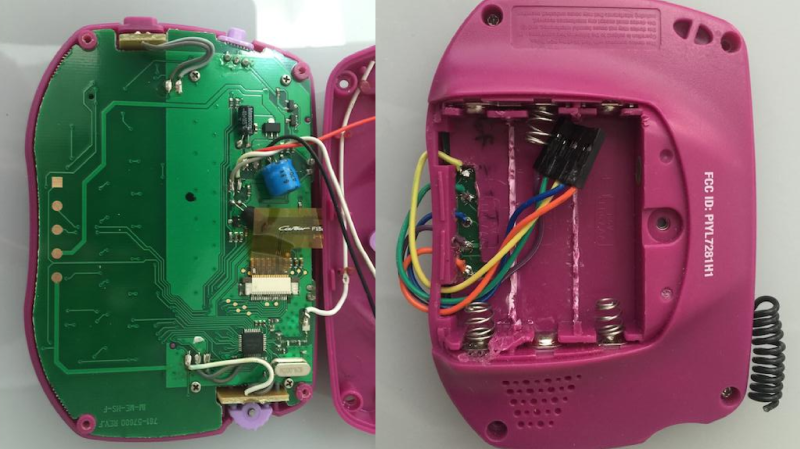
The IM-ME is a defunct toy and Mattel no longer produces it, but it can be snagged from Amazon or eBay if you’re lucky. The Radica Girltech IM-ME texting toy has been extensively hacked and documented. Not surprising, since it sports a TI CC1110 sub-GHz RF chip, an LCD display, keyboard, backlight, and more. A good start point is the GoodFET open-source JTAG adapter, followed by the work of [Travis Godspeed] , [Dave] and [Michael Ossmann].
One issue with fixed code systems is their limited key space. For example, a remote with 12 binary dip switches supports 12 bits of possible combinations. Since its binary and 12 bits long, that’s 2^12, which is 4096 possible combinations. With a bit of math, [Samy] shows that it takes 29 minutes to open an (8-12)-bit garage, assuming you know the frequency and baud rate, both of which are pretty common. If you have to attempt a few different frequencies and baud rates, then the time it takes is a multiple of 29 minutes. If you don’t transmit the codes multiple times, and remove the pauses in between codes, the whole exercise can be completed in 3 minutes.
The weak link in the hardware is how the shift registers which decode the received codes work. Each bit is loaded in the register sequentially, gradually moving as additional bits come in and push the previous ones. This, and using an algorithm [Samy] wrote based on the De Bruijn sequence, the whole brute force attack can be completed in just over 8 seconds. OpenSesame implements this algorithm to produce every possible overlapping sequence of 8-12 bits in the least amount of time.
You can take a look at understanding how the code works by checking it out on Github. [Samy] loves doing such investigative work – check out his combo lock code breaker we featured recently, the scary, keyboard sniffing wall wart and the SkyJack – a drone to hack all drones.















I’m writing up my new open source Zero Point Energy module – but the blueprints are purposely bricked to prevent misuse.
If you’re not going to publish the actual working code, then don’t publish anything at all.
He explains how it works in the video, why don’t you write it yourself?
SCRIPT KIDDIE ANGRY! SCRIPT KIDDIE WANT MOAR E-Z!
So I write the code myself – why would I need the original author? Either publish your work or don’t. No one in the real world publishes half assed stuff, and expects the reader to fill in the blanks.
While I somewhat agree (my first reaction was damn I want to try this on everyone I know’s garage right now,) releasing it in a broken form does somewhat protect him from the almost assured legal nonsense when some tool uses it for wrongdoing.
On the other hand, what kind of script kiddie is able go through the relative difficulty of wiring up an im-me and learning to compile and upload code to it and not be able to work through the code and find whats broken.
Now, who wants to hook this up to a high power amplifier, watch an entire neighborhoods worth of garages open and close, then pray the FCC didnt notice…
that’s some 4chan level chaos right there. time to grab a bag of popcorn and a chair.
Been there, done that with a modified ham radio ;)
I sort of did this with a handheld CB and an RC car remote… Neighbor kids were picking on my brother, and one of them decided to steal his RC car that he had been playing with. My brother managed to wrangle the remote away from him, but turned out the kids’s remote for his other car (That had broken, probably why he stole my brother’s) controlled it so I saw him out there playing with it and the gears started going… Found the input to the transmitter portion of the remote, cut the trace on the circuit board, fed that into the microphone input of my handheld CB… 5 watts easily overpowered the remote the kid had, and I drove my brothers car back to my side of the street before the kid could figure out what was going on (Rather than just pick it up, he chased it down the street with his remote screaming at it)
This guy never ceases to amaze me!
Look him up. It’s completely understandable that he doesn’t want the secret service at his doorstep again. XD
I can see this also being useful as a self contained wireless serial terminal when paired with a serial radio of the correct frequency
Who hasn’t done 300Mhz-400Mhz fixed-code car and garage openers?
Did you miss the De Bruijn sequence being used for the brute force stopping the time from ~30 minutes down to 8 seconds. I do agree that replay attack has been around for a while, but the use of De Bruijn makes this interesting.
The time doesn’t really matter, you can sleep on these systems bruting days if you need to and have a persistent key. The rolling code algos and per-maker challenge-response on ECM ASICs are where the challenges are. These have went relatively untouched for decades except a few academic teams who instantly got visits from government agencies and had to shred all their work.
Yes man id love one of those headloght thingamajigs if u get any plans and code please, (strictly for legal purposes!)
I read through the source code and found at least one of the deliberate faults, but I suspect that there are more. Interesting, but soon enough, getting your hands on the physical IM-ME hardware will be a good enough to prevent people from carrying out this exploit.
I’d bet that it will be ported to GNU Radio and work with all TX hardware – USRP/BladeRF/HackRF/….
I don’t know enough about cheap serial rf modules and garage door opener remotes to know the frequencies off the top of my head, but I bet it would be possible to use a cheap microcontroller combined with a cheap serial rf module instead of going overkill and using an sdr.
Then you may find this interesting:
https://youtu.be/wpKg1sM68SA
http://www.embeddedrelated.com/showarticle/626.php
315, 433 and 868 Mhz are the most common frequencies for most small consumer handheld RF stuff like this. Quite a bit of work has already been done with small mcu’s and cheap RF modules, CAME and NICE barrier “brute forcers” seem to be popular on some Russian forums.
Not hard to do this with an arduino and a cheapie 315mhz transmitter board. Actually a lot easier.
https://www.sparkfun.com/products/10535 and a pro mini clone can be had for almost nothing and the rolling code hack can be done quite quickly.
in fact I thought we had something like that already on HAD a few years ago. The security problem with the older garage door openers has been known for well over a decade.
http://www.panstamp.com/product/panstamp-avr/ Actually even smaller and easier. just add antenna and code.
@timgray1 wrong frequency thats the CC1101 chip not CC1110
Looking for a someone that can hack mi device
With paymeny
I’m suprised that no one has fixed this code and released it by now.
Some are working on it, but apparently nobody’s got an actual working bit of code.
Hey anything New? I honestly want to try this out (not for criminal uses), and I am kinda lazy rn. If no one has fixed it, I will try rebuilding it for an arduino…
Any updates on this
just got my im-me next stop a goodfet and !’m going to dive into this until it kills me.
well i said i was going to get it and i did wow this was a great feeling had to write some bits of the code but man i want to make my own ook apps now
I’m finally on my way to getting one just because I can’t get in line to get a flipper zero right now but have you gotten past the point where it’s not allowing you to use rolling code or is it still fixed code and that’s i?
so you wouldnt be interested in sending someone an email with that info would you? asking for a friend
That took two years huh
Im still wondering if anyone really got samys code working and how??