[Simon] has been using his home alarm system for over six years now. The system originally came with a small RF remote control, but after years of use and abuse it was finally falling apart. After searching for replacement parts online, he found that his alarm system is the “old” model and remotes are no longer available for purchase. The new system had similar RF remotes, but supposedly they were not compatible. He decided to dig in and fix his remote himself.
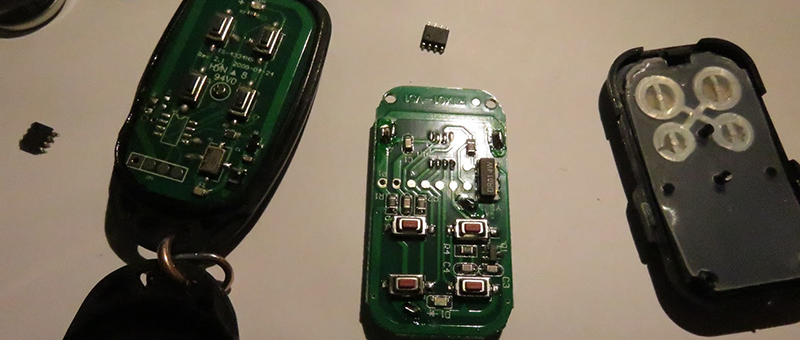
He cracked open the remote’s case and found an 8-pin chip labeled HCS300. This chip handles all of the remote’s functions, including reading the buttons, flashing the LED, and providing encoded output to the 433MHz transmitter. The HCS300 also uses KeeLoq technology to protect the data transmission with a rolling code. [Simon] did some research online and found the thew new alarm system’s remotes also use the same KeeLoq technology. On a hunch, he went ahead and ordered two of the newer model remotes.
He tried pairing them up with his receiver but of course it couldn’t be that simple. After opening up the new remote he found that it also used the HCS300 chip. That was a good sign. The manufacturer states that each remote is programmed with a secret 64-bit manufacturer’s code. This acts as the encryption key, so [Simon] would have to somehow crack the key on his original chip and re-program the new chip with the old key. Or he could take the simpler path and swap chips.
A hot air gun made short work of the de-soldering and soon enough the chips were in place. Unfortunately, the chips have different pinouts, so [Simon] had to cut a few traces and fix them with jumper wire. With the case back together and the buttons in place, he gave it a test. It worked. Who needs to upgrade their entire alarm system when you can just hack the remote?















Impressive! A proper hack indeed.
Another option would have been to program a NEW KEY, because the original key is unknown you could simply reprogram the base unit too, as it is likely also a Microchip KeeLoQ ™ device that supports programming a key. Like a HCS515 (KeeLoQ Code Hopping Decoder) which has a synchronous serial interface.
Both ICs can be reprogrammed in a simple manner, it would probably only take a few minutes to wip up an arduino sketch or something.
There seem to be no special requirements of the key, any 64bit combination is fine.
Nope, wasn’t an option. The receiver also ‘speaks’ keypad for the alarm, issuing arm / disarm instructions. I’d also have to reverse engineer that.
Only a few minutes? Bwahahahah!
I agree that i might have been a little too optimistic there, the programming in the HCS300 datasheet is dead simple, but programming the decoder is quite a bit more involved, but certainly doable.
A few minutes was too optimistic, let’s call it a few hours.
Doesn’t the receiver run another mcu for all the alarm stuff and keypad, and use a seperate KeeLoQ Decoder IC ?
I can’t seem to find one with integrated mcu so i’m guessing this to be the case.
I didn’t look at the receiver in too much detail, but iirc there’s only the one chip on it. I *believe* you can implement KeeLoq in firmware if you know the key, and that might be why there’s only the wrong chip.
I could also be 100% wrong and suffering from having had a “Man’s look” as SHMBO might put it.
Even still… if something went wrong hacking the remote you could just order up a couple more remotes and try again.
Less likely to be true if hacking the base went sideways.
I was curious about rolling key receivers and transmitters like keeloq. The gate remote for my office park uses a HC301. The HC515 supports the largest number of transmitters (7), yet there are about 120 people working in my office park.
I strongly doubt that they have 8-10 decoders set up at the gate, so I suspect they are reusing the same transmitter keys with different button combinations. If every H301 supports 15 functions, so there should in theory be 7 different transmitter models, which brings up the theoretical number of transmitters to 49 per decoder. Still, 3 decoders sounds a bit counter-intuitive.
Anyone else wants to take a stab at a theory?
I think its probably likely that the transmitters are just all clones. At most maybe each company has its own code.
The property management company is likely just concerned with seperating people who have a transmitter from the people that don’t have a transmitter.
If all the transmitters are all the same frequency and there were ever a need to revoke access then they probably just reprogram to one of the other six and redistribute transmitters.
Transmitters are just for access to the parking lot, the real security probably happens at the pedestrian doors to the building and each individual office.
Isn’t the whole point of rolling-code systems that you can’t duplicate transmitters, because whenever you use one of them, the other one will be out of sync with the receiver.
I think you can use the HC301 chips in the transmitters, and handle the receiving side in a microcontroller, which would give you space for a virtually unlimited number of codes. At some point, it might become a bit slow, because every time a code is received, it has to be checked against all registered remotes, for a number of cycles, to allow for out-of-range keypresses.
I was thinking it was 2-way and the algorithm essentially said “the sequence is ‘2, 8, 7, 4, 1, 6, 3…'”, then when you press the remote button the base would respond ‘7’ and the remote would reply ‘4’… then the gate would open.
After thinking about it a bit more, that’s the conclusion I got to as well. Microchip is even publishing the encryption and decryption algorithms on their website, and looking up the manufacturer product page for the remote reveals that they do have a product which can handle for up to 2000 transmitters and is interfaced via RS485.
But you know all, that keeloq is brocken and that it easy be broken?
https://www.schneier.com/blog/archives/2008/04/keeloq_still_br.html
Nice job. Simon strikes me as the type who doesn’t like giving up that easily! :)
Good job, definitely a hack and a half.
Great to see people fix stuff instead of just throwing it out (I expect nothing less on Hackaday), BUT, aren’t the KeyLoQ chips the same ones that are very susceptible to a jam/replay attack? I thought that was why most auto manufactures stopped using them in their key fobs. Please correct me if I’m wrong.
or disable the remote and then wire in some remote and receiver into the keypad so it could be worked from the phone
Nice!
So this is a range of alarm systems where people can just order remotes for online? Doesn’t seem a very secure setup to me
The remotes need to be learned to the system and have the correct manufacturer key. He bought another remote from the same company, which probably had the same manufacturer key internally.
Ah linked like the wifi ‘sync’ button thing too and not just the manufacturer key, got it. So that manufacturer key is basically just DRM for the manufacturer’s benefit.
Think of it more like if every device got its on wifi key. It would take too much storage for a router to store the key for every device you plan to make, so the manufacturer key is a way to derive the wifi key for each device.