For this post, I want to return the word hacking to its nefarious definition. We prefer the kinder definition of a hacker as someone who creates or modifies things to fit some purpose or to improve its function. But a hacker can also be someone who breaks into computer systems or steals phone service or breaks encryption.
There are some “hacker battlefields” that are very visible. Protecting credit card numbers from hackers is a good example. But there are some subtle ones that many people don’t notice. For example, the battle for online reviews. You know, like on Amazon when you rate the soldering iron you bought and leave a note about how it works. That might seem like a strange place for hacking until you stop and think about why people do bad hacking.
In its infancy, the Internet was an networking highway that let you go to a particular host and use tools on it. In fact, I can remember paying DIALOG a lot of money (upwards of $100/hour) to access custom databases online. You could use Gopher to look for particular documents on a server. A hacker, in those days, might be interested in penetrating a particular server and finding individual documents or accessing particular applications.
Hacking People
Despite movie and TV exploits showing password cracking machines and geniuses who figure out passwords using some technobabble explanation, the easiest way to get a password for a machine is usually social engineering. You know, you call someone who has an account on the machine and say something like:
Mr. Green? This is Samantha Rivers with tech support. Our in-phase monitor shows that your machine is being infected by a virus right now. Are you visiting any unusual web sites? No? Well, you better give me your password right now so I can stop it before it encrypts your hard drive with a multispectral quantum entanglement key. If that happens, your data will be lost forever.
This illustrates something I’ve always thought was interesting: hacking a computer is nothing compared to hacking a human. We’ve had human hackers for longer than we’ve had computers. Psychics doing cold- and warm-reading on victims, come to mind. Scams like the pigeon drop or any of hundreds of other scams were perpetrated long before e-mail offering you a share of some Nigerian prince’s bank account were technically possible. Ad men have long been people-hackers as have merchandisers. Next time you are in the cereal aisle at a supermarket, note the placement of the cheap brands vs. the pricey brands. It isn’t an accident.
Not all of this hacking is illegal or even bad. Granted, conning victims isn’t a good thing, but placing pricey cereal at eye-level is just optimizing profit. It all boils down to this: a person-hacker wants to make you do something. Buy a product. Spend more money. Give them your money. Fake online reviews are the newest form of social engineering.
Positive and Negative Reviews
In the case of online reviews, you have several competing interests. The value of positive reviews to my product is pretty obvious. A little less obvious is the value of negative reviews for my competitors. This goes on more than you might think. Several years ago I had a book due out tied to the release of a Microsoft operating system. Microsoft delayed the release, so we delayed the book also. I had about two chapters completely done and maybe another four in draft on the original release date. Despite that, a few days after that date a very nasty Amazon review showed up saying the book didn’t even deserve one star, but that was the least you could give. It also suggested an “excellent” alternative book that I won’t name.
Short of someone breaking into my office, no one had seen more than two chapters of the book. And those people all worked for my publisher, so the obvious answer was the review was totally fake and very likely posted by someone with fiduciary interests in the other title. To Amazon’s credit, they did remove the post once we let them know the review was on a book that wasn’t available yet.
customers immediately trust this product
There is a third stakeholder in all this: the retailers themselves (and the service providers that put ratings on most major Web sites). Think about this: If you were a real Nigerian prince trying to launder money, you’d be shocked at how hard it is. Most people have figured out that scam, and if you were legitimate, people would still assume you were a scammer. If scam reviews become common, the value of reviews will disappear. So the companies like Amazon, Bazaarvoice, and PowerReviews all have a vested interest in protecting the integrity of reviews. For companies like Amazon, that could lead to reduced sales. For the others, a failure of online reviews could put them out of business.
Scanning for Fakes
There have been a few academic papers about spotting fake reviews. Apparently, fake reviewers are more likely to talk about themselves instead of the product. Other ways to spot fake reviews focus on the reviewer. Common sense tells you that a reviewer who has posted just one review or that only reviews one company is suspect. Reviewers that have all 5-star reviews is another tip-off.
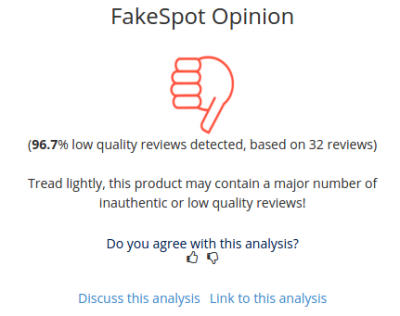 There are automated websites now putting some of these algorithms into use. There’s one for hotel reviews from Cornell. Another recent site, fakespot.com, only works with Amazon. The fakespot site is especially interesting because it lets you view some of the reviews it is calling out as fake and explains its analysis. On the other hand, I plugged in a Kindle book that clearly had fake reviews (a ten-page pamphlet universally panned except by the first eight reviewers who all posted on the same day). The site told it me it thought the reviews were real.
There are automated websites now putting some of these algorithms into use. There’s one for hotel reviews from Cornell. Another recent site, fakespot.com, only works with Amazon. The fakespot site is especially interesting because it lets you view some of the reviews it is calling out as fake and explains its analysis. On the other hand, I plugged in a Kindle book that clearly had fake reviews (a ten-page pamphlet universally panned except by the first eight reviewers who all posted on the same day). The site told it me it thought the reviews were real.
While it doesn’t get as much press as, say, credit card hacking, review hacking can be pretty disastrous to consumers (then again, there has been some news coverage like the video below). We’ve long had the idea of white-hat hacking. Maybe part of that is developing these algorithms and tools to detect suspicious reviews. Perhaps the “good” hacker community will take up that challenge.
One thing is for certain: cyberspace crime and physical world crime are closely related. We’ve had breaking and entering, fraud, scams, and everything else way before we had computers. Nothing so far has stopped all crime, so it is unlikely we’ll squelch all computer-based shady activity, including review tampering. However, just because bolt cutters will open a padlock doesn’t mean you don’t padlock your shed. We just need more tools to help people make informed decisions about the validity of things they read online.
Thanks to [Patrick Williams] for pointing out fakespot.com and providing some background for this post.
















if Samantha Rivers is really with tech support they can get the password.
more like can contact security and have the account shut down and isolated.
Hey Sam, how’s Amritsar?
If this is a real company, they don’t have your password. If they do, their security is terrible. Instead, they should only have the hash of your password. They should have to reset the password, and either give you the temp password or send you an email with the reset instructions.
A good company/provider will never store your password.
“In its infancy, the Internet was an internet highway that let you go to a particular host and use tools on it…”
Doesn’t make sense – did you mean “information highway” and autocorrect stepped on it?
“…In fact, I can remember paying DIALOG a lot of money (upwards of $100/hour) to access custom databases online. You could use Gopher to look for particular documents on a server. A hacker, in those days, might be interested in penetrating a particular server and finding individual documents or accessing particular applications.”
Wow, I’d forgotten all about DIALOG. Thanks for reminding me.
I’d forgot all about GOPHER
look it’s bender :) with gold finish :)
★☆☆☆☆
This blog has TERRIBLE service and didn’t even bring me water OR food! I don’t think they even have a kitchen! I had to make my own food and then use my own internet connection to read their articles as a meager form of entertainment (I tried to nibble on one and it tasted horrible). How is this business still in operation?
It’s pretty obvious this is fake. You’ve probably never even used Samantha Rivers’ tech support before!
If you ask me, a term “hacking” means a highest level of computer science. Someone should have been called a hacker only when he reach something worth admiring, something really big. Not just like stealing someones Facebook account password of his/her close friends, which can easily be done by doing some social engineering skills.
And what is interesting is that this is starting to be harder and harder every day due to rapidly evolving of technology, computer science and security. It’s easily to fake a human then machine. And these machines are getting smarter and more intelligent every day. We need to evolve our minds too, instead of wasting our days on watching brain-washing TVs and browsing Facebook feeds. It might be a good idea to learn and read a lot.
Anyway interesting article, thanks for sharing!
Regards,
Adam
That’s a weird comment coming from someone with a scam facebook hacking app linked to their username.
I was just about to say that.
The sad part is I’m not sure if it’s satire or the poster is actually stupid.
Looks computer-generated to me.
5 star. Excellent seller, fast delivery, will recommend to my friends
Sometimes my reviews look just like that, just because the site wants a minimum of xx letters in each review.
Indeed even my review may look fake. Or some sites want the customer to answer with a rating, experience with seller, shipping and overall satisfation. When a maybe fake IS fake is when they just seem inappropriate to the context, as when someone says “product works, 1 year warranty” of an action figure.
Good article. Has anyone seen the ads for “Addium” on facebook? They claim it’s a pill like what’s in the movie, “Limitless.” The add looks like it’s from CNN. I dug into it and saw the amazon reviews (at the time) were almost at 5 stars with raving reviews. I kept scrolling down and saw some people say it was like a caffeine pill. I noticed the pattern. People rating it bad were “Verified” buyers. Most of the good reviews were not. Of course, a whois of the fake CNN site as well as the Addium website revealed they were both hosted by the same service. It looks like Amazon may have deleted many of those reviews now though.
The article mentions people hacking. In this context, one of the oldest professions has to be that of the “professional” panhandler. You all know the type, able to elicit the desired emotional response from his mark, with the goal of opening the wallet…..
In my opinion, the ad writers and marketers are no better than the bum on the street that gets you to give up your hard earned cash.
Who hasn’t noticed the similarities in all the television and radio ad campaigns that get the best response?
Here’s a list of some additional academic research re:online deception in social networks that you may be interested in.
https://hackaday.io/page/1447-list-academic-papers-online-deception
Until a few years ago I was oblivious to the rampant use of fake reviews; sybil accounts; astroturfing; trolls; etc. – Something that only happened in movies and on t.v., or so I thought.
The results on sites like Amazon/Yelp is interesting and at minimum based on an actual product of service. What blows my mind is the pervasiveness of these deceptive practices on crowdfunding sites like Kickstarter and Indiegogo – for products that don’t exist and people with no history.
The economics of deception is incredible – Millions of dolllars to bad actors, lubricated by fabricated social proof.
New rules.
1 discard all full star ratings.
2 give most weight to mid star ratings.
3 screen low star ratings for specifics. If the specifics match roughly across
reviews then accept the negative comments.
4 A few low star ratings are to be expected due the left side bell curve users discount those.
5 spin that wheel…
Reading the low star reviews with a bit of knowledge also helps. I was looking for a countertop dishwasher, half of the 1 and 2 star reviews were that the hoses leaked at the seals no matter how much you tightened them. The pictures showed the hoses had plastic nuts. What little plumbing I know says that no washer made can save you from stripped threads, and that Teflon tape is cheap insurance. Had that dishwasher for 5 years till I moved somewhere with a full sized one. Never a single leak.
Unless a “this product sucks” reviewer gives details, it’s about as valuable as “amazing would buy again A++++”. Once the reviewer gives details, it gets easier to sort out the folks who understand why something broke from those who don’t realize they are the reason it broke.
On the other hand, I hate that Amazon wants me to do more that just give a number of stars for some items. What can I say about a litter box I bought for my cat, or book 4 in a series where I’ve written a bunch on books 1 and 2? Anything I can write is either too verbose or of the “great item, glad the price was cheap” quality. A simple wordless number of stars is just as meaningful.
That is quite annoying, that they always want a rating with text. Sometimes an item already has hundreds of reviews. I don’t need to add to a sea of crap when somebody else has already done a better job explaining, I just want to rate my usb cable / trading car / lightbulb and be done.
@wilbertofdelaware
I don’t think discarding full star reviews is a good idea. If a product does exactly what it’s supposed to cheaply and efficiently, and you have literally no complaints, why not give it 5/5? I’m not talking about something complicated like a computer game or a novel, I’m thinking of, eg, power adapters or screwdrivers. I would be suspicious if the *average* is full starts, given more than a handful of reviews, but not for individual reviews.
“I received this product at a discount price in exchange for an honest and unbiased review.”
Really is cranking the Amazon review signal to noise ratio way down. If I’m searching for a product I generally cross ones of my list that have reviews like this. You can filter out these reviews by selected verified purchasers only, but when you are searching among dozens or hundreds of products, you can’t fix the search. Not only that, it games the entire system and products with paid for reviews are much more likely to be purchased, so they end up higher in the popularity list.
@russdill
I take paid-for *negative* reviews more seriously than just about any other. :V
Amazon make all their review data available as an open data set, so you can do analysis on it yourself, as I wrote about at https://www.linkedin.com/pulse/100-shades-grey-other-amazon-review-discoveries-mark-chopping/
Do you have to build your FICO rating?
Do you expect to overhaul your school grade?
Would you like to hack your duping mate Email, whatsapp, Facebook, instagram or any interpersonal organization?
Do you need any data concerning any database.
Do you have to recover erased documents?
Do you have to clear your criminal records or DMV?
Would you like to expel any website or connection from any blog?
you should contact this programmer, he is solid and great at the hack employments..
contact : hackerkelvinmckinnon14489 AT GMAIL DOT COM
Dealing with custody battles is the toughest and anyone here who relates understands it particularly when you’re dealing with a narcissist. So my ex husband tormented me for months and I needed to get access to his messages and emails to get evidence that would prove his evil. So I started researching for people who would help me get the details I needed. My sister found positive reviews about the Gear Head team, we contacted them and surprisingly, they provided us with access to his messages, social media, gallery, email and contact list. Their email is gearhead (@) engineer (.) com
If I were to hazard an inference, I’d say binary options are more like playing bingo, specifically if your broker prefers to invest on your behalf. That explains why a phoney company that claimed to have made investments on my behalf and cost me a sizeable sum of money caused me to lose all of my investments. To put it briefly, though, I performed some research and got in touch with a hacker outfit called Craker cyberdude are true pros in this field; after an investigation into the transactions was completed, I soon obtained my money back. Craker cyberdude would surely help you get your missing bitcoin back if you let them know about it. They are highly skilled at what they do, much like health care providers.
Thank you
The cryptocurrency market is extremely unpredictable, and many people have fallen victim to internet fraud and lost some of their cryptocurrency investments. I too fell for phony telegram personnel. Due to a security breach at my wallet address, I lost all my cryptocurrency coins totaling 10 BTC. My home may have been forfeited if I hadn’t been able to successfully recover my crypto coins, which made up the majority of my savings and assets. This grieved and depressed me greatly. I complained online, and Wizard Web Recovery was suggested to me. This cryptocurrency recovery company saved my life by assisting me in recouping all of my losses in under six hours. To complete the successful recovery of my cryptocurrency assets, I went ahead and provided the essential requirements and pertinent information. I was ecstatic when I got my coins back. Kindly Search Wizard Web Recovery and chat them up via the website.
Without getting too technical, CyberPunk Programmers uses advanced techniques to gain access to the target device’s apps, messages, and media files. They employ cutting-edge technology to navigate through passwords, encryption, and security measures, giving you a window into your partner’s digital world. But don’t worry, they remain discreet throughout the process, ensuring your privacy and security. When I reached out to them they provided me with a thorough initial consultation. We discussed my concerns, gathered information about my wife’s phone, and determined the best course of action. It was a relief to know that I wasn’t alone in this process and that they had a solid plan in place. Once they gained access to my wife’s phone, they dove deep into her communication apps and social media accounts. They uncovered a wealth of information that shed light on her interactions as I could see that she had several men aside from myself. It was like peeking behind a curtain that had been concealing a whole other world. WhatsApp this lguru on: +44 7848 161773
Thank you Saclux Comptech Specialst For having a professional team, patience, and support have been instrumental in our journey. Your introduction to the world of cryptocurrency recovery has not only empowered us but has also led to our recent home purchase, A testament to the success we’ve achieved together in getting the huge amount of money we had lost in the hands of fraudsters. Thank you for having a dedicated and professional team in your company and a friend on this incredible journey. We are forever grateful for the joy you’ve brought into our lives, I recommend anyone who lost their investment in cryptocurrency to fraud trust Saclux Comptech Specialst To recover all your lost investment. Via: sacluxcomptechspecialst@engineer.com Viber: +44 7782 645302
I have actually gone through a lot emotionally for over 9 months now and there has been no one to help me. I need to desperately access my husband’s whatsapp to find out what has been keeping him away from home but no hacker was down to assist me until I contacted techspypro @gmail.com I actually have been able to get access to my husbands whatsapp messages and gotten all evidence I needed for this divorce.
I have actually gone through a lot emotionally for over 9 months now and there has been no one to help me. I need to desperately access my husband’s whatsapp to find out what has been keeping him away from home but no hacker was down to assist me until I contacted techspypro @gmail.com I actually have been able to get access to my husbands whatsapp messages and gotten all evidence I needed for this divorce.
I’m very excited to speak about TRUSTGEEKS HACK EXPERT, this cyber security company was able to assist me in recovering my stolen digital funds and cryptocurrency. I’m truly amazed by their excellent service and professional work. I never thought I could get back my funds until I approached them with my problems and provided all the necessary information.
The relief of seeing my funds restored was immense, but the experience also left me wary and more cautious about whom I trusted with my investments. Reflecting on the entire ordeal, I realized how vital it is to have reliable resources when managing digital assets. The stress of losing a substantial amount of money was immense, but Wizard Web Recovery provided a lifeline. Their advanced algorithms and professional approach made the recovery process straightforward and secure.
Sometimes last month, my spouse started acting weird which prompted me to have the feeling of getting access to his phone without his consent and without physical access. I started to search the internet for a legitimate and reliable mobile phone spying expert who can access his phone to dig out proof to satisfy my curiosity. Luckily for me I found CYBERWEBPRO1 @GMAIL, C0M through a referral and I reached out to this expert. He gave me his mode of operation and the associated cost for his services which was quite affordable. He requested for few info off his phone which I didn’t hesitate to give him to my greatest surprise within 4 hours I was able to totally access all info off his phone which made me catch him red-handed in his cheating ways. Kudos to Cyberwebpro1 @gmail, c0m for this amazing phone spying and tracking services. He’s the real deal
Details: CYBERWEBPRO1 @GMAIL C0M
Retrieving lost investment funds seemed like an impossible feat for me, especially after I lost $1.1 million in investing with a dubious crypto-mining company. I had almost given up hope until I discovered ASSET RESCUE SPECIALIST. Their work was nothing short of miraculous, transforming my despair into relief by successfully retrieving my lost funds. I initially struggled with doubts, unsure whether any firm could recover my investments. But the exceptional reviews about ASSET RESCUE SPECIALIST caught my attention. The firm’s reputation for helping victims of scams recover their money was compelling, so I decided to give them a chance. The decision proved to be a turning point in my case. ASSET RESCUE SPECIALIST demonstrated its commitment to customer satisfaction. Their team of expert hackers approached my case with a blend of technical expertise, forensic acumen, and a deep understanding of the crypto landscape. They were not just skilled but also empathetic, showing genuine concern for my situation. The process began with a detailed assessment of the evidence I provided, which included transaction records with the fraudulent company. The recovery firm then embarked on a thorough and systematic investigation. Their methodical approach was impressive, revealing their dedication and expertise. They conducted a meticulous examination of the fraudulent operation, which was crucial in the successful retrieval of my funds. The terms and conditions provided by ASSET RESCUE SPECIALIST were clear and fair, making it easy to collaborate with them. Their professionalism and efficiency were evident throughout the recovery process. I was kept informed at every step, which alleviated much of the anxiety I had been feeling. Waiting for the outcome was challenging, but the systematic and thorough nature of their investigation gave me hope. ASSET RESCUE SPECIALIST technical prowess and astute handling of my case were pivotal. Their ability to navigate the complexities of the crypto world and their relentless pursuit of justice were remarkable. Had it not been for the stellar reviews I read online, I might never have found ASSET RESCUE SPECIALIST. The testimonials of others who had successfully recovered their funds were both inspiring and reassuring. These reviews played a significant role in my decision to hire them, and I am grateful I did. ASSET RESCUE SPECIALIST is not just a hacking firm; they are recovery experts who bring unparalleled dedication to their work. Their efforts have been transformative for many victims of scams, and my experience confirms their reputation as leaders in the field. If you find yourself in a similar situation, I highly recommend reaching out to them. Their expertise and commitment could turn your situation around, just as they did for me. Contact information is listed below.
Email : support(@)assetrescuespecialist (.) com
WhatsApp : +1 (475) 309 2808