It doesn’t matter how many bits your password has, how proven your encryption is, or how many TrueCrypt volumes are on your computer. If someone wants data off your device, they can get it if they have physical access to your device. This is the ‘evil maid’ security scenario, named after hotel maids on the payroll of a three-letter agency. If someone has physical access to a laptop – even for an hour or two – the data on that laptop can be considered compromised. Until now, there has been no counter to this Evil Maid scenario, and for good reason. Preventing access to data even when it is in the possession of an Evil Maid is a very, very hard problem.
Today, Design Shift has released ORWL (as in George Orwell), the first computer designed with physical security in mind. This tiny disc of a computer is designed to defeat an Evil Maid through some very clever engineering on top of encryption tools we already use.
At its heart, ORWL is a relatively basic PC. The CPU is an Intel Skylake, graphics are integrated Intel 515 with 4K support over a micro HDMI connection, RAM is either 4 or 8GB, storage is a 120 or 480GB SSD with AES 256-bit encryption, and wireless is Bluetooth 4.1 and 802.11 a/b/g/n/AC. Power is delivered through one of the two USB 3.0 Type C connectors. The specs are sufficient, but are in no way the major selling point of this computer.
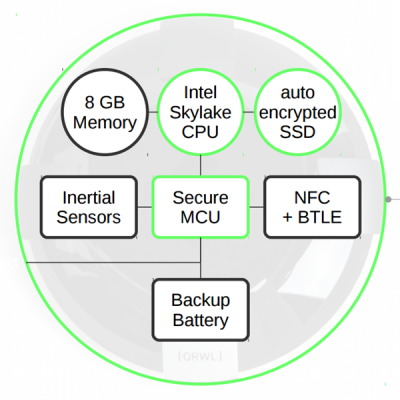 The reason ORWL exists is to be a physically secure computer, and this is where the fun happens. ORWL’s entire motherboard is surrounded by an ‘active secure mesh’ – an enclosure wrapped with electronic traces monitored by the MAX32550 DeepCover Secure Cortex-M3 microcontroller. If this microcontroller detects a break in this mesh, the SSD auto-encrypts, the CPU shuts down, and all data is lost. Even turning on the computer requires a secure key with NFC and Bluetooth LE. If ORWL is moved, or inertial sensors are tripped when the key is away, the secure MCU locks down the system. Of course, this microcontroller is powered by a small internal battery. If nothing else, the (eventual, but hopefully not soon) exploit that will open ORWL’s data up without the security key will be very, very cool.
The reason ORWL exists is to be a physically secure computer, and this is where the fun happens. ORWL’s entire motherboard is surrounded by an ‘active secure mesh’ – an enclosure wrapped with electronic traces monitored by the MAX32550 DeepCover Secure Cortex-M3 microcontroller. If this microcontroller detects a break in this mesh, the SSD auto-encrypts, the CPU shuts down, and all data is lost. Even turning on the computer requires a secure key with NFC and Bluetooth LE. If ORWL is moved, or inertial sensors are tripped when the key is away, the secure MCU locks down the system. Of course, this microcontroller is powered by a small internal battery. If nothing else, the (eventual, but hopefully not soon) exploit that will open ORWL’s data up without the security key will be very, very cool.
We first heard of ORWL a few months ago from Black Hat Europe. Now this secure computer is up on Crowdsupply, with an ORWL available for $700, delivered later this year. The comments for our first post on this computer were unusually entertaining, beginning with the obvious question of why this was designed for Windows 10, and continuing to YAG lasers and cat’s whisker JTAG debuggers.
It’s irresponsible to claim ORWL will never be compromised. There are ways around every type of security, even if that method is a rubber hose and a pipe wrench. The question ORWL presents is if a computer designed with physical security in mind can be a success in both the market place and against an Evil Maid. That’s a question we can’t wait to see answered.















Am I missing something? This is just stupid.
Just encrypt your hard drive and don’t leave it in standby.
That way if someone touches it it already has the security measures this device purports to impose.
Somebody could still pull the hard drive out, copy its encrypted data, and decrypt it at their leisure. This one is designed to erase the drive if someone attempts that.
The only way of assured quick data destruction is high explosives…
There you go. Wrap the HDD in Det cord and have a trigger on the case. Case opened? BOOM! they are not getting any data…. or fingers….
High voltage on the flash chip should do it. Might be slightly explosive.
Could still pull the harddrive platters out and read them in a separate unit.
It’s an SSD, so no platters.
@karboll
It has a ssd, no platters.
Oh yes, explosives and data security goes really well together!
https://www.youtube.com/watch?v=-bpX8YvNg6Y
I like my security to be safe too though…
Personally I would put a conformal coating on the hardware and fill the slack space with thermite. If anyone messes with it then the whole devce is reduced to a molten puddle of iron and slag
+1
No, they can’t. Most HDD encryption systems decrypt per request, and encryption is rather strong. How strong? Combined forces of NSA and FBI were unable to break encrypted drives…
the “evil maid” will install keyloggers etc..
a requisite but insufficient condition for “evil maid”-proof extension of the human mind (memory, computing/reasoning) would be wearable and waterproof so you even take it in the shower…
Doesn’t installing a keylogger require to have a HDD to write on? Or a physical device to be installed quickly INTO a Notebook?
The other thing is: shut down, pull the hdd, put it into some otterbox, go showering. Or (soon) us ethe Dragonbox pyra for not letting anybody get physical access to your device.
mclien,
That wouldn’t stop hardware keyloggers
Last I checked, keyboards aren’t very secure.
Take a cue from the Russians, they put a key logger directly into the typewriter.
I beg to differ. If you encrypted your hard drive with any sensible crypto algorithm and key size, they won’t “decrypt it at their leisure” unless they can employ every atom for the entire lifetime of several billion universes. Weak algorithms are certainly often a problem, but the biggest problem is “key size” and users using something very brute-forceable.
“Just encrypt your hard drive and don’t leave it in standby”, is fair, assuming good crypto and good key size, EXCEPT when you have good reasons to leave it running, in which case super tamper-proof shred-the-keys-and-panic-shutdown sounds like a good approach, which sounds like what this article describes.
It says “the SSD auto-encrypts, the CPU shuts down”, I suspect actually the SSD was ALREADY encrypted, and ORWL just shreds the in-memory keys leaving the SSD as essentially a big collection of random numbers until the keys are provided again.
My guess will be IF it’s ever hacked, it will be by compromising the “secure key with NFC and Bluetooth LE” and tricking it into handing a drive unlock key to the wrong party… Or the tried and tested “other type of brute force attack” https://xkcd.com/538/
xkcd gets it!
Much more likely scenario IF we’re talking three-letter-agencys.
That, or the key will be on a post-it somewhere…
That’s basically how dm-crypt nuke works with Kali linux. They’ve patched the dm-crypt bootloader part with nuke key functions. If you use one of the preprogrammed keys it wipes the public key part of the decryption chain. Just use a few of the often guessed passwords for your nuke keys and the maid or anyone isn’t reading your data.
https://www.kali.org/tutorials/emergency-self-destruction-luks-kali/
install a keylogger or interceptor to steal the private keys and the encryption is meaningless.
Isn’t THAT obvious?
Whatnot says: “install a keylogger or interceptor to steal the private keys and the encryption is meaningless.
Isn’t THAT obvious?”
Yet the device seems to be protected from physical intrusion because of the mesh — the owner of the computer could tell that something has happened if it were opened up. So, any physical key logger would be visible on the outside of the system.
Correct Kevin. Any type of logging device will have to be installed EXTERNALLY to the device as access to the motherboard and any sensitive HW parts is protected by the two clam shells. Any prying, drilling or milling will be detected and triggers a “Tamper event” ==> erasing the encryption Key; what we call Root Of Trust. Making the data on the SSD inaccessible. Not even we can retrieve the data.
Except for back doors in the SSD, there is no way to prove they are secure when it is a “black box” that you have no control over at a low level.
Dan,
We selected the Intel 540s series SSD as we are convinced it provides a great level of protection, we specifically selected the consumer version, which doesn’t include vPro features. vPro is considered a backdoor to some of these drives. That is why the consumer version of it was the right fit for this project.
Preach my brotha!
Which sound great! What happens when somebody tampers with the keyboard? Most keyboards/mice today are USB devices, what’s to stop somebody from hacking a keyboard and installing a malicious USB device with, for example a keylogger. Bypass your “secure” computer and just log everything the keyboard types. Come back later, retrieve passwords. Perhaps a little bit more effort required to decipher what’s a password and what isn’t, but with a large enough sample size you’d probably see that “gee this guy sure likes to type Hunter2 a whole bunch”
Physical security means you have to have 100% trust in everybody who could possibly touch the device.
The current USB hacks may transmit the keys in real-time to a remote collection device so the maid only needs to visit the room once.
Yes, I know that’s the idea, I was a replying to someone saying encrypting a HD was enough.
Keylogger is useless really. You can’t boot the device without the keyfob. You can’t log in without the keyfob in range. You can also configure ORWL to require NFC authentication each time you get back in range. You will have to fake both to boot. Keyfob is using rotating key table so intercepting once over the air is not sufficient. You will have to attack the secure element in the keyfob to try to duplicate. Good luck ! there is a die shield to prevent this ;-)
If you are worried about your data, I also hope you check if there is a keylogger on your computer before using it…. ;-)
It is only offered with 8GB of RAM.
Correct. 8GB is what we offer it as, which should be more than sufficient for most applications.
So, an Intel Chip with M.E. and Windows 10? They don’t need a backdoor in, just waltz in the front…
Indeed, but the ORWL has the added benefit or spontaneously destroying your data if you drop it to hard.
s/to hard/too hard/
OH NOES WICKED HANDS WHAT HAVES YE DUN
Quote from the spec: “Operating Systems: Ubuntu and other GNU/Linux systems, Windows 10”
Currently, the order form only support Ubuntu and Windows 10. I would have liked an option for “other GNU/Linux”.
Damn it I can’t find that 1 hour talk about how a guy spent 6 month with an electron microscope to find which nets of an IC mesh he should connect together in order to be able to get access to the unencrypted bus inside the ASIC…
can’t find the spec saying how long the battery can last…
The built in batterie is projected to last 6 months without the unit being connected to power.
So what happens if the battery is deliberately let run down? Does it detect battery depletion and encrypt the SSD as its last act before dying. The kind of people who really need this type of hardware would need to know such an attack is impossible.
Once the batterie runs out, the SRAM is simply not getting refreshed anymore and looses the key. So yes, as the last action, the key will be erased. As the SSD data is encrypted as it is written, all your data will no longer be accessible.
The main point is to make any kind of attack be so expensive in time and money that nothing inside could possibly be worth the effort.
Saying that, even if you could get an electron microscope to see through the on-die protection, I don’t see how you could get said microscope around the unit without disrupting it enough to power off the device, giving you nothing in particular to look at.
You have the wrong technologies in mind, it is the electrons that are being measured, but they are not the illumination source. OK here is a quantum reality check for you, everything you can see or interactive with via EMR is, electrons. Spectral lines are electrons saying hello. That fancy dye molecule you just invented is just a way of confining electrons so that they behave spectraly in a given way, Reflection and refraction are the same, just electrons having they way with photos of EMR. So if you can illuminate an electron with coherent light it will talk to you. So what frequency do you use, that is the only question. How do you do it without optics, via a diverging beam that causes the “shadow” to be enlarged. The hard part is the source, or it was hard until people got their head around wakefield acceleration.
How to hack the ORWL:
Step 1) Place the ORWL in liquid nitrogen to stop the battery
Step 2) Do whatever you darn well please with the SSD
rtfa…
” The DRAM is soldered, and protected by the active clamshell mesh. Cooling down the secure microcontroller will trigger a tamper event, erasure of the encryption key, and system power down.”
We thought of this too ! The Secure controller monitors constantly the temperature and will erase the key and switch off the unit if temperature is below certain level. Then drive is left encrypted AES 256….
Surely the simple answer is to encrypt the SSD using very long keys held in SRAM, which are erased on tamper detection.
That is what’s done, more or less. There’s a little microcontroller with security features, that gives out the keys when the owner logs in with his smartcard. The microcontroller is the key, and it’s on a hair-trigger to wipe the HD encryption keys on various forms of tampering.
Looks pretty good. Be a complete pain in the arse, of course, if it needs repairing.
So when the good maid moves it to clean the room it self-destructs? If “they” can’t get at your data they can just harass you to the point where you give up and drop your guard. There are so many “soft” reasons why this hardware is garbage.
Looking at the pictures i was just asking myself if the maid wouldn’t call the bomb squad when seeing this “thing” in a room. Or maybe the medias because an flying saucer has landed? ;-)
Between my electronics hobby and my airsoft hobby I’ve left some VERY “interesting” things in various hotels rooms all over the country. I’ve even made it a point to make some of this stuff look even more interesting on occasion, just to see what kind of response I might get. I’ve never had the cops called or been harassed by hotel staff.
These maids are too busy and overworked to give a rats rear end about what you leave in your room.
The device does not self destruct when moved. It shuts down. You need the keys to power it up again.
So it shutsdown allowing the maid to then penetrate the shell without the risk of a self destruct, and then they can install compromising code or hardware? Has that SSD got firmware on it that you can’t audit?
Irrespective of the realities of secure data. There will be a few people getting their rocks of trying to access this device.
Nothing’s really secret anyway – hell the whole country here just had to fill in a form telling the government all our personal details.
Amusingly the form said we could do it on line and recycle the paper form to be kind on the environment. But their server was ineccesable – had it crashed lol
Looks vulnerable to EM probing, but will have to see final product. But honestly if you’ve got really tight bastard enemies that won’t shell out a couple of thousand on test monkeys, then you don’t need one anyway.
Movement and inertial sensors detect and clear it if anything is detected while the key is away.
Midnight earthquake, moving house, bumpy road, pet knocking it down… it’s going to be an inconvenient computer to own due to the amount of natural and commonplace things that would trip the protection.
Movement while away will only shut down the system, not erase all data.
The only way this will protect against a TLA is if a bug in the Intel M.E. trips the self-destruct.
Kessel, The Intel system has no access to any of the security features we implemented. These are two separate subsystems; The Maxim SuC having control over powering up or down the Intel system. No security features are exposed to the Intel system. No Intel Bug can trigger false tamper events.
install keylogger in external usb keyboard, own device.
If that happens on your watch it’s your/customer’s fault…
And there’s the problem you can fix computers but you can’t fix people
Ok, so in no way does it protect against TLA:s then.
Seriously, I celebrate your effort, I just don’t understand why you decided to go with Intel and Win10/Ubuntu, all of which are known to have backdoors.
Maybe I’m reading too much into this Hackaday write up and the ORWL name, perhaps you are not really trying to mitigate TLA snooping but rather industrial espionage.
Anyway, cool project.
TLA snooping may as well be industrial espionage.
Side penetration hacks?
Key processed in the secure microcontroller protected by side channel scrambling HW. Maxim 32550 is used as stated.
I’d really like to see this subjected to the hydraulic press of youtube fame. You know, for science…
me too… Would love to provide you an old prototype if you can set this up ! ;-)
Well if you know the internal layout of the computer why don’t you just fire a bullet through the CPU, in theory it would be destroyed so fast it wouldn’t have time to encrypt the SSD, and since the SSD is, well solid state, it should survive the impact. Just make sure to frisk your maids.
Ehehehehe isn’t that standard practice for bachelors?
I’m still waiting for them to explain how I can know that the SSD that was in the device when it was ship is in the same state when it arrives, because if they can’t tell me that it is safe to assume that it is vulnerable to an attack that has been practised for decades.
If you have data you are storing on a computer that is so sensitive that you need to worry about nation state actors that could intercept the shipment in transit then x86 is not for you my friend. In fact no off the shelf hardware including all mass produced storage is going to be good enough for you, but I suspect you’re just trying to be a dick.
There is a point where you have to just say “this is good enough”, and for 99.9999999% of us this almost certainly is.
I have better ways of securing my data, if I need to do so, this “toy space ship” is rubbish and if you need to attack me rather than address the point I have made then you are the one who is a dick and my point stands, uncontested.
I didn’t attack you I stated what I suspect to be true. I did address your point so it hardly stands uncontested. Perhaps you could do something useful such as enlighten us to your better method of securing data?
You suggested that I was a dick, when you are a the one acting like a dick, then you lie about it and follow up with request for help?
FFS you wankers are pathetic, you go on about what a saint Snowden is and then you don’t take notice of anything he pointed out?
No I will not help you because clearly you are no friend of mine, and you deserve to have the NSA crack your ass until it bleeds.
I said that I suspected that you were just trying to be a dick, and now I am certain of it. You are cutting down what looks to be a great product for an issue that they have little if any control over. You certainly are no friend of mine and I highly doubt you have a better way of securing your data than this device should provide. In fact I’m sure of it because an arrogant asshole like you would like nothing better than to brag about your knowledge. Of course most people like you possess little knowledge and no wisdom.
You still try attack the man but have no answer to what is a legitimate question, how is the SSD secured in transit to the purchaser? I’m not a dick, but you continue to prove what a sad little turd you are, boo hoo your toy is broken by design, grow up and get over it.
If you have to ask me how to secure data better then you don’t even know enough to understand the answer/s. I bet I could just make up some random term and you’d pretend to understand it when really is is nonsense, or I could use a real term and you would ignorantly claim it was bullshit. e.g. Trans-geographic bit-level data diffusion, real or bullshit?
You get one shot, a 50:50 chance of giving me the right answer (but you also have to explain your answer), get it wrong and I write you off as a useless piece of shit and ignore you.
Your move asshole.
Don’t bother talking to Dan. He’s an asshole with a need to have the last word.
Projecting again are you “Mark”, because you did try to have the last word, even when it was “Dan#8582394734” who gave “handsomedave76” the opportunity to have the last word. You poor sad little troll.
Sleep well tonight Dan.
LOL look at the flaccid little troll trying to make threats, your are pathetic “Mark”.
I have to explain why your made up term is bullshit? Nice try troll.
You fail, without even trying. No surprise there, all you did is leave people wondering why a seemingly legitimate question about security could suddenly attract such a hostile response, and that also leaves people thinking hmmm, perhaps the security issue is real after all… So yet another failure on your part.
I’m no troll, I’m not after some childish emotional response from you, even if that is all I got, I did specifically ask you to grow up and answer the actual question. Feel free to go on about it as much as you like but if you can’t give me an adult answer to and adult question, or two, all you will do is score yet another fail.
PurpleTurdBracket is Dan#8582394734. FYI (I’m sure you figured that out).
I only talk to trolls, and I seem to talk to “Mark” a lot. “Mark” is often completely wrong, and almost always useless, even “Mark”‘s trolls are amateurish and ineffective, such a pathetic try-hard. Perhaps that is “Mark”‘s excuse, the need for practice. LOL!
At least ‘mark’ doesn’t constantly change his name, purpleturdbracket.
I fail because I cannot explain why your made up term is made up, or are you saying it’s not made up? If it’s not made up perhaps you could explain what it is and provide a link to proof it is not made up?
You fail because you need to ask that question, because it demonstrates, as I pointed out earlier, that you don’t even know enough to be sure either way and be able to confidently demonstrate why you hold that opinion.
If the SSD is changed, as with any component inside the security shell, the root of trust key is deleted. The unit will not boot. This state cannot be rectified without the 6 digit PIN, shipped separately.
This isn’t to say that it will tell you the SSD is different. All you would know is that the system has been tampered with, and that it doesn’t work at all. In that state, if you want to use your key and PIN to reset the tamper event, you could choose to trust the SSD, install the operating system of your choice, and proceed. But that’s probably not the best choice.
You have no way of knowing if the SSD has had new code loaded onto it’s internal controller. I did not say the entire SSD would be swapped, that would be a rather obvious, as well as unnecessary. This is why I used the term “black box” the internals of the SSD are not subject to audit from the system or the user.
How are you going to stop customs from opening the devices, as is their right? Hasn’t this always been the problem, there are legitimate reasons for opening up gear, but unless you can fully audit the gear you don’t know if it was just a simple inspection or something more. This is really old why do I even need to ask?
As stated, you CAN’T stop it, and you don’t need to audit it – the system ‘breaks’ if you open the enclosure enough to modify the hardware/software/firmware. You can’t keep it from happening, but you’ll know SOMETHING happened. At that point you would most likely choose to not trust it.
But why is customs even messing with this? You shouldn’t be shipping it out of the US. And if you’re that worried about it, why wouldn’t you be going to the factory to pick one up? In fact, why are you trusting this 3rd party at all? Order some 74 series logic and get to building.
I eagerly await your response, because no matter how much of a dick you try to be it’ll just be funny to read.
So this unit is useless if you live outside the USA, or travel outside the USA with it, or have it delivered by a third party? Because customs in many countries does open up gear all the time, sometimes they even misplace it then find it again so you have to have it shipped to you, rather odd that eh?
It is useless then, thanks for clearing that up.
Also, where does the SSD come from, is it made in the USA or can shipments to the USA be intercepted, because the destination is known? You know I am talking about the sort of stuff that has actually been going on for a long time. You do know this is an old problem don’t you, and that nothing you have said actually fixes it? No? The problem is that the SSD is a black box and not even the people assembling the unit can audit it. You are a good example of the Dunning-Kruger effect. That is not funny at all, it is tragic.
Good idea Hirudinea! Hopefully there won’t be any data corruption during that event.
Well even if there was some data corruption depending on what you were looking for and how fast you needed it, say the SSD was full of terrorist info you needed now, it might be worth it rather than risking the drive encrypting, what I’m wondering though is how much energy would be imparted to the whole structure vs. just the CPU, I think you’ed need to shoot the CPU with something like an FMJ rifle bullet, so it just cuts right through, destroys the CPU and passes right through, hopefully, imparting little energy to the rest of the parts. Any gun experts here to help shoot a computer?
Totally. There should still be enough there to work with.
AIUI the drive’s ALREADY encrypted, it stores nothing but encrypted data. It’s en/decrypted on the fly with the keys from the security chip. Smashing the casing with a bullet would trigger the security controller, which would forget the decryption keys, leaving everything on the drive useless. You could smash the security chip but then you’ve erased the keys yourself.
You might be able to get whatever info remains in the RAM with enough messing about, though you’d be fighting time. But that assumes you can access and forensicalise the machine while it’s actually in use, ie the user is sat in front of it. As long as he makes sure to shut down after use, that’s not likely.
The majority of everything would still be scrambled nonsense in the SSD though.
OH, it already encrypted, I misunderstood. In that case a gun would be useless unless you held it to the users head.
Hard drives (unless you’re using some antique from the 20th century) have an option to have a password. Use a decently strong password and nobody is going to crack it any time soon. Doesn’t matter if it’s moved to another computer, the password goes with the drive.
They do have a ‘back door’ to remove the password but it opens over a bottomless pit. Using that function initiates a secure erase process. There’s a command line program that can be used to remove the passwords, it was written as a secure erase program. It first checks if the drive has a password. If so, it uses the backdoor to trigger the erase. No password? It sets one then removes it to trigger the erase. I dunno if unplugging the drive after initiating the erase, then plugging it back in has any effect on the erase procedure.
One thing to note about most SSDs. They have a finite amount of use then they brick themselves to make the data inaccessible. It’s a LOT of use, many petabytes of writes, but the limit is there. Some drives use a hard limited write counter, and will self-brick even if there are no accumulated errors. Some self-brick based on proprietary amounts of errors which indicate possibly impending failure.
Intel’s consumer SSDs are self-bricking. Their commercial/enterprise ones slow down write speeds to a crawl when they reach their calculated end of life, which allows for recovering the data.
If you’re working with insanely massive amounts of data where you’ll be doing writes that amount to a petabyte in under a year, you’d best have a good backup that doesn’t use SSDs, or plan on swapping out SSDs yearly. “Slightly used SSDs, only one petabyte total written to it, still has at least 5 or 6 petabytes of life left, maybe.”
[paragraph 1+2] I really doubt about this. If the data isn’t encrypted there certainly is a way to access it, maybe not for some random bad guy but certainly for tree letter agencies – for which there probably exist some kind of backdoor in the firmware anyway… And even if the data is encrypted it doesn’t guarantee anything. The algorithm could be weak or the implementation could be wrong. You can’t check it, it’s security trough obscurity. If i want to protect the data on my HDD i really prefer some open source encryption tool with known strong algorithms. (Balefulness(?) to the ***** NSA that killed TrueCrypt by the way! [nasty words censored])
The tamper-resistant packaging seems like the only part I couldn’t reasonably imitate (notice I didn’t write ‘replicate’) with a weekend, a trip to MicroCenter/Frys, and open-source software. At least now the Blackphone owners have a desktop to go with their paranoia, err, I mean cell phone.
Two things that I think they got completely right are the price and being Open Source. That puts them way ahead of the Silent Circle folks on my score card. Some things that I think could have been done better were supply chain verification, wider OS support, and pedigree.
Maybe one of the folks on the project is a hardware security rock star and I’m just out of the loop, but the biggest risk of all is, who are these people and why should I trust them. Silent Circle has Zimmerman and even if he’s just licensing the use of his name (I’m not stating this is the case, merely postulating the hypothetical) he’s a trusted resource in the community and some level of trust is thereby extended to the product through his participation. What reason do I have to believe beneath the tamper-proof mesh in all the hardware/firmware/software there isn’t a backdoor of some sort, maybe even mandated by some TLA?
Since, on a scale from snooping-spouse to three-letter-agency, I fall towards the lower end, I’ll stick to the 100% fool-proof zero cost solution of taking my laptop and phone with me whenever I leave my hotel room. I’ve yet to meet the evil maid that’s been able to crack that security measure.
Protection from TLAs is an interesting thought exercise, but the more common scenario is guarding against theft of your intellectual property. I’ve spoken to photographers who are very happy with the idea that if somebody steals their computer, momentarily neglecting the fact that they’ll end up with a doorstop instead of a computer, there is no chance they’ll see their photos turning up on-line with false attribution.
It’s even more reassuring when you extend that to more sensitive data like medical records, legal records, etc.
What I’m wondering is why can’t I just short the mesh and then have my way with the internals?
You can, if you buy enough of the devices to discover what the detection circuits tolerances are, then so long as you use a method that stays within that range you can open up a big enough hole to get an endoscopic type probe into it.
But who make a physical hole when another type is possible?
If you can get a coherent x-ray source over the right part of the right chip and a digital x-ray detector under it you can use x-ray diffraction to read the electron densities of the memory where the keys are sitting.
This is where being an open design causes as many problems as it solves, anyone wanting to crack the device gets to practice as much as they like until they perfect their methods.
I’d be surprised if this would work reliably with the described meshes in the path of the lightsource. In fact I’m not sure this would work without the case and mesh in place, I can’t find a single paper describing the use of x-ray diffraction or any other x-ray technique to read the contents of memory of packaged devices. That is ignoring of course that the types of attack this is designed to prevent probably wouldn’t be feasible if you need to drag a bunch of equipment into the location the PC is in as it would likely draw attention. If you just want the data from the machine and don’t care if the user knows you are getting it quickly destroying the Cortex-M3 would be the way to go.
So I am wrong because you are ignorant, well I refer you to earlier comments regarding your credibility. I know for a fact the technique has been known about for at least 10 years, and even then discussions around it were in reference to even earlier physics. So what does that make you, nothing more than an opinionated amateur?
BTW have you ever noted how much “gear” a maid wheels into a room without people taking any notice? What about multiple “maids” suddenly converging on one one room, how much gear could you temporarily get into a room in under 5 minutes?
To be blunt, I genuinely think you are stupid and would never want to rely on a person like you for anything important where my interests needed to be protected from people who I know are capable of so much more.
Is that rude, am I a “dick”, I don’t care, because it is the truth even if you don’t like how I put it.
http://imgs.xkcd.com/comics/duty_calls.png
Technique being discussed and technique being demonstrated are two different animals. Someone who wasn’t bullshitting or trying to be an arrogant ass would provide at least a shred of evidence when challenged. I hadn’t thought about the amount stuff housekeeping normally drags around with them and it is a good point, though I’m still not convinced that x-ray diffraction is feasible in this case.
As for you questioning my credibility because I can’t prove that your made up term is meaningless drivel anyone here with basic reasoning skills understands what you are demanding is nonsensical.
There is nothing wrong with my reasoning, you asked me if it was nonsense, read your own words, fool. That is why you failed. As for if it is nonsense, I guess you will never really know but the language does in fact parse correctly so strictly speaking it is a sensible term, even if you have no idea what it means which clearly you do not, but your answer does illustrate a point about you to others, people who do know the answer. You try to dictate terms, that is your MO, but I did not allow you to do that and when backed into a corner you resorted to deception in order to escape, except that you did not escape and now people have a clear picture of what you are like.
The demonstrated vs possible false dichotomy does you no good either, because you can simply be dismissed by pointing out your already demonstrated membership of the category “ignorant”. It is not a question of if it has been demonstrated (and there is a secondary flaw in your thinking there too) it is a question if you would ever have a chance to access such knowledge. The secondary flaw is that what is possible is in fact a legitimate issue because this discussion is about what could (possibly) happen if you use that product in the future and assume that certain things are not possible.
Your use of such fallacies demonstrates the weakness of your reasoning, which is ironic given your above claim above regarding mine.
Oh gods, Dan’s come off his anti-dickhead pills again. I’ll call the hospital.
He seems to think people come to forums to prove who’s objectively correct, and thereby win.
The mesh is a series of interlocking circuits carrying digital data generated by the random number generator on the secure microcontroller. The secure micro monitors the data coming back, but also the impedance of the circuit. Shortening the circuit with a jumper will trigger a tamper event.
In addition, the trace width, pitch, and depth are all significant. With the traces so thin and so shallow, the goal is to ensure no physical intrusion can succeed without disrupting the circuit.
Just hoping this is the case is not good enough, obviously. This is why we are contracting with a third party FIPS 140-2 security review company to perform exactly this kind of testing.
The circuit cannot be so sensitive that it is triggered by stray radiation on all that receiving surface. So the truth is it still comes down to being able to tap the tracks with a circuit of a different geometry that emulates the characteristics of the bypassed section. Not hard if you are always dealing with a known configuration. randomising the tracks would have been smarter. This is why I pointed out that there are some down sides to open designs.
How are you with electronics? You have some more work to do I imagine.
How would you propose to bypass a portion of the mesh with an identical external circuit to trick the device?
If the internals poll the mesh frequently enough, your tamper will be detected. You can’t simply add something in parallel because it would alter the circuit. You can’t break the circuit for obvious reasons, but the only option is to (at in incredibly rapid rate) break the circuit, then re-attach your external circuit.
Oh well.. I like the idea, but I don’t see hardware being broken into very often… heck, I don’t see things ‘hacked’ very often either… Most thefts and break-ins I’ve seen are weak passwords and poor security practices.
As mentioned above, you can’t fix people.
( I like the det-cord around the HDD idea… good luck getting through customs though )
The point is it is an open design so you can spend as much time as it takes to get such a circuit working on your own copies, and they didn’t do the obvious by randomise the layout per unit or even offer 10 variants to make such a penetration that much harder. So what do I know about electronics, enough to see that obvious improvement, so why didn’t you?
The mesh is printed inside and very fragile to drill or mechanical stress. So, lets imagine you find a way to solder on the inside without making a hole or disassembly. Then, each track is very fine and close to another one. Each track is the neighbor of a separate signal, so you need to solder on one and bridge to another location to short one. Then, you need do this multiple times to make a hole large enough to insert a probe and then attack the right place…The issue is the secure controller generate a random pulse going through these tracks and check the impedance. So, you need to do all the above using a process that does not add any impedance on the line (capacitive or resistive) or the keys will be wiped in 50us….
These shield are used in recent payment terminal and we pay some companies to do these tests. We will provide reports when completed…
“Never say never”
:o)
Am I the only one impressed with its roundness?
No. Even Apple is jealous.
All the great ideas about how to get into this unit / round the encryption and the truth about three letter agencies is they’ll just bug the hotel room and watch you type the password…
Oh, we have detection tools for that sort of thing…
It uses a physical key fob. A password isn’t enough. But yeah, if you have physical access to the computer, you probably have physical access to the user as well.
Fix *2. I came up with a foolproof way to store encryption keys which is NSA/CIA proof. Its just a circular buffer using glow in the dark ZnS plastic material on a hard disk platter; turn the power off or interrupt its logic circuitry even for a microsecond and the buffer gets disrupted enough to scramble the key beyond recovery.
In fact this could be integrated into existing hard disks with minimal effort especially low density ones, just by adding the unused second platter on top of the first with coating insulated under a robust UV/IR transmissive material.
Delay line memory, bro. Simpler, cheaper and no disk hacking required…
I think a laptop hard drive surrounded by plastic explosive would be easier.
I appreciate that it was posted on hackaday and that Stefan is answering questions here.
It’s not redneck maid proof though, looks too much like a roomba, they’ll be all **BLAM** **BLAM** **BLAM** “It tuk rrrr jrrrbs!”
It looks almost like the disk from Tron movies. Except for the hole in the middle. And you cannot throw it. And it doesn’t glow. Still looking yummy though.
I wonder if this could me made as a wearable device, on your arm, with a screen mounted also on you arm, big enough to see and type in the same time. And with an RFID tag embedded in your arm as a key (shallowly so they won’t cut your arm for it). And a backpack with enough power backup. As seen in Red Planet movie.
> And with an RFID tag embedded in your arm as a key (shallowly so they won’t cut your arm for it).
If it is designed and sold that way, everybody knows that it is in your arm.
If it is detectable, it is detectable in your arm. If it is not (or not easily) detectable, why put it in your arm in the first place?
Why do these weirdos put anything in their arms? Don’t they have pockets? I really can’t see the point of implanting anything unless it’s going to be necessary to have it 24 hours a day. Currently there is nothing like that, except perhaps pacemakers and medical stuff. Probably why most of these “cyber” implants look like a solution in search of a problem.
I can’t believe they’d build an evil computer, especially one that can’t be cleaned! Just awful.
Nooo…
Nooo…
Was already hacked…
Need more lemon pledge…
so… ion generator and subwoofer running nearby to constantly trigger the auto-encrypt/lockdown feature. Eventually, the human trying to use the ultra-secure machine will throw up their hands and use something less secure, then the evil maids can steal the data. Done.
*puts SSD inside padded enclosure*
*kick subwoofer*
+11
I think the idea, at least part of it, is to tell you if someone is trying to get into your hardware.
If you are working with sensitive data, and you know that people are trying to get it, the correct solution is to remove the people who are trying to get in. If you notice a strange subwoofer, or your computer “randomly” wipes itself, time to take some more drastic action.
I’m just going to leave this here: https://xkcd.com/538/
I remember you guys from Austin OSCON. I like your PC features! I always walk away and forget to lock my PC.
evandromiami,
Yes, we where at OSCON. We had good discussions with a lot of people there. Very fruitful.
Thanks for your interest.
Stefan
when wear leveling hits in months you can just throw it away and buy a new one. Also what if I get remote code execution and work up to 0 or -1 execution?
That’s a different problem. This is only physical security. They can’t solve every problem!
@stefan – Would it be possible to purchase an ORWL device with Qubes-Whonix installed? (Or just Qubes)
@Me
Yes, Qubes can be installed on it. It was no harder than Ununtu installation. I do’t see a reason why Whonix installation would be a problem. I am hesitant to commit to too many custom OS installations though, for logistical reasons.
it seems easiest, to go after the weakness of wifi. on the nsa level I’d picture unoffical firmware updates. but as mentioned its weakness is being mass produced. if wifi isnt used or ect but physical access to the device exist. freeze some non conductive device with a large thermal mass clamp onto board to keep mesh intact. reflow letting ssd free from pcb prior to mesh disassembly. with encrypted data its only a matter of time once quantum computing is ready
if your the nsa you probably planted backdoors in every opensource os. by contributing a few 1000 lines of code to fill a bugfix request. or mining existing code for weaknesses. if your a government target, connecting to the internet even worse with wifi. makes owning the device obsolete. Id propose a design change drop the wifi and bluetooth for a 28.8kbps modem and put your 1mb of secret documents in a encrypted 2 gb zip file. the government would have less bandwidth to make a unnoticed intrusion
If I was going to the bother of buying this computer, I wouldn’t connect it to the Internet. Internet’s got way more holes, and attackers, than dodgy CIA “maids”.
That’s if it CAN work without an Internet, almost nothing else does nowadays. My friend bought a Playstation 4 game. Put it in the drive. Wait for 9GB to download before it’ll even fucking play!
This always-Internet thing is making software companies really, really fucking lazy. It’s not good enough. I want the Internet of about 20 years ago back.
What about a regular harddrive + super strong electromagnet….
So… They’re offering to sell me a black-box computer, whose internals I can’t check without bricking it, and they promise me its secure?!
TLAs probably have these guys on their payroll, and the ‘security’ chip is probably the back door.
Russian anti-doping agency, folks.
That sounds very cynical, until you do a bit of research and discover there are historical examples that demonstrate that the point of view is based on more than theory. The SSD is the biggest problem as there is no complete chain of trust from the manufacturer to the assembly plant, and that is assuming the SSD manufacturer has not been “owned”. i.e. They are not in a position to claim that they could know if it is secure or not.
No back door, no Russian agency, just a bunch of guys that like to design computers. We thought of sending it in kits but its not easy to put together. Now, if you are really worried and willing to put it together yourself ping us.
All comments = tldr, so I hope I’m not repeating…
The encryption and security requires a remote device, probably akin to a keychain, so why go to all this trouble? Just make a drive less laptop and use a thumb drive as the hard drive! A cursory search revealed thumb drives as big as its hdd, including ones with built-in keyed encryption. When it’s time to walk away from it, hibernate to the drive and take the drive with you, just as you would the security card. Much more secure, with the only downfall (comparatively) being that it’s not wireless…
Just my quick, obvious observation.
because you need more than the drive to be sure your data are safe. You need to know the BIOS has not been change, that the OS is still the one you think, that no apps or malware has been installed or a WiFi driver changed…
Also, there are two keyfob in the box, what happens if you loose your drive ?
I think you’d need to disguise it too. If someone knows it’s an ORWL, they can be much more careful not to trip it’s countermeasures. Perhaps stick it in an old ThinkPad case so the Evil Maid will bump it and place it into it’s crash mode.
Of course, one hopes you don’t have heavy trucks near your hotel, or the machine might scramble on it’s own.
The motion detect is not triggering when heavy truck is driving. ORWL is detecting when its moving significantly like changing desk or on leaving the room.
The ORWL sucks, cannot connect to network (lacking ethernet port) what rubbish.
In fact you can connect [ORWL] to Ethernet though the USB Type C and a RJ-45. We are keeping the options open to many different user needs by providing USB port.
From my perspective I think an Ethernet port really should be standard internal hardware. If the aim of the device is total security then having the ethernet components internal and vetted to be secure then it removes the possibility of a compromised USB ethernet device being attached.
You have a good point there IMO.
I don’t know shit about security or understand half of what I just read BUT, this was the most entertaining thing I’ve read all day…
Just use a keyboard logger for the user pass code and a RFID relay attack for the keyforb and your are in.
Btw. I guess the LDS have so bad tolerances which means the MAX32550 must have large tolerances for the impedance measurements.