So, erm… good news everyone! A vulnerability has been found in a software library responsible for generating RSA key pairs used in hardware chips manufactured by Infineon Technologies AG. The vulnerability, dubbed ROCA, allows for an attacker, via a Coppersmith’s attack, to compute the private key starting with nothing more than the public key, which pretty much defeats the purpose of asymmetric encryption altogether.
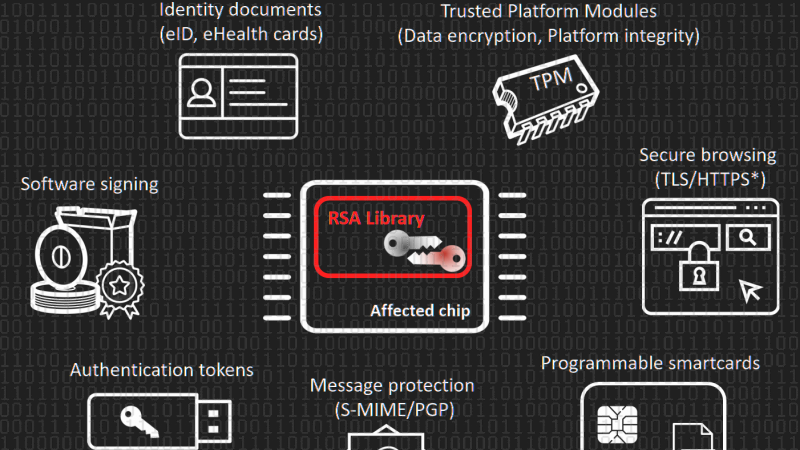
Affected hardware includes cryptographic smart cards, security tokens, and other secure hardware chips produced by Infineon Technologies AG. The library with the vulnerability is also integrated in authentication, signature, and encryption tokens of other vendors and chips used for Trusted Boot of operating systems. Major vendors including Microsoft, Google, HP, Lenovo, and Fujitsu already released software updates and guidelines for mitigation.
The researchers found and analysed vulnerable keys in various domains including electronic citizen documents (750,000 Estonian identity cards), authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP. The currently confirmed number of vulnerable keys found is about 760,000 but could be up to two to three orders of magnitude higher.
Devices dating back to at least 2012 are affected, despite being NIST FIPS 140-2 and CC EAL 5+ certified.. The vulnerable chips were not necessarily sold directly by Infineon Technologies AG, as the chips can be embedded inside devices of other manufacturers.
The difficulty of the factorization attack is not the same for all key lengths and is NOT strictly increasing (some longer keys may take less time to factorize than other shorter ones). The following key length ranges are now considered practically factorizable (time complexity between hours to 1000 CPU years at maximum): 512 to 704 bits, 992 to 1216 bits and 1984 to 2144 bits. Note that 4096-bit RSA key is not practically factorizable now, but may become so, if the attack is improved.
The time complexity and cost for the selected key lengths (Intel E5-2650 v3@3GHz Q2/2014):
Keep in mind that these benchmarks are for a single CPU. For certain three-letter agencies one must assume the attacks take trivial time to complete. Then again, they probably already have your keys (citation needed).
Concerned users can test their public keys online or, maybe a better idea, offline by cloning the following GitHub repository. If using Linux flavors with pip, you can try the following to test your known public keys:
$ sudo pip install roca-detect $ gpg -a --export > /tmp/public && roca-detect /tmp/public 2017-10-17 14:10:33 [7869] INFO ### SUMMARY #################### 2017-10-17 14:10:33 [7869] INFO Records tested: 93 2017-10-17 14:10:33 [7869] INFO .. PEM certs: . . . 0 2017-10-17 14:10:33 [7869] INFO .. DER certs: . . . 0 2017-10-17 14:10:33 [7869] INFO .. RSA key files: . 0 2017-10-17 14:10:33 [7869] INFO .. PGP master keys: 1 2017-10-17 14:10:33 [7869] INFO .. PGP total keys: 102 2017-10-17 14:10:33 [7869] INFO .. SSH keys: . . . 0 2017-10-17 14:10:33 [7869] INFO .. APK keys: . . . 0 2017-10-17 14:10:33 [7869] INFO .. JSON keys: . . . 0 2017-10-17 14:10:33 [7869] INFO .. LDIFF certs: . . 0 2017-10-17 14:10:33 [7869] INFO .. JKS certs: . . . 0 2017-10-17 14:10:33 [7869] INFO .. PKCS7: . . . . . 0 2017-10-17 14:10:33 [7869] INFO No fingerprinted keys found (OK) 2017-10-17 14:10:33 [7869] INFO ################################
In this example, no vulnerable keys were found. Did you find one? If it is yours, it’s probably better to revoke and generate a new one. It seems 2017 keeps on giving us security pearls with each passing day. Yesterday we mourned the death of WPA2, but we’ve also seen SHA-1 broken, the Broadcom WiFi exploit in one billion smartphones (Broadpwn), a Bluetooth vuln that won’t be patched in around 40% of the devices, your credentials being cached in search engines, and we left several from this list.
















“The currently confirmed number of vulnerable keys found is about 760,000 but could be up to two to three orders of magnitude higher.” so between 76,000,000 and 760,000,000. are you sure?
Orders of Magnitude can also be binary,
each increasing order multiplies by 2.
“Orders of Magnitude can also be binary,”
Magnitude is directly related to the base the number is expressed in. In this case it’s base 10.
Possibly also 8 or 9.
Octal? :-)
Am I the only one who read the intro in professor Farnsworth’s voice?
Duh, that’s because he wrote it in professor Farnsworth’s voice.
I actually did. :)
Ha!
Damn it, everything reads in Farnsworth’s voice now!
Imagine when this happens with cryptocurrency wallets…
Gonna have fun figuring it this is affected.
https://www.amazon.com/gp/product/B0085E4WQQ/ref=oh_aui_search_detailpage?ie=UTF8&psc=1
Seems a lot of crypto implementation issues this month… Best I check for infineon TPM chip-sets (others affected? Intel ME?? and the IME equivalent of a TPM???)… dunno what to do about them though other than re-purposing said machines to a non-security computing role.
OK, reread by skimming over the relevant parts… Only Infineon parts affected… still will check those
Guess I won’t bother setting up the TPM in this laptop then… When I got Windows 7 re-installed, there was a utility there for setting it up and I think I set a passphrase on it but never set up anything more than that. Under Linux (primary OS)
tpm_infineonis loaded, but never bothered to look into userland tools to interact with it.I shan’t bother now since the open-source packages I run don’t use it, and don’t suffer the problem. Not sure if Panasonic will be releasing a firmware update for this and I really can’t be stuffed looking.
“Devices dating back to at least 2012 are affected, despite being NIST FIPS 140-2 and CC EAL 5+ certified”
Of course they were, because the NSA probably snuck in, or requested, this “bug”.
Infineon chips were used in GSA approved Department of Defence (DoD) Common Access Cards(CaC) (aka smartcards). This is going to be a problem for the government as well. Would not surprise me if NSA has cards with the issue.
I have a PIV compliant card (Civilian version of the CaC card) from PIVKey (aka Taglio) , vendor says they have to swap out the cards.
“We don’t have confirmation from Infineon, but it seems clear that the SLE78 chip we use is vulnerable.
What makes this situation difficult, is that the card is FIPS and EAL certificated, and specifically the key generation algorithm is certified as well. So I think we will hear more about this from the NIST as well as Infineon.
We will be replacing the C980 with a non-vulnerable card as soon as they are available.
” – Taglio rep
When I test my keys at keychest they are vulnerable. Thankfully I haven’t deployed my smartcard infrastructure yet thats a 2018 project.
If this affects qualified signatures (AFAIK these Estonian ID cards could be used this way) this would be a huge problem. Qualified signature is equal by the law to normal signature and any signed document contains public key. If you have any document signed by someone with such card you could restore his private key and fake signs. On the other side if you have such card – you can denial any responsibility of what you have signed just because you have weak key.
Hope someone uses it to expose Lenovo some more, doing it 3+ times in the most outrageous circumstances apparently wasn’t enough to convince the public nor resellers that you should stay the fuck away from Lenovo..
I bet the ‘reviewers’ will be able to buy a few Teslas from the bribes already, but with some more exposé’s they can buy a mansion with a large garage to go with it.
And despite all these identified security holes in technologies the push for widespread implementation of the IOT (Internet of things) at any cost is still going strong. Why would the industry continue to push IOT after all of these security flaws have been identified unless there are ulterior motives behind such a push? What kind of motive? Sure would be a good way to argue why internet access must be licensed/restricted. Once you implement licensing it becomes a lot easier to restrict that access and thus forcibly regulate individuals behaviors/actions. Just imagine how compliant the public (for the most part) would become if you had to have a license to access/use the internet and you could have that license revoked (maybe even permanently) by some government agency.