If you’ve had the classic engineering education, you probably have a hazy recollection of someone talking about control theory. If you haven’t, you’ve probably at least heard of PID controllers and open loop vs closed loop control. If you don’t know about control theory or even if you just want a refresher, [Brian Douglas] has an excellent set of nearly 50 video lectures that will give you a great introduction to the topic. You can watch the first lecture, below.
You might think that control systems are only useful in electronics when you are trying to control a process like a chemical plant or a temperature. However, control theory shows up in a surprising number of places from filters to oscillators, to the automatic gain control in a receiver. You’ll find the background behind many familiar results inside control theory. Sort of like when you take calculus and you discover how they came up with all the formulas you memorized in geometry.


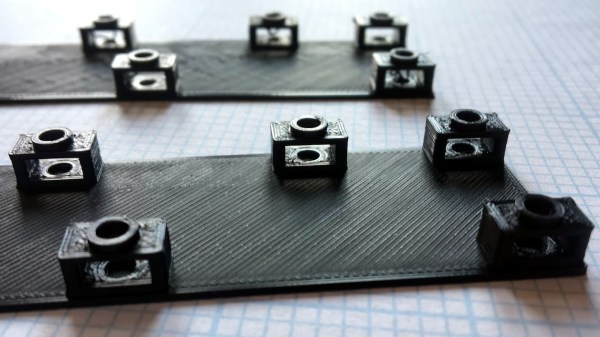
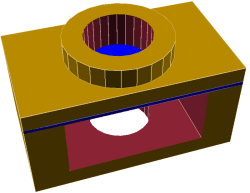 To solve this [Tommy] added what he calls a “sacrificial bridge”, shown as blue in the CAD image. He essentially gives the hole a flat bottom, so that the printer first lays down a thin but solid bridge as a foundation. Then, the portion with the round hole is printed on top of that. With this small design change, the print becomes much more reliable with no support structure required.
To solve this [Tommy] added what he calls a “sacrificial bridge”, shown as blue in the CAD image. He essentially gives the hole a flat bottom, so that the printer first lays down a thin but solid bridge as a foundation. Then, the portion with the round hole is printed on top of that. With this small design change, the print becomes much more reliable with no support structure required.