If you walked into a gym and asked to sniff exercise equipment you would get some mighty strange looks. If you tell hackers you’ve sniffed a Fitbit, you might be asked to give a presentation. [Jiska] and [DanielAW] were not only able to sniff Bluetooth data from a run-of-the-mill Fitbit fitness tracker, they were also able to connect to the hardware with data lines using test points etched right on the board. Their Fitbit sniffing talk at 34C3 can be seen after the break. We appreciate their warning that opening a Fitbit will undoubtedly void your warranty since Fitbits don’t fare so well after the sealed case is cracked. It’s all in the name of science.
There’s some interesting background on how Fitbit generally work. For instance, the Fitbit pairs with your phone which needs to be validated with the cloud server. But once the cloud server sends back authentication credentials they will never change because they’re bound to to the device ID of the Fitbit. This process is vulnerable to replay attacks.
 Data begin sent between the Fitbit and the phone can be encrypted, but there is a live mode that sends the data as plain text. The implementation seemed to be security by obscurity as a new Bluetooth handle is used for this mode. This technique prevents the need to send every encrypted packet to the server for decryption (which would be for every heartbeat packet). So far the fix for this has been the ability to disable live mode. If you have your own Fitbit to play with, sniffing live mode would be a fun place to start.
Data begin sent between the Fitbit and the phone can be encrypted, but there is a live mode that sends the data as plain text. The implementation seemed to be security by obscurity as a new Bluetooth handle is used for this mode. This technique prevents the need to send every encrypted packet to the server for decryption (which would be for every heartbeat packet). So far the fix for this has been the ability to disable live mode. If you have your own Fitbit to play with, sniffing live mode would be a fun place to start.
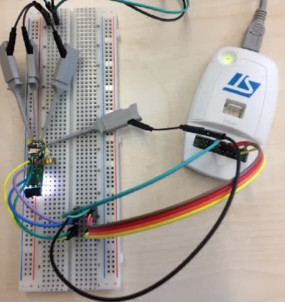
The hardware side of this hack begins by completely removing the PCB from the rubber case. The board is running an STM32 and the team wanted to get deep access by enabling GDB. Unfortunately, the debug pins were only enabled during reset and the stock firmware disables them at startup (as it should). The workaround was to rewrite the firmware so that the necessary GPIO remain active and there’s an interesting approach here. You may remember [Daniel Wegemer] from the Nexmon project that reverse engineered the Nexus 5 WiFi. He leveraged the binary patching he used on Nexmon to patch the Fitbit firmware to enable debugging support. Sneaky!
For more about 34C3 we have a cheatsheet of the first day and for more about Fitbit security, check out this WAV file.















“If you walked into a gym and asked to sniff exercise equipment you would get some mighty strange looks.”
Just tell them you’re from the EPA.
Still not believable with all the budget cuts. Now, the NSA doing something weird and invasive, that’s believable.
Just tell them you’re from the Department of Agriculture.
I keep seeing the STM32 for Bluetooth and mobile accessories. It seems really popular. Why’s that? Power consumption? It’s popularity is making me doubt my choice of nrf51 SoC
It does seem odd to use a separate dumb ble radio; there’s a ton of fully integated BLE chips of course and the ones I’ve worked with appear to be sufficiently low power for a fitness tracker, assuming you have an accelerometer with an motion alarm output so your cpu can be in deep sleep at night time. NRF51 I’ve avoided b/c it’s expensive; I used a Quintic QN9021 (now NXP) – cortex M0, which is very cheap and worked fine
that STM32L15 they used is pretty sweet tho a decent CPU with very very low power; 1.15microamp standby with RTC and pin wakeup, 185microamp/Mhz when running… I’ll be bearing that chip in mind…
Last time I was looking at ultra-low-power microcontrollers, I compared the MSP430’s with the STM32L series, and found the STM32 was just as good or better. It uses more power whilst awake, but doesn’t need to be awake as long, for a net decrease in consumption. That was a surprise!
ARM is ARM is ARM, but there’s a big enough difference between manufacturers for peripherals/debug hardware/support libraries that there’s a strong impetus to stick with the one manufacturer if you’ve already got a time/money/knowledge investment in it.
Also, there’s almost certainly a price component to it – the integrated IC is probably more expensive than the discrete solution per unit, but requires less development time/cost. Depending on the size of the production run/sales, either the per-unit cost or the development NRE’s will dominate.
“Data begin sent” => “Data being sent”
Hi,
thanks for covering our hack :-)
Here are the links mentioned in our talk:
1. Our open source app which allows you to extract your secret key and the firmware
https://github.com/seemoo-lab/fitness-app
2. Our modified version of the Nexmon framework which already contains code to mulitply each step by 100 ;-)
https://github.com/seemoo-lab/fitness-firmware
Also: here is a gif of the demo which we showed in our talk
https://giphy.com/embed/xT1R9Tv5kJgEbV4lvq
Cheers,
Daniel
Could this be the beginning of custom FWs to add/modify functions?
Sure, for example it would also be possible to get access to the raw sensor data of the accelerometer. This should give you values for each X,Y and Z axis :-)
Would be great to make it possible to export data without having to resort to the Fitbit API. The device does keep all the raw data in memory so it’d be lovely to be able to dump it immediately!
Someone could possibly do modifications like turning off Peek function when asleep etc – stuff that the FB devs have been ‘considering’ for years now.
Why do they lock up the hardware at all? I understand why game console makers do – as they make all their money out of games, not the hardware. But fitbit sell just hardware – and if they had a proper access to everything they would sell more hardware! Or is the answer that their models are differentiated by features in the software, so they have to lock them down?
But FitBit isn’t locking its hardware; your data is there, and you can access them in their entirety (I think). And it’s pretty easy to cerate a dev account and get access to it. The problem is, it’s a huge amount of data, so it doesn’t make much sense in getting a simple dump. Instead you must use an app that makes use of it – and that’s where the problem lies: there aren’t any to speak of, save one I had found on Github and a couple of (limited) web services.
You shouldn’t have to “hack” a device to get your own data out of it.
Yeah, that is strange having to hack a device to get the information the device was designed to provide. Way to go team on provisions with details!
The most recent annoying item I purchased and returned was a pair of wireless Motorola FOCUS66-BLK2 Wi-Fi HD Home Monitor Camera – 2 Pack (I had to check my Amazon order as I forgot details) surveillance cameras where you had to use the cloud or their service to acquire the video without a pain in the hack into hack the wireless signals and I think firmware hack also. I forget at the moment if firmware hack was required as I think the software or firmware was a bonus though does seem like I had to figure the addresses… I had to use VLC player, wireshark and hhhmmm… I don’t recall moments from last winter.
I wonder if there are other issues with work around hacks like this? Some say like wireless communications… we are being ripped off every way that can be in almost criminal ways and means by devices that aren’t even required for survival. Figure co-op relay like wall street for those that need communications where we can make them as proprietary as well like and only need PM’s, electricity, licenses and hidden variable funds maybe for upgrades or unplanned maintenance.
For example where we can still have our freedoms with legal rules of course too follow that are not frivolous or unreasonable… If wasn’t for hackers, libraries and forward thinkers providing library style information on the web… like say driving a car and getting repaired by the automotive shop that is corrupt damaging or locking items out charging fraudulent fees… we wouldn’t be able to do what the vehicle was designed for without the auto shops permission to fleece or maybe mafia road block to get to the shop or where-ever even.
Strange how different some of the latest generation is de-sensitized to corrupt malicious operations and almost seems like the valid thinking legal generation is being poached that is more outspoken regarding our Rights being Conspired Against and Deprived Under Color of Law that is prejudice and biased towards armed robbers trying to look official
In case you want to learn more about Nexmon, I recently published my PhD thesis about this topic. Feel free to download and read it: http://nexmon.org/thesis
What about the four connectors on the backside of for example the charge 5? is that usb? At least the charger is and it’s connecting to the two outer ones.