With mass vaccination programmes and careful application of public health measures it almost feels for some of us as though the pandemic is under control. Any thoughts of it being over are illusory though, and if further reminders were needed we have the news that once more this year’s Chaos Communication Congress has been cancelled due to the safety of its attendees and the extra precautions that its organizers would have to undertake.
This event in Leipzig between Christmas and New Year is probably the largest of the European gatherings in our community, and its loss will be a great disappointment. Last year’s cancelled event was replaced by a remote one, we’ll see whether they repeat that feat in 2021. If so, we’ll be there, virtually.
We can only sympathise with our German friends, as while it must be extremely annoying it’s to their credit that they are taking the pandemic seriously. We’re sure that they will be back with the same event in 2022 as the world slowly inches towards normality, and Hackaday will be there to bring you the best of the event.
Somehow we didn’t do a big overview post of the 36C3 in 2019, so if you want to bask in the glory of a Congress, you have to travel back in time all the way to 35C3 in 2018, long before the arrival of COVID-19.
Header image: Yves Sorge, CC BY-SA 2.0.





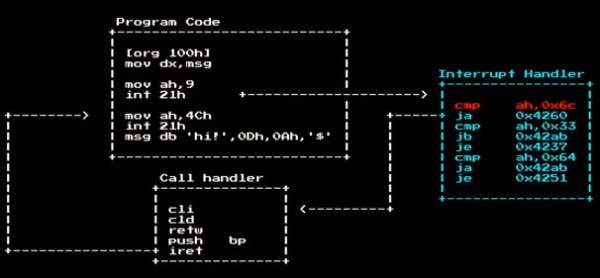


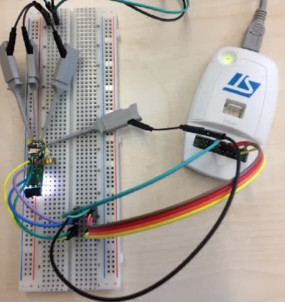 Data begin sent between the Fitbit and the phone can be encrypted, but there is a live mode that sends the data as plain text. The implementation seemed to be security by obscurity as a new Bluetooth handle is used for this mode. This technique prevents the need to send every encrypted packet to the server for decryption (which would be for every heartbeat packet). So far the fix for this has been the ability to disable live mode. If you have your own Fitbit to play with, sniffing live mode would be a fun place to start.
Data begin sent between the Fitbit and the phone can be encrypted, but there is a live mode that sends the data as plain text. The implementation seemed to be security by obscurity as a new Bluetooth handle is used for this mode. This technique prevents the need to send every encrypted packet to the server for decryption (which would be for every heartbeat packet). So far the fix for this has been the ability to disable live mode. If you have your own Fitbit to play with, sniffing live mode would be a fun place to start.








