Google Authenticator is a particularly popular smartphone application that can be used as a token for many two factor authentication (2FA) systems by generating a time-based one time password (referred to as TOTP). With Google Authenticator, the combination of your user name and password along with the single-use code generated by the application allows you to securely authenticate yourself in a way that would be difficult for an attacker to replicate.
That sounds great, but what if you don’t have a smartphone? That’s the situation that [Lady Ada] recently found herself in, and rather than going the easy route and buying a hardware 2FA token that’s compatible with Google Authenticator, she decided to build one herself based on the ESP8266. With the hardware and source documented on her site, the makings of an open source Google Authenticator hardware token are available for anyone who’s interested.
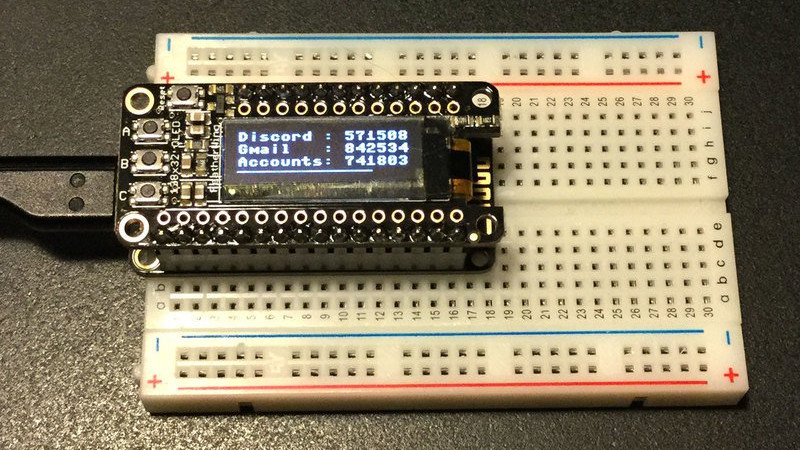
For the hardware, all you need is the ESP8266 and a display. Naturally [Lady Ada] uses her own particular spin on both devices which you can purchase if you want to create an identical device, but the concept will work the same on the generic hardware you’ve probably already got in the parts bin. Software wise, the code is written in CircuitPython, a derivative of MicroPython, which aims to make microcontroller development easier. If you haven’t tried MicroPython before, grab an ESP and give this a roll.
Conceptually, TOTP is relatively simple. You just need to know what time it is, and run an SHA1 hash. The time part is simple enough, as the ESP8266 can connect to the network and get the current time from NTP. The calculation of the TOTP is handled by the Python code once you’ve provided it with the “secret” pulled from the Google Authenticator application. It’s worth noting here that this means your 2FA secrets will be held in clear-text on the ESP8266’s flash, so try not to use this to secure any nuclear launch systems or anything, OK? Then again, if you ever lose it the beauty of 2-factor is you can invalidate the secret and generate a new one.
We’ve covered the ins and outs of 2FA applications before here at Hackaday if you’d like to know more about the concept, in addition to previous efforts to develop a hardware token for Google Authenticator.















How about combine this with usb output. Then you can connect it to a computer, generate auth and enter it with a push on a button. No more enter the numbers manually :)
You would need to use a Teensy since it can emulate a keyboard. Using an Arduino/ESP8266 would be hard.
CNLohr got the esp to emulate a keyboard already
That’s basically a yubikey with its own built-in clock.
It’s already been done check out Onlykey – https://crp.to/p
You must have inspired somebody because it exists now. 2FA-Sidecar (on this site too)
Nice, but much more secure when the token has it’s own RTC, and a protected memory. (And no connection to the outside).
Otherwise, you could as well use a smartphone app.
She does not have a phone.
I use my pebble smartwatch for this. I made my own 2FA app as well (It was my hello World Project on the platform). I am still sad the company is gone :´(
That sounds awesome! Is your code up anywhere public? That sounds like something that would be useful to me.
Also, have you checked out the rebble project? They’re looking to make an open source pebble os replacement.
I don’t know about blkhawk, but my take on TOTP on Pebble is here: https://github.com/al177/twostep .
There are much better apps for Pebble that do the same, but the token code for this one should be easy enough to lift for other projects.
I know :-( I miss pebble, was a great little company. You know what would be cool, is a pebble keychain. Instead of the whole watch, let’s put the actual pebble in a keychain form and then be able to use it for all secondary apps.
Cool! A 2FA TOTP token was my first (and only) app for Pebble as well.
He makes this mistake twice! Certainly destroys his credibility as a writer, considering how prominent Lady Ada and Adafruit are in the hacker community.
None other. No correction needed.
Speech to text with an accent?
Fixed, thanks.
HAD commenters, never failing to pick up on the most critical elements of the post…
I would say the identity of the maker — especially one as esteemed as Limor Fried — is a CRITICAL element of the post.
Maybe she drives a Lada…
I recently found module that has ESP8266, small OLED display, 18650 holder, 4way+push joystick and Li-ion charging circuitry, all on one board sligtly larger than 18650 cell. It costs 12 bucks on eBay, it seems ideal for this purpose.
Any idea if this would facilitate ESP8266 devices connecting to a WPA2 Enterprise network? Bit of a n00b when it comes to network protocols, but have been looking for a solution to get these devices on a 2FA network so students can use them to collect / transmit data. Suggestions?
I’m very new to Arduino’s, and I’m wanting to make a lazy keyboard, using a touchscreen panel I want to be able to scroll through a list of words and phrases and then tap them to have them sent to the computer as a HID device. It appears doable from what I’ve seen and read and examples I’ve seen look good, to have the list of words and phrases on an SD card in a plain text file useful, with different files for different use cases such as ham radio or gaming. I now kind of want to include an Authy clone that I can one click auto complete entering my 2FA keys.
Would this be particularly hard to do?