I recently spent a largely sleepless night at a hotel, and out of equal parts curiosity and boredom, decided to kill some time scanning the guest network to see what my fellow travelers might be up to. As you’d probably expect, I saw a veritable sea of Samsung and Apple devices. But buried among the seemingly endless number of smartphones charging next to their sleeping owners, I found something rather interesting. I was as picking up a number of Amazon-made devices, all of which had port 5555 open.
As a habitual Android tinkerer, this struck me as very odd. Port 5555 is used for Android Debug Bridge (ADB), a development tool used to control and perform various administrative tasks on an Android device over the network or (more commonly) locally over USB. The number of users who would have legitimately needed to enable network ADB on their devices is surely rather low, so to see a half dozen of them on the network at the same time seemed improbable to say the least.
Why would so many devices manufactured by Amazon all have network ADB enabled? I realized there must be a connection, and it didn’t take long to figure it out.
The Seedy World of “Jailbroken” Fire Sticks
The somewhat awkwardly named “Fire TV Stick” is a cheap little device that you stick in the HDMI port of your TV to turn it into a “smart” TV. Ostensibly it allows you to stream content from all the big name providers out there, but realistically Amazon is hoping it will get you to spend more money within their ecosystem. For Amazon, the Fire Stick is to video content as the Kindle is to books: sell the hardware cheap, and make money on the subsequent content purchases.
That was the plan, anyway. But it didn’t take long for people to realize that the Fire Stick was running Amazon’s customized version of Android, and what’s more, was particularly easy to install additional software onto. As you might expect, a huge community of Fire Stick modifications and hacks sprung up in some of the less fashionable parts of the Internet, largely focused on turning the Fire Stick into the ultimate device for illicit video content.
How do you install this software, you might ask? It’s simple, and about a thousand different guides and YouTube videos will walk you through the process of “jailbreaking” your Fire Stick. All you need to do is go into “Developer Options” and enable “Apps from Unknown Sources” and “ADB Debugging”. These handy-dandy guides don’t bother to explain the dangers of doing this, nor do they caution the user to turn off these settings after they’ve installed the third party software of choice (usually Kodi).
The end result is a whole community of people using Amazon Fire TV Sticks in development mode, where anyone can connect to these devices over the network and gain full control over them. A potential botnet, created by willing participants.
Realistic Risk
To be fair, most of these Fire Sticks will never leave the user’s home. In such a situation, while there’s still no good reason to allow remote ADB on these devices, the risk is probably low enough that there’s no great danger to leaving it on. But if you’re using a “jailbroken” Fire Stick on a public network, such as a school dorm or hotel, you’re asking for trouble.
It should be said that the Fire Stick does pop up a message when a device tries to connect over remote ADB. But it’s not a terribly descriptive message, and certainly doesn’t tell the user what this big complicated string of characters means. It doesn’t even say that the connection is coming from a remote device. To add insult to injury, “OK” is the default action when the prompt comes up.
Frankly, it’s a pretty terrible “warning” message for the average user. Granted this message was never intended to show up during normal operation of the Fire Stick (remember, you must first enable “Developer Options” to get to this point), but still. The majority of people will simply press the “OK” button as fast as possible to get this scary Matrix-code off of their TVs so they can get back to watching Netflix.
Once the user hits “OK”, it’s game over. With ADB access approved, an attacker would be free to install and execute their own software, wipe the Fire Stick, or do basically anything else they wanted.
Sniffing for Fire Sticks
If you want to go on the hunt for ADB enabled Fire Sticks, the first thing you need to do is identify Amazon-manufactured devices on the network. There are many ways you could do this, but a quick one-line from a *nix machine with arp-scan installed would look something like: sudo arp-scan --localnet | grep Amazon. This would find the MAC addresses for all the devices on the local network, then pipe that to grep which would search the results for the word “Amazon”.
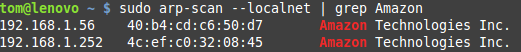 If it’s on the LAN and was made by Amazon, that should get you it’s IP address. The next step would be port scanning each of those IPs. Again there are plenty of ways to do this on different platforms, but
If it’s on the LAN and was made by Amazon, that should get you it’s IP address. The next step would be port scanning each of those IPs. Again there are plenty of ways to do this on different platforms, but nmap is always a good bet. Of course, if it’s only one or two devices you could always just try connecting to them directly with adb connect and seeing what happens.
While tinkering with this concept I’ve come up with a Python script which scans the local network for potentially vulnerable Amazon devices. This script could easily be expanded to actively connect to those devices and execute commands on them (such as rebooting the device), but for obvious reasons I’ll let that be an exercise for the reader.
The Takeaway
This is a perfect example of why you need to be exceptionally cautious when following guides posted online. Whether it’s due to ignorance or indifference, the individuals who create these clickbait “jailbreaking” guides for the Amazon Fire Stick don’t adequately explain the risks of enabling “Developer Options”, and the Fire Stick itself doesn’t do much better in terms of warning the average consumer about allowing remote devices to connect.
It’s also important to remember how sophisticated these “simple” media player devices are becoming. In the case of the Fire Stick, we’re talking about a full fledged computer running Android, and all that entails. It’s not outside the realm of possibility that your Fire Stick could be compromised with a Trojan horse style application, and then become a backdoor into your home network. What seemed like a cheap way to watch streaming movies could end up costing more than you bargained for.
TL;DR: Turn off remote debugging.

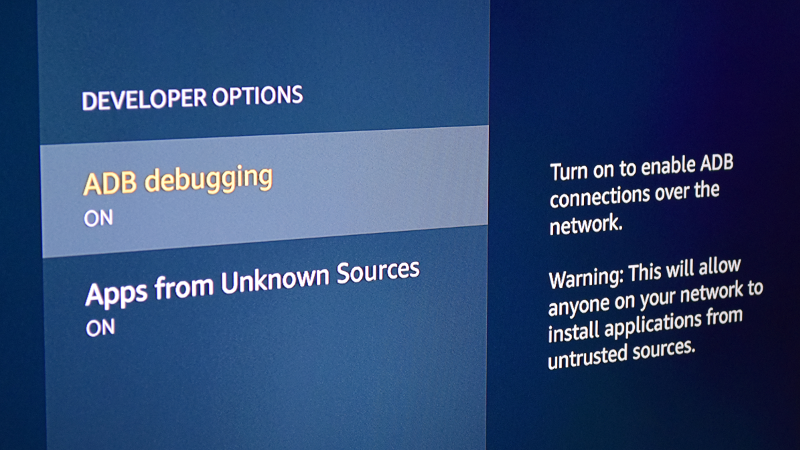
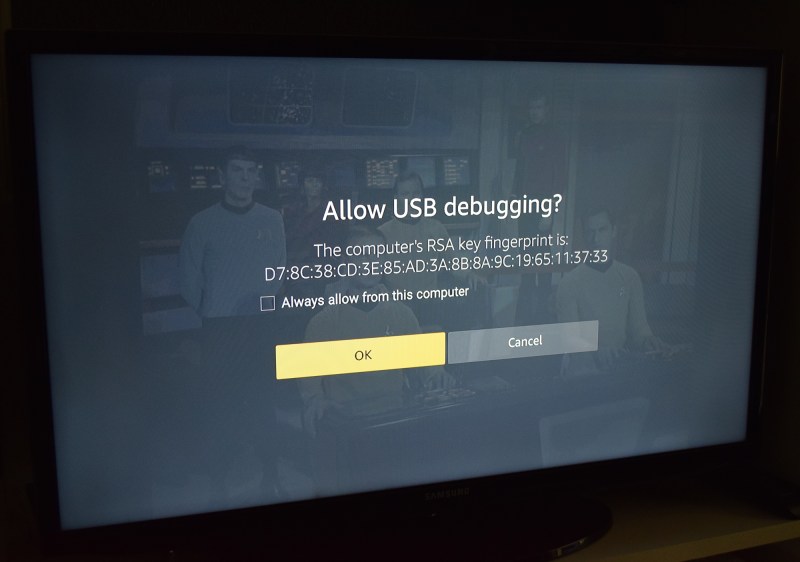














Thanks,
about a year ago a friend was telling me about how he bought a Firestick and installed downloaded software which allows him to watch Netflix, etc.
I wonder if he thought of turning the Developer Options off.
The stock Fire TV Stick allows users to install apps like Netflix, no jailbreaking necessary.
Well, I probably have mis-remembered details, but the article is one I want to share with my friend.
Only apps approved by amazon and available on their app store, the majority of apps are massively outdated and the selection is only a fraction of what’s available on the play store. The only person i know who bothered to jail break an amazon device, did so to install Google play.
No need to be so rude here. Save such behavior for sites like 4chan, please.
Just ignore him (her?).
I think he’s finally giving up: That is, I think (s)he’s the one who has hijacked many of HaD’s followers’ aliases to target mainly Brian Benchoff and to generally cause havok.
Maybe it is someone Brian knows/known personally? someone jealous of him and his colleagues? A school-time roughey?
Maybe his target is someone-else? or just pure anarchy??
With such a gibberish name and without thought or effort as “Bdjdjjxb”, it looks like we just need to ignore such people for at least a year longer.
P.S. I quite agree with what is implied by @Ren… (:D)-}-{ and ¯\_(ツ)_/¯
What if?
It _IS_ Benchoff, under a schizophrenic personality?
(dramatic music, dun, dun, DUN!)
B^)
Carlito ?
“… largely focused on turning the Fire Stick into the ultimate device for illicit video content.”
Aka piracy. Actions have consequences.
Piracy?
Piracy involves killing people on a ship and taking all their stuff. I’m not saying that ip theft is good but I don’t think many movie movie thiefs slit the directors’ throats and dump their bodies in the ocean. Let’s not pander to industry by reinforcing that association.
Everyone knows what you’re talking about when you say digital piracy.
No one thinks you’ve got a belt full of match lock pistols and a boarding axe or a group of AK wielding East Africans in the back of your pickup as you assault the movie studio.
Law enforcement and legislators call it piracy and have for some time, so whether you agree with the definition or not, it’s how the word is commonly used.
> “No one thinks you’ve got a belt full of match lock pistols and a boarding axe or a group of AK wielding East Africans in the back of your pickup as you assault the movie studio.”
That would actually make a pretty good Hollywood scenario.
I Arrrrggggeeee wit’ you, matey!
B^)
Besides, this website features a Jolly Roger (er… Wrencher) in its banner!
Or Monty Python sketch, one of the two.
Pirate walks into bar with a proper ships wheel stuffed down the front of his pants. Bartender says, “Mate, that ship’s wheel looks mighty painful you have there”. Pirate replies, “Aye, it’s Drivin’ me nuts!”
“Law enforcement and legislators call it piracy and have for some time, so whether you agree with the definition or not, it’s how the word is commonly used.”
I’m sure they are tickled that you’re buying in, Leithoa.
Personally, if I’m going to help law enforcement push neurolinguistic programs to help them demonize minor crimes, I’m going to want to get paid cash money! :)
Call it what you want but when someone talks about pirating the latest movie I know they probably didn’t maroon anyone on a sandbar after they got the movie.
I suppose you’re also going to tell be that all the studies showing NLP is complete bunk are also ‘just what THEY want you to think’.
Looking in a 190 year old dictionary http://webstersdictionary1828.com/Dictionary/piracy
“2. The robbing of another by taking his writings.”
Sounds like taking information without permission has been called piracy for a more than a couple of years.
True!
This sounds like a great scene for an updated “Blazing Saddles”. Get ready for the “great Raspberry Pi fight”!
i think the proper term should be unauthorized duplication and distribution
Let’s call it “dezentralized backup copy”.
“You honestly think you’ll be able to rewrite the modern definition of the word by being a pedant about it in internet forums?”
Says a guy on hackaday.
I killed the director of “Batman Begins”, totally justified.
That only stops ignorant pirates.
The smart ones get away and write better online guides.
No, not piracy. Piracy is the act of cracking and distributing the original protected content. Playing that cracked content is receiving of stolen goods.
The FireTV stick hardware is amazing for the form factor and the price, Amazon must be subsidizing it heavily. The AppleTV seems so huge and bloated in comparison.
> “All you need to do is go into “Developer Options” and enable “Apps from Unknown Sources” and “ADB Debugging”. Theses handy-dandy guides don’t bother to explain the dangers of doing this, nor do they caution the user to turn off these settings after they’ve installed the third party software of choice (usually Kodi).”
I, for me, can’t stand this kind of shitty tutorial :
https://www.linux.com/blog/how-install-openvpn-centos-7
-Advise the user to completely disable SELinux without any word about the security issue of this action, nor why it’s needed. You normally just need to add a rule to SELinux for the software you added to make it work and shall never disable SELinux.
In most cases, you don’t even need to add an extra rule for OpenVPN, so basically this tutorial is asking you to remove SELinux for nothing.
-Advise the user to remove your actual firewall (firewalld) for ip-tables without any explanation, probably because the author don’t have a clue how to setup firewalld, while it’s working perfectly.
So, it’s Linux (i.e. open source), have you submitted a paragraph for them to incorporate with the tutorial that warns people of the dangers?
Once upon a time ADB stood for Apple Desktop Bus.
That’s the association my brain does when the TLA “ADB” appears under my goggly eyes – seems I’m getting… outdated?
Well, he did show a picture and explain how to turn it on, and it’s an on/off toggle. I was able to work out the rest on my lonesome.
I have multi tv at both our homes in fla and Illinois . We purchaced the Apple box and q 2 remote systems that fits behind tv . Can I buy just more firesticks for the other TVs that rarely gets use?
Damn. I wonder which one if you is a chubby, hairy dude that likes to cuddle ND play around.
Wtf!
Man, the comments for this one are really a minefield….
Don’t you just hate it when you find out you’ve posted to the wrong site???
B^)
:D You’ll find a few here.. you’re in good company XD
B^)
You don’t even have to buy a firestick, just download kodi onto your laptop and run hdmi cable to tv..
Not having to plug a computer into every TV in your house is precisely the reason devices like the Fire Stick and Chromecast were developed. Given the millions of units both have sold, it seems like a rather popular idea.
And the screen who shows the ADB port is overlaid over a stock Star Trek TOS publicity photo. And I even own a first Gen Chromecast device, but I’ve not had a reason to do something else with it…..
Yeah fix your [any Android device here] that probably still has a old ROM vulnerable to dozens of parser vulnerabilities like all the media parsers accessible without interaction from MMS with only a IMSI or MSISDN..
The fact there aren’t massive mobile botnets is only a testament to how lazy people are..
You don’t really need to ARP scan for a device that broadcasts itself as _amzn-wplay._tcp. via ZeroConf.
If we’re going to go by connection security a lot of people are in for a rude awakening.. Injecting malware in to octet streams even over HSTS TLS is trivial(even banks and casinos are too lazy to do pinning), and even hardened Linux allows a lot in the slim chance there are jails or even half way decently configured SELinux policies.. If adversary has netfilter zero-day(highly likely to be sold by Zerodium) you’re screwed even if you’re running Qubes or Subgraph.. They have kernel exec that defeats even anal-retentive grsec building practices..
Of course this is stuff all the authorities on security don’t bother mentioning on Twitter or hyped up ad-platforms/security-websites.. Vulnerability research is just as dishonest as the anti-virus industry..
If you delete kodi is your firestick still jailbroken. How do u remove a jailbreak from a firestick
I just want to know how well it will run Octoprint!
Can anyone tell me if the Area 51 network is available and how do I apply for it ??
i wasnt able to access some content because of different regions. tried express and pure both work great