Around these parts, seeing a classic laptop or desktop computer get revived with the Raspberry Pi is fairly common. While we’re not ones to turn down a well-executed Pi infusion, we know they can be controversial at times. There’s an impression that such projects are low-effort, and that the combination of old and new tech gains little in the way of usability due to the usability quirks of the Pi itself.
But we think even the most critical in the audience will agree that this build by [Tylinol], which sees the internals of a circa 1993 PowerBook 165c get replaced with that of a 2014 Mac Mini, is something else entirely. For one thing, there’s no question that packing a modern (relatively) desktop computer motherboard into a laptop’s body takes a lot more planning and effort than hot gluing the comparatively tiny Pi into the same space. Plus as an added bonus, anyone who counts themselves among the Cult of Mac will be happy to see the vintage machine retain its Cupertino pedigree.
 So how do you get a Mac Mini inside of a PowerBook? Very carefully. As explained by [Tylinol], the inside of the PowerBook’s case was coated in graphite and conductive enough to be a problem. So after the original hardware was removed, a layer of tape was added to insulate it; though we imagine a suitably thick spray-on coating could be used as well if you don’t have that kind of patience.
So how do you get a Mac Mini inside of a PowerBook? Very carefully. As explained by [Tylinol], the inside of the PowerBook’s case was coated in graphite and conductive enough to be a problem. So after the original hardware was removed, a layer of tape was added to insulate it; though we imagine a suitably thick spray-on coating could be used as well if you don’t have that kind of patience.
Once the case was gutted and insulated, [Tylinol] added new stand-offs to mount the Mac Mini motherboard and hard drive. For anyone wondering, the 2014 model was used because the shape of the board almost perfectly fits around the trackball PCB. A board from a newer Mac could be used, but it would likely mean using an external mouse.
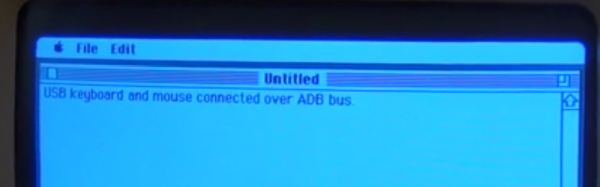
Which would have been a problem for [Tylinol], because one of the main goals of this build was to get the original input working. That meant adapting the Apple Desktop Bus (ADB) devices to USB, which turns out to be something of a Dark Art. But with the help of some contemporary information about the long-forgotten protocol and a Teensy 3.5, both devices are now picked up as standard USB HID.
But of course, that’s just scratching the surface. [Tylinol] also had to figure out how to swap the original display out for a modern panel, and then get the whole thing running on internal battery power. Even if you’re not particularly interested in retro Apple hardware, this is really a phenomenal build that deserves a thorough read-through.
For those of you who don’t mind getting a Pi in a PowerBook, we recently saw a recreation of Lord Nikon’s laptop from Hackers that went that route.