Unless you’re reading this from the middle of the ocean or deep in the forest, it’s a pretty safe bet there’s WiFi packets zipping all around you right now. Capturing them is just a matter of having the right hardware and software, and from there, you can get to work on cracking the key used to encrypt them. While such things can obviously have nefarious connotations, there are certainly legitimate reasons for auditing the strength of the wireless networks in the area.
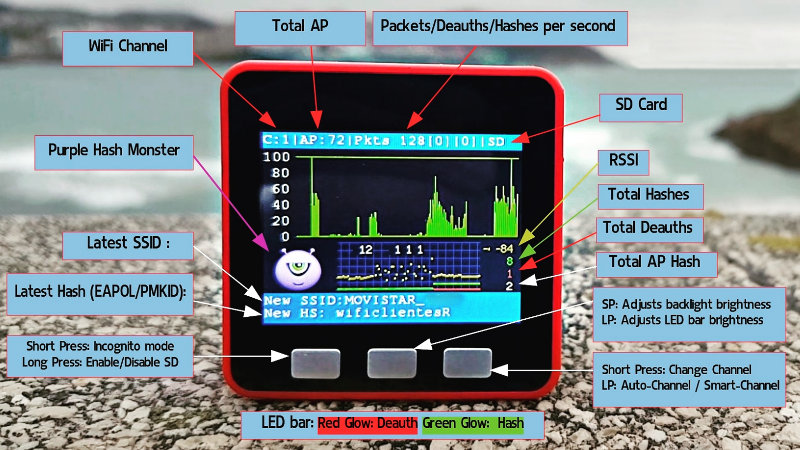
It might not have the computational horsepower to crack any encryption itself, but the ESP32 M5Stack is more than up to the task of capturing WiFi packets if you install the Hash Monster firmware developed by [G4lile0]. Even if you don’t intend on taking things farther, this project makes finding WiFi access points and grabbing their packets a fascinating diversion with the addition of a few graphs and an animated character (the eponymous monster itself) that feeds on all those invisible 1s and 0s in the air.
There’s some excellent documentation floating around that shows you the start to finish process of popping open a WiFi network with the help of Hash Monster, but that’s only the beginning of what’s possible with this gadget. A quick search uncovers a number of software projects that make use of the specific advantages of the M5Stack compared to more traditional ESP32 boards, namely the built-in screen, buttons, and battery. We’ve even seen it used in a few builds here on Hackaday, such as this DIY thermal camera and custom shipboard computer system.
[Thanks to Manuel for the tip.]















This would be great to get going on the LilyGo t-watch 2020
This would be nice to use as a packet sniffer monitored by something like wireshark.
IE
https://www.wireshark.org
Warning this is an invasive bit of software, as it was originally designed for people to monitor local packets on a PC, later was added external device capture.
It would be interesting to be able to follow activity of wireless network(s) in an area. Not to snoop passwords and encryption but just to get how much people broadcast in an area and the behavior of the wireless systems. In general how much noise is going on.
You know things are bad when the network guys break out wireshark.
It looks like it counts Deauth Packets. But are the Deauth Reason Codes displayed? I don’t see them anywhere. Can the deauth reason codes be captured displayed in the first place? This is what I am talking about:
https://community.cisco.com/t5/wireless-mobility-documents/802-11-association-status-802-11-deauth-reason-codes/ta-p/3148055