As cars have become more sophisticated electronically, understanding the CAN bus that forms the backbone of automotive digital systems has become more and more important for hacking cars. Inexpensive microcontroller CAN interfaces have made obtaining the raw CAN bus traffic trivial, but interpreting that traffic can be pretty challenging. In order to more easily visualize CAN traffic, [TJ Bruno] has developed CanoPy, a Python tool for visualizing CAN messages in real time.
A basic PC CAN interface simply dumps the bus’s message traffic into the terminal, while more sophisticated tools organize messages by the address of their intended recipients. Both of these approaches digitally lift the hood and let you examine what your car is thinking, but the wall-of-numbers approach makes finding the patterns that hold the keys to reverse engineering difficult. Automatically plotting the data with CanoPy makes finding correlations much easier, after which the text-based tools can be used to focus in on a few specific addresses.
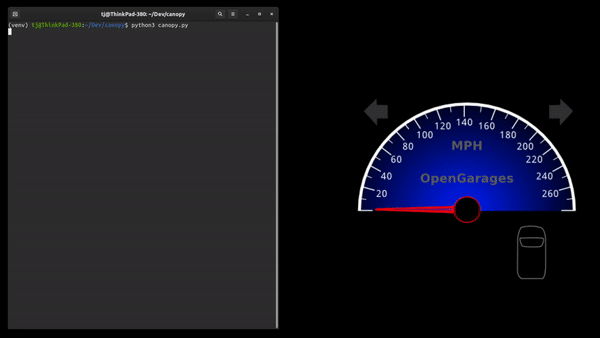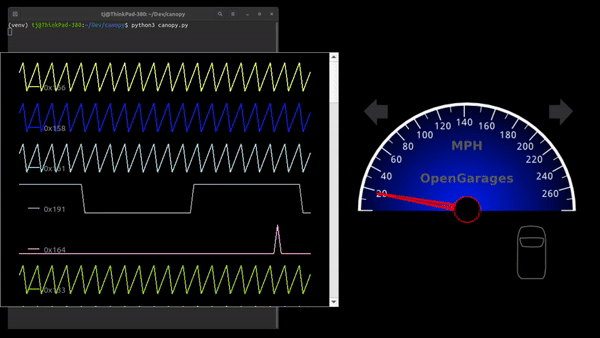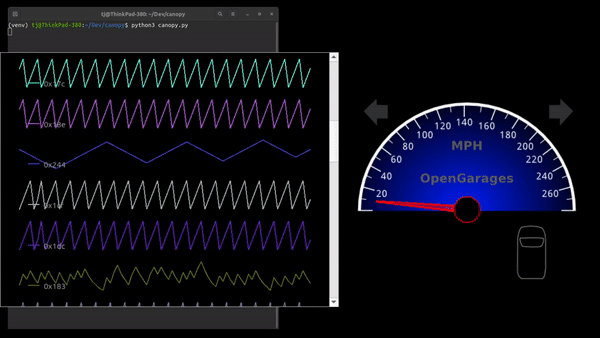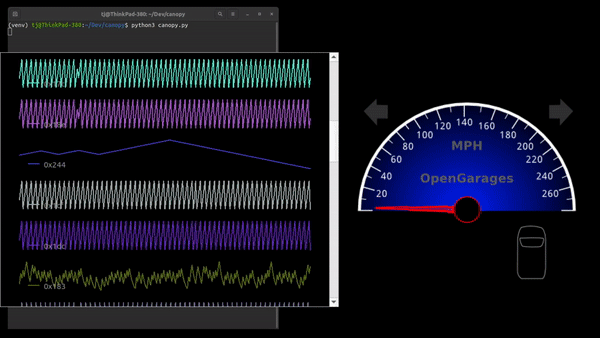
If you’d like to try CanoPy out for yourself, [TJ] has shared it on GitHub. You may also remember [TJ] from his previous guide to hacking CAN with Arduino.















Isn’t one of the problems with OBD-II is encrypted messages?
Not encrypted, but cryptic unless you have the cheat sheet. You might get a “PO457” code, but look it up and it’s “your gas cap is loose”.
But there’s some manufacturer specific codes.
the rabbit hole is much much deeper than that, you also have region differences , year of make and thats just the actual can messages on top of that you have baud differences and recently I came across a software change that also affected the CAN protocol in use.
For cars manufactured in North America just hook to pins 6 and 14 on the OBD II port and have your baud rate set at 500K. If there is a gateway on the car then its less fun but you can still ask it questions with UDS. https://en.wikipedia.org/wiki/Unified_Diagnostic_Services its not that hard. If you have a hard time understanding it read the ISO 14229 spec and plug in a scan tool and watch how the tool talks to the car.
I would like more details on this software changing the CAN protocol… Do you mean changing the baud rate? Or do you mean it went from CAN to CANFD?
In addition to this, there’s often juicy stuff flying over the bus that is completely nonstandard.
For example, individual wheel speeds from the ABS system of a 2009 Outback are passively available over the bus at very high refresh rates, there are no known OBD PIDs for them.
They’re not encrypted but figuring out which messages have which values can be a major headache just due to needle-in-haystack issues.
Some vehicles firewall off the internal buses completely, some with firewalls will still relay messages such that something on the diagnostic port has readonly access.
2007 Toyota Siennas have no firewall – everything flying over a single main bus
2009 Subaru Outbacks have no firewall – everything is flying over a single main bus
2020 Chevy Bolts have multiple buses and a firewall – but a lot of stuff on the main bus is echoed onto the diagnostic bus automatically.
Supposedly some vehicles have firewalls with no echoing requiring you to tap into the buses elsewhere instead of just plugging into the diagnostic connector. I don’t personally own any of these.
Just had fun with LED hyper flash. Learned more about CAN’t bus than I ever wanted to know. That lesson cost about $100.
A long time ago, I captured CAN traffic from my 2002 MINI Cooper’s CAN bus and did some reverse engineering.
Then I make a presentation…
http://bobodyne.com/web-docs/robots/MINI/CAN/Presentation/index.html
It’s not a super great read, but I don’t have a video of the presentation, so hopefully you can get something out of this.
Thanks for that. Really interesting to see a simple but real world example of reverse engineering.
I’ve used some of your work and some other info to start my own dash replacement for those earlier R50/52/53 Minis.
Shame no one did the same for the later R56.. I have a ton of parts from those I’d like to try get working.. if only someone had some logs 🙂
Hi, get your dbc files from GitHub. There’s a pretty good repo, opendbc I think
Has anyone got this to work? I’d really love to be able to use this, but all I get is a blank window with no logs when I run the program. Tried it on two differant computers too (a mac and a windows machine).
I’m using an arduino that’s outputting the CAN data to a serial port, and I can read the serial port and see the raw data just fine.