We’ve all owned something where one tiny detail drives us nuts: a blinding power LED, buttons in the wrong order, or a beep that could wake the dead. This beautifully documented project fixes exactly that kind of annoyance, only this time it’s the climate-controlled seats in a 2020 Ram 1500.
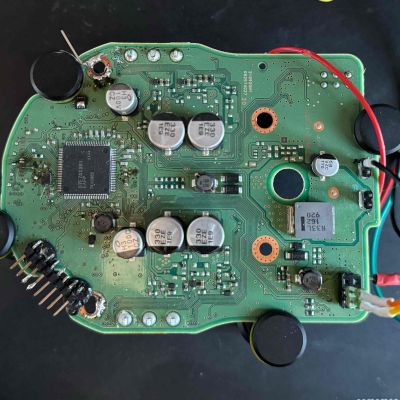
[projectsinmotion] wasn’t satisfied with adjusting seat heating and ventilation only through the truck’s touchscreen. Instead, they added real physical buttons that feel just like factory equipment. The challenge? Modern vehicles control seats through the Body Control Module (BCM) over a mix of CAN and LIN buses. To pull this off, they used an ESP32-S3 board with both CAN and LIN transceivers that sits in the middle and translates button presses into the exact messages the BCM expects.
The ESP32 also listens to the CAN bus so the new physical buttons always match whatever setting was last chosen on the touchscreen, no mismatched states, no surprises. On the mechanical side, there are 3D-printed button bezels that snap into blank switch plates that come out looking completely stock, plus a tidy enclosure for the ESP32 board itself. Wiring is fully reversible: custom adapters plug straight into the factory harness. Every pinout, every connector, and every wire color is documented with WireVis diagrams we’ve covered before, making this an easily repeatable seat-hack should you have a similar vehicle. Big thanks to [Tim] for the tip! Be sure to check out some of our other car hacks turning a mass produced item into one of a kind.