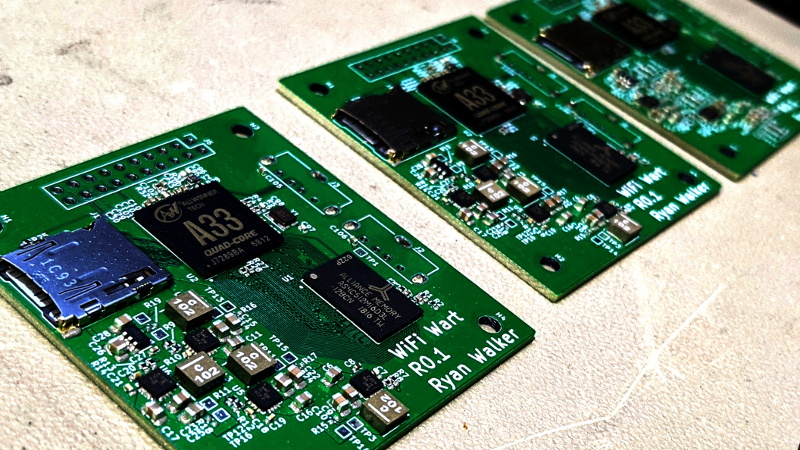
When we last checked in on the WiFiWart, an ambitious project to scratch-build a Linux powered penetration testing drop box small enough to be disguised as a standard phone charger, it was still in the early planning phases. In fact, the whole thing was little more than an idea. But we had a hunch that [Walker] was tenacious enough see the project through to reality, and now less than two months later, we’re happy to report that not only have the first prototype PCBs been assembled, but a community of like minded individuals is being built up around this exciting open source project.
 Now before you get too excited, we should probably say that the prototypes didn’t actually work. Even worse, the precious Magic Smoke was released from the board’s Allwinner A33 ARM SoC when a pin only rated for 2.75 V was inadvertently fed 3.3 V. The culprit? Somehow [Walker] says he mistakenly ordered a 3.3 V regulator even though he had the appropriate 2.5 V model down in the Bill of Materials. A bummer to be sure, but that’s what prototypes are for.
Now before you get too excited, we should probably say that the prototypes didn’t actually work. Even worse, the precious Magic Smoke was released from the board’s Allwinner A33 ARM SoC when a pin only rated for 2.75 V was inadvertently fed 3.3 V. The culprit? Somehow [Walker] says he mistakenly ordered a 3.3 V regulator even though he had the appropriate 2.5 V model down in the Bill of Materials. A bummer to be sure, but that’s what prototypes are for.
Even though [Walker] wasn’t able to fire the board up, the fact that they even got produced shows just how much progress has been made in a relatively short amount of time. A lot of thought went into how the 1 GB DDR3 RAM would get connected to the A33, which includes a brief overview of how you do automatic trace length matching in KiCad. He’s also locked in component selections, such as the RTL8188CUS WiFi module, that were still being contemplated as of our last update.
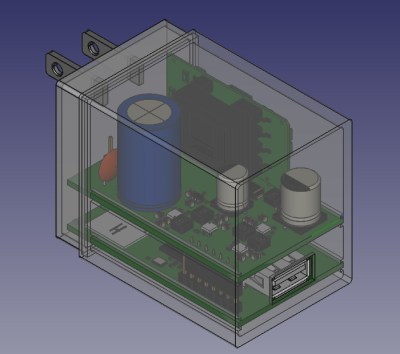
Towards the end of the post, he even discusses the ultimate layout of the board, as the one he’s currently working on is just a functional prototype and would never actually fit inside of a phone charger. It sounds like the plan is to make use of the vertical real estate within the plastic enclosure of the charger, rather than trying to cram everything into a two dimensional design.
Want to get in on the fun, or just stay updated as [Walker] embarks on this epic journey? Perhaps you’d be interested in joining the recently formed Open Source Security Hardware Discord server he’s spun up. Whether you’ve got input on the design, or just want to hang out and watch the WiFiWart get developed, we’re sure he’d be happy to have you stop by.
The first post about this project got quite a response from Hackaday readers, and for good reason. While many in the hacking and making scene only have a passing interest in the security side of things, we all love our little little Linux boards. Especially ones that are being developed in the open.















Nice
It’s curious why people choose such powerful hardware for embedded devices. Unless you are manipulating videos on the fly then a single core is plenty of computing power and there’s certainly little use for having absurd amounts of RAM. Yet without fail, people continue to build beastly embedded systems.
Actually, most of these class of problems come from regular personal cellphones, and or unmodified devices like printers/routers. Thus, there is little hard evidence to use to pin someone in front of a judge.
Personally, I think the FCC should allow active defense measures for malicious interference sources.
I’m sorry, was the objective to get away with committing crimes? If so, maybe the front page of HaD as a poor choice.
Nope, just alluding to old news about the recent failed Lazarus heist:
https://www.bbc.com/news/stories-57520169
Also, a warning that without proof it could be considered defamatory to out business people that pulled these stunts in the past. They already know who they are… ;-)
Lots of RAM makes sense on a system with MTD storage that won’t be getting ANY SWAP EVER.
So which embedded MPU would you recommend that can handle two RTL8188CUS 150Mbit/sec USB 2.0 HS WiFi Modules, process the data in realtime ? And if you are removing Linux kernel which requires a minimum of 2MiB of RAM just to boot and do nothing else, or 100 MiB if you want enough RAM to be able to compile code on the device, what are you replacing it with ?
The A33/is nor common, nor a phone SoC. It was intended for tablets back in the day …
In this (size optimized) projects, I’d favor a pop (expensive) or integrated RAM solution.
AllWinner has the V16 I believe targeted at dashcams which should be just right, with integrated ram.
Also those router SoC’s are interesting, as the combine CPU and WiFi.
I don’t know of a chip that combines both of those however.
Really interested in this project. Even if it never gets to the size of a phone charger (I’m kind of skeptical about that part), I’m always interested in community-developed OSHW Linux boards. Wild what’s possible at the hobbyist level these days.
Even if it doesn’t quite make it down that small, as long as it looks like some kind of wall wart, most folks won’t touch it. I still find 12v warts from old adding machines still plugged into the power strip under a desk that hasn’t actually been powering anything for years.
wifi master/root mode too?
please make a europe 230V version for me ;-) and if it is possible add second usb charge
So, why do people build these? I mean why do they build them and then share with a community of “penetration testers”? Basically boxes of specialty burglary tools are they not? Just curious.
The internal/external good guys install devices like the above to the test security of companies. It would be used as part of the testing process just like any other software or hardware deployed, the results end up in a very long final test report with lots and lots of non-technical summaries and recommended solutions, which are all that really matter.
The device(s) may be configured in a passive monitor mode only (no WiFi RF transmissions at all) to log WiFi traffic packet headers for a hour/day/week/month. And after collection an offline analysis of the harvested metadata may help reveal unexpected patterns within the environment where they were placed.
One alone (or two – primary and secondary) could be used as active device(s) for a hopping server to access, control and monitor other installed hardware during the test(s). How a device like the above gets used really depends on the knowledge of the people using them.
You could simulate the all of the above with a few laptops or desktops with WiFi cards. But getting paid, part of that is putting on a show, making a song and dance and being entertaining. Management expect to be wine dined, and to see a Hollywood style penetration test and not a Z-list simulation of one. In a techies mind the end result will be the exact same report, but one report will have an extra zero or three on the price tag.
So, it isn’t used to find entry points for ransomware? They won’t attract the FBI or a drone attack?
Yes, it’s used to find entry points for ransomware – and companies will pay people to find those entry points for them. Do some googling on penetration testing. In short, the consensus among big companies is that the best defense against criminals is to make the crime tools as widely available as possible and constantly test to make sure everything is protected against them. This is why you can easily buy lock picks, USB rubber duckies, Windows password workaround software, and other such tools. Kali Linux even puts a lot of this stuff into one neat Linux distribution. Ideally, all of this is useless to a criminal because companies have the exact same stuff and have already tried hacking themselves a million times.