If you’ve ever read up on the basics of cryptography, you’ll be aware of steganography, the practice of hiding something inside something else. It’s a process that works with digital photographs and is the subject of an article by [Aryan Ebrahimpour]. It describes the process at a high level that’s easy to understand for non-maths-wizards. We’re sure Hackaday readers have plenty of their own ideas after reading it.
The process relies on the eye’s inability to see small changes at the LSB level to each pixel. In short, small changes in colour or brightness across an image are imperceptible to the naked eye but readable from the raw file with no problems. Thus the bits of a smaller bitmap can be placed in the LSB of each byte in a larger one, and the viewer is none the wiser.
We’re guessing that the increased noise in the image data would be detectable through mathematical analysis, but this should be enough to provide some fun. If you’d like a closer look, there’s even some code to play with. Meanwhile as we’re on the topic, this isn’t the first time Hackaday have touched on steganography.

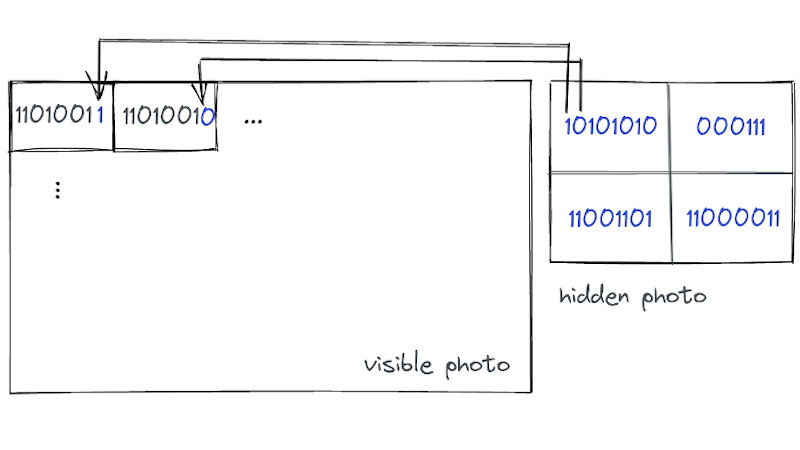














Unfortunately, this particular steganography won’t survive exposure of the method. This method messes with the final bits of each byte. Once you know that, it’s trivial to run statistics on the final bits of each byte of a suspected photo, and immediately spot when they look statistically funny from regular unmodified photos.
A truly cryptographically-secure system is supposed to work even if the adversary knows how it works.
Using only the final bit to encode the data is useful for the purpose of teaching.
Once you understand the concept, it’s not much of a leap to apply an additional algorithm on top to “randomise” the position of each encoding bit.
This obvious flaw of this simple example is explained in detail at 01:02 in the attached video.
There is no attached video. The first link is to his blog, the second to his git hub, and the third is to a different article on hackaday.
It still hides an invisible picture in a picture. The mathy section is a complicated way to say “use the least significant bit for the data” and for 8 bit pixels, a 24Mpixel image can hide a 3Mpixel image. 9Mpixel if the “pixels” are RGB. The write-up looks like a presentation to a math or computer science class. I wonder if you can see a ghost image in a section of sky or other flat region.
yes you can!
“the eye’s inability to see small changes at the LSB level to each pixel. In short, small changes in colour or brightness across an image are imperceptible to the naked eye”
is false as soon as the original image has flat colour areas or smooth gradients. the brain and eyes are pretty good at picking up even the slightest contrast in these conditions.
If you think about it, why would we use those bits if they were imperceptible in the first place. Ultimately that’s exactly what compression does (except in a smarter way) – remove the bits that we don’t see. jpeg is completely based on perception. of course professional photography uses up to 16bit per channel where you could hide much more information without it being visible
You can put encrypted archive files inside images.
Depends on how you transmit the data. Over the internet it’s not worth much, carrying it over a border on your phone, if customs just flips through your “innocent” photos, it would work. If someone only inspects the data with human eyeballs it is a secure method.
If customs notices that all your photos are in PNG format then you’ll be answering some questions in the back room.
Have a problem with me preferring non lossy compression methods?
A quick search for ‘JPEG steganography’ reveals this very good write-up and intro to both steganography and steganalysis:
https://www.medwinpublishers.com/IJFSC/jpeg-steganography-hiding-in-plain-sight.pdf
Surely just save as PNG or even still GIF and hide images within the layers.
Not so fast. Grab a picture with less than ideal lighting conditions as the storage, and encrypt the secret image before embedding. Even if you run statistics on the storage image it’s not possible to tell with a great degree of certainty that something was embedded on it, as the original was full of noise, and properly encrypted data looks very much like noise.
The results will depend entirely on two premises: the original image cannot contain large areas of uniform color, and the image cannot be found online before the embedding. Images with bad lighting or very high ISO are great for that, because the uniform areas will display noticeable noise even without embedding anything. But if the picture can be found with and without the data embedded, it’s trivial to extract the embedded data.
But if the image is properly encrypted, even if you can tell with certainty that you extracted embedded data from it, you cannot tell if the data is a picture, an audio file, an executable or plaintext without the key.
Stegosaurus
Another introduction:
https://www.youtube.com/watch?v=TWEXCYQKyDc
I think there’s an eastern egg in MatLab that does something similar as well. Pretty cool concept
Are there any western eggs, though, for full global egg-coverage?
I wrote something similar to this in MatLab in about 2003, specifically because it handles structured files so nicely: you can open a jpg as an object and it’ll build you a kinda struct thing that has all the metadata held in chunks and all the rgb data in sub-arrays, with each individual color held in one dimension of a multidimensional array.
I know Octave reimplements much of what MatLab does but don’t know if it has image type parsing capability.
But matlab sure made it easy to xor in a plaintext message to the lsb of the rgb data.
how hide sms in sms ?
search program ‘patrz’
Howabout you get really, really cunning, like Baldrick level, and write a chatty letter in normal pen, then get a UV pen and write “Nothing to see here LOL!” with that, and then write the secret note with lemon juice.
I did that lemon juice trick when I was a kid, got impatient for it to dry, and the light bulb imploded when I touched the wet paper to it. It left an emotional scar, fortunately, no physical scars!
You compressed that bulb and embedded it in the letter.
This only works with lossless compression. So it’s pretty much useless today as only a Jpeg is unsuspicious.
And by the way, it also works with audio-files.
It’s not true that it only works for lossless, you can hide data in the frequency matrix after the DCT/Quantisation step. You just can’t stir it in the pixel data since lost images don’t have pixel data.
You can hide it in the macroblock offsets, since that is compressed with a lossless algorithm.
You would not want to use this method in the real world, but it’s useful to demonstrate the general concept.
Regarding JPEG files: Over 20 years ago I stumbled over a paper named “F5 – A Steganographic Algorithm” published by Andreas Westfeld, which presents an algorithm that does a far better job than the method presented here.
Link: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.115.3651
Steganography/watermarking methods strongly depend on the use case and are generally not fit for many scenarios.
To choose a method, we need to reply to a few questions :
– How much data do I need to store?
– Which attack does it need to resist? (jpg compression, crop, rotation, relighting filters,…)
– Is it a problem if an opponent detect/erase its existence even if he can not decode it?
– Does the opponent know the algorithm used?
– Do we have the original document to help the decoding?
LSB is good to store a lot of data with very low noise on the image, but do not protect well the hidden data (easily extracted or removed by a spy).
Pre-encrypting the data with a secret key prevents a spy to decypher it but he can still remove it (as well as any image editing or compression). It’s good to use to leak documents secretely for example because we control the transmission and can make it without degradation.
On contrary, for scenarios such as traitor tracing (identify a leaker by inserting a unique id in each copy of a document), we need a method with high resistance to attacks because we want to prevent people to remove it but we don’t need to store a lot of data and we have the original to help the decoding. Methods based on fourier or wavelet transform may be good for this case.
For jpg compression resistance specifically, some methods use the same tiling and frequency encoding to maximize the resistance.
There are hundred of methods existing with different set of properties that will fit well or not some scenarios.
Some people who sell images online add a barely visible watermark that embeds the user’s name to the images. This discourages people from sharing the pictures, or forces them to ruin the image in attempts to remove the watermark.
If the intent is to identify a traitor without them knowing it, a more resilient method is to make subtle alterations to the image in select locations, like adding an extra flower to a vase, or changing the color of a shirt button. The combination of possible variations then adds up to a simple binary code that can be assigned to each suspect. As long as each suspect has access only to their own copy, they cannot detect the presence of the code because there is nothing extra going on with the image data.
The latter method was used to detect leaked documents by adding typographical errors to the text, adding extra spaces, changing paragraph indentation, etc.
I have a few pictures that have an archive appended. So if you change the file extension on the image it becomes a file container, add your files then put the extension back. It’s pretty obvious something is amiss if you use a small picture and big files, but a big picture and small files and nobody would notice
Imagine the James Webb telescope takes a picture of deep space, the stars and galaxies arranged in a funny little pattern that catches your eye. You go to analyze the image, and naturally embedded inside the image is the code that creates an audio file seemingly native to the picture itself…..do you listen to it
Heck Yes! Just have too… Regardless of the disaster lurking… Press PLAY
This is a method I also use (Alongside many others) and for hiding things from general adversaries this can work, but it doesn’t hold up against those who know what to look out for. From the perspective of any authority a JPEG file that contains valid PKZIP headers (Just grep!) would be immediately suspicious, and if the data’s encrypted you might be having some uncomfortable discussions in small, windowless rooms!
BUT: If you’re using a format that supports plausible deniability (e.g: Nothing to grep for) and you’re in the habit of erasing drives with randomised garbage you might be able to keep it under the radar. That’s a definite “Might” though, and won’t protect your data from enforced erasure of the device…
Modern data policing is a surprisingly thorough process, and it’s for this reason I never carry drives bigger than 4GB when travelling internationally (Bigger devices = More time waiting at Customs) and always make sure they’re cleared of anything except what I actually need during the trip. Using throwable passwords for encryption also means not having to give away anything you wouldn’t normally want to (Some countries have key disclosure laws) and the simplest rule is to make sure you’re only carrying things you don’t mind customs officials having access to in the first place. :-)
Nothing at all wrong with encrypting your work documents (They’re commercially sensitive), your music/movie library (That’s reasonable protection of copyrighted material), or anything containing peoples personal information (Thank you GDPR!)…But do remember that most countries give their officials the right of access to anything that’s inbound, and “But that’s private!” doesn’t turn your BitLocker volume into a diplomatic bag! :-)